
Understanding and Working Computer keyboard
Understanding and how to work Computer keyboard - Basically the computer consists of Hardware, software, and brain ware. All three are necessary for a computer to operate properly. As for one of the important hardware of a computer that is keyboard.Keyboard is an input tool used to type information into a computer and run various instructions or commands into a computer. Keyboard in Indonesian means finger board or keyboard.The keyboard is a standard input tool that must exist on every computer. The keyboard is connected to a computer using a cable available on the keyboard. The end of the cable is inserted into the port on the computer's CPU.How to Work Computer KeyboardA keyboard is like a miniature computer. The keyboard has its own processor and circuit circuitry that carries information to and from the processor. The largest part of the keyboard series is "key matrix"."Key matrix" is a circuit grating under the keyboard keys. Inside the keyboard, each circuit is disconnected (like a switch) at a point below each key. When we press a button, the button presses a switch, making the circuit connected and the electric current passes through it. If we long press on the button, the processor recognizes it by pressing the button repeatedly ..
When the processor finds a closed circuit (connected because of keystrokes), then the processor will compare the location of the closed circuit with the character map stored in the ROM (read only memory) keyboard.
The character map is basically a table of characters that lists the positions of each key or a combination of keys and the characters they represent.
For example, a character map tells the processor that pressing the "a" button alone produces a lowercase "a", but the Shift key along with the "a" button together will produce a capital letter.
The character map is basically a table of characters that lists the positions of each key or a combination of keys and the characters they represent.
For example, a character map tells the processor that pressing the "a" button alone produces a lowercase "a", but the Shift key along with the "a" button together will produce a capital letter.
In a computer program and a hand phone in ROM only stores raw data, while RAM stores data that is processed and cooked into an information that can be used and used by users both in the form of games or military projects.
Keyboard Types Based on Connector (Port) - Keyboard is an input tool used to type information into a computer and run various instructions or commands into the computer. Actually the development of the keyboard is not rapid.However that does not mean nothing has changed from the keyboard of the old days until now. Like the connector on the keyboard itself, ranging from Serial, PS / 2, USB, and some even do not use the cable but wireless. For more details, you can understand a little explanation below.
Keyboard Types Based on the Connector1. Serial KeyboardKeyboard this type is usually used for computer type AT. Because the type of connector on this keyboard is a serial connector, then to connect it with the computer must be inserted into the serial port.
 2. Keyboard PS / 2
2. Keyboard PS / 2

The PS / 2 keyboard is a keyboard connected to the computer using the PS / 2 port. Usually used on ATX computers and still commonly used in older computers. Installation of this type of keyboard must be implemented carefully, because the port is the same as the port for the mouse.3. USB KeyboardThe latest computer today has many who use a type of USB connector that ensures faster data transfers, other than that how to install it more easily.
 4. Wireless KeyboardAs the name implies, this type of keyboard does not use a cable as a media liaison between the keyboard with the computer. Type of connection used is infra red, wi fi or blue tooth. To connect the keyboard with a computer, it takes the transmitter and receiver unit. The transmitter unit is usually present on the keyboard itself, while the receiver is usually installed on a USB or serial port on the CPU.
4. Wireless KeyboardAs the name implies, this type of keyboard does not use a cable as a media liaison between the keyboard with the computer. Type of connection used is infra red, wi fi or blue tooth. To connect the keyboard with a computer, it takes the transmitter and receiver unit. The transmitter unit is usually present on the keyboard itself, while the receiver is usually installed on a USB or serial port on the CPU.

X . I
 When you look at all the extras and options that are available for
new computer keyboards, it can be hard to believe that their original
design came from mechanical typewriters that didn't even use
electricity. Now, you can buy ergonomic keyboards that bear little
resemblance to flat, rectangular models with ordinary square keys. Some
flashier models light up, roll up or fold up, and others offer options
for programming your own commands and shortcuts.
When you look at all the extras and options that are available for
new computer keyboards, it can be hard to believe that their original
design came from mechanical typewriters that didn't even use
electricity. Now, you can buy ergonomic keyboards that bear little
resemblance to flat, rectangular models with ordinary square keys. Some
flashier models light up, roll up or fold up, and others offer options
for programming your own commands and shortcuts.
But no matter how many bells and whistles they offer, most keyboards operate using similar technology. They use switches and circuits to translate a person's keystrokes into a signal a computer can understand. In this article we will explore keyboard technology along with different key layouts, options and designs.

A keyboard's primary function is to act as an input device.
Using a keyboard, a person can type a document, use keystroke
shortcuts, access menus, play games and perform a variety of other
tasks. Keyboards can have different keys depending on the manufacturer,
the operating system they're designed for, and whether they are attached to a desktop computer or part of a laptop. But for the most part, these keys, also called keycaps,
are the same size and shape from keyboard to keyboard. They're also
placed at a similar distance from one another in a similar pattern, no
matter what language or alphabet the keys represent.
Most keyboards have between 80 and 110 keys, including:
The typing keys include the letters of the alphabet, generally laid out in the same pattern used for typewriters. According to legend, this layout, known as QWERTY
for its first six letters, helped keep mechanical typewriters' metal
arms from colliding and jamming as people typed. Some people question
this story -- whether it's true or not, the QWERTY pattern had long been
a standard by the time computer keyboards came around.
Keyboards can also use a variety of other typing key arrangements. The most widely known is Dvorak, named for its creator, August Dvorak. The Dvorak layout places all of the vowels on the left side of the keyboard and the most common consonants on the right. The most commonly used letters are all found along the home row. The home row is the main row where you place your fingers when you begin typing. People who prefer the Dvorak layout say it increases their typing speed and reduces fatigue. Other layouts include ABCDE, XPeRT, QWERTZ and AZERTY. Each is named for the first keys in the pattern. The QWERTZ and AZERTY arrangements are commonly used in Europe.
The numeric keypad is a more recent addition to the computer keyboard. As the use of computers in business environments increased, so did the need for speedy data entry. Since a large part of the data was numbers, a set of 17 keys, arranged in the same configuration found on adding machines and calculators, was added to the keyboard.
 In 1986, IBM further extended the basic keyboard with the addition of function and control keys. Applications and operating systems can assign specific commands to the function keys. Control keys provide cursor and screen control. Four arrow keys arranged in an inverted T formation between the typing keys and numeric keypad move the cursor on the screen in small increments.
In 1986, IBM further extended the basic keyboard with the addition of function and control keys. Applications and operating systems can assign specific commands to the function keys. Control keys provide cursor and screen control. Four arrow keys arranged in an inverted T formation between the typing keys and numeric keypad move the cursor on the screen in small increments.
Other common control keys include:
The Windows keyboard adds some extra control keys: two Windows or Start keys, and an Application key. Apple keyboards, on the other hand, have Command (also known as "Apple") keys. A keyboard developed for Linux users features Linux-specific hot keys, including one marked with "Tux" the penguin -- the Linux logo/mascot.
 A keyboard is a lot like a miniature computer. It has its own
processor and circuitry that carries information to and from that
processor. A large part of this circuitry makes up the key matrix.
A keyboard is a lot like a miniature computer. It has its own
processor and circuitry that carries information to and from that
processor. A large part of this circuitry makes up the key matrix.
The key matrix is a grid of circuits underneath the keys. In all keyboards (except for capacitive models, which we'll discuss in the next section), each circuit is broken at a point below each key. When you press a key, it presses a switch, completing the circuit and allowing a tiny amount of current to flow through. The mechanical action of the switch causes some vibration, called bounce, which the processor filters out. If you press and hold a key, the processor recognizes it as the equivalent of pressing a key repeatedly.
 A computer can also use separate character maps, overriding the
one found in the keyboard. This can be useful if a person is typing in a
language that uses letters that don't have English equivalents on a
keyboard with English letters. People can also set their computers to
interpret their keystrokes as though they were typing on a Dvorak
keyboard even though their actual keys are arranged in a QWERTY layout.
In addition, operating systems and applications have keyboard accessibility settings that let people change their keyboard's behavior to adapt to disabilities.
A computer can also use separate character maps, overriding the
one found in the keyboard. This can be useful if a person is typing in a
language that uses letters that don't have English equivalents on a
keyboard with English letters. People can also set their computers to
interpret their keystrokes as though they were typing on a Dvorak
keyboard even though their actual keys are arranged in a QWERTY layout.
In addition, operating systems and applications have keyboard accessibility settings that let people change their keyboard's behavior to adapt to disabilities.
 Keyboards use a variety of switch technologies. Capacitive
switches are considered to be non-mechanical because they do not
physically complete a circuit like most other keyboard technologies.
Instead, current constantly flows through all parts of the key matrix.
Each key is spring-loaded and has a tiny plate attached to the bottom of
it. When you press a key, it moves this plate closer to the plate below
it. As the two plates move closer together, the amount of current
flowing through the matrix changes. The processor detects the change and
interprets it as a key press for that location. Capacitive switch
keyboards are expensive, but they have a longer life than any other
keyboard. Also, they do not have problems with bounce since the two
surfaces never come into actual contact.
Keyboards use a variety of switch technologies. Capacitive
switches are considered to be non-mechanical because they do not
physically complete a circuit like most other keyboard technologies.
Instead, current constantly flows through all parts of the key matrix.
Each key is spring-loaded and has a tiny plate attached to the bottom of
it. When you press a key, it moves this plate closer to the plate below
it. As the two plates move closer together, the amount of current
flowing through the matrix changes. The processor detects the change and
interprets it as a key press for that location. Capacitive switch
keyboards are expensive, but they have a longer life than any other
keyboard. Also, they do not have problems with bounce since the two
surfaces never come into actual contact.
All of the other types of switches used in keyboards are mechanical in nature. Each provides a different level of audible and tactile response -- the sounds and sensations that typing creates. Mechanical key switches include:
 Rubber dome switches are very common. They use small,
flexible rubber domes, each with a hard carbon center. When you press a
key, a plunger on the bottom of the key pushes down against the dome,
and the carbon center presses against a hard, flat surface beneath the
key matrix. As long as the key is held, the carbon center completes the
circuit. When the key is released, the rubber dome springs back to its
original shape, forcing the key back up to its at-rest position. Rubber
dome switch keyboards are inexpensive, have pretty good tactile response
and are fairly resistant to spills and corrosion because of the rubber
layer covering the key matrix.
Rubber dome switches are very common. They use small,
flexible rubber domes, each with a hard carbon center. When you press a
key, a plunger on the bottom of the key pushes down against the dome,
and the carbon center presses against a hard, flat surface beneath the
key matrix. As long as the key is held, the carbon center completes the
circuit. When the key is released, the rubber dome springs back to its
original shape, forcing the key back up to its at-rest position. Rubber
dome switch keyboards are inexpensive, have pretty good tactile response
and are fairly resistant to spills and corrosion because of the rubber
layer covering the key matrix.
Rather than having a switch for each key, membrane keyboards use a continuous membrane that stretches from one end to another. A pattern printed in the membrane completes the circuit when you press a key. Some membrane keyboards use a flat surface printed with representations of each key rather than keycaps. Membrane keyboards don't have good tactile response, and without additional mechanical components they don't make the clicking sound that some people like to hear when they're typing. However, they're generally inexpensive to make.
Metal contact and foam element keyboards are increasingly less common. Metal contact switches simply have a spring-loaded key with a strip of metal on the bottom of the plunger. When the key is pressed, the metal strip connects the two parts of the circuit. The foam element switch is basically the same design but with a small piece of spongy foam between the bottom of the plunger and the metal strip, providing a better tactile response. Both technologies have good tactile response, make satisfyingly audible "clicks," and are inexpensive to produce. The problem is that the contacts tend to wear out or corrode faster than on keyboards that use other technologies. Also, there is no barrier that prevents dust or liquids from coming in direct contact with the circuitry of the key matrix.
Different manufacturers have used these standard technologies, and a few others, to create a wide range of non-traditional keyboards. We'll take a look at some of these non-traditional keyboards in the next section.

A lot of modifications to the traditional keyboard design are an
attempt to make them safer or easier to use. For example, some people
have associated increased keyboard use with repetitive stress injuries like carpal tunnel syndrome, although scientific studies have produced conflicting results. Ergonomic
keyboard designs are intended to keep a person's hands in a more
natural position while typing in an attempt to prevent injuries. While
these keyboards can certainly keep people from holding their hands in a
"praying mantis" position, studies disagree on whether they actually
prevent injury.
The simplest ergonomic keyboards look like traditional keyboards that have been divided down the middle, keeping a person's hands farther apart and aligning the wrists with the forearms. More complex designs place the two halves of the keyboard at varying angles to one another and to the surface on which the keyboard rests. Some go even further, placing the two halves of the keyboard on the armrests of chairs or making them completely perpendicular to the desk surface. Others, like the Datahand, don't look much like keyboards at all.

Some modifications, while not necessarily ergonomic, are designed
to make keyboards more portable, more versatile or just cooler:

With the exception of the Virtual Laser Keyboard, which has its
own sensing system, each of these keyboards uses the same type of
technology as traditional models do to communicate with the computer.
We'll look at that technology next.
 As you type, the processor in the keyboard analyzes the key matrix
and determines what characters to send to the computer. It maintains
these characters in its memory buffer and then sends the data.
As you type, the processor in the keyboard analyzes the key matrix
and determines what characters to send to the computer. It maintains
these characters in its memory buffer and then sends the data.
Many keyboards connect to the computer through a cable with a PS/2 or USB (Universal Serial Bus) connector. Laptops use internal connectors. Regardless of which type of connector is used, the cable must carry power to the keyboard, and it must carry signals from the keyboard back to the computer.

 Whether it's through a cable or wireless, the signal from the keyboard is monitored by the computer's keyboard controller.
This is an integrated circuit (IC) that processes all of the data that
comes from the keyboard and forwards it to the operating system. When
the operating system (OS) is notified that there is data from the keyboard, it checks to see if the keyboard data is a system level command. A good example of this is Ctrl-Alt-Delete on a Windows computer, which reboots the system. Then, the OS passes the keyboard data on to the current application.
Whether it's through a cable or wireless, the signal from the keyboard is monitored by the computer's keyboard controller.
This is an integrated circuit (IC) that processes all of the data that
comes from the keyboard and forwards it to the operating system. When
the operating system (OS) is notified that there is data from the keyboard, it checks to see if the keyboard data is a system level command. A good example of this is Ctrl-Alt-Delete on a Windows computer, which reboots the system. Then, the OS passes the keyboard data on to the current application.
The application determines whether the keyboard data is a command, like Alt-f, which opens the File menu in a Windows application. If the data is not a command, the application accepts it as content, which can be anything from typing a document to entering a URL to performing a calculation. If the current application does not accept keyboard data, it simply ignores the information. This whole process, from pressing the key to entering content into an application, happens almost instantaneously.

In September 2007, an Australia-based company called Fairlight
introduced a new digital audio production device named Xynergi. Gadget blogs covered the story and called Xynergi a $28,000 keyboard. Such labels are misleading. In reality, identifying Xynergi as a $28,000 keyboard is like saying the audio system inside a Bentley is a $250,000 radio -- it misses the big picture.
The Xynergi keyboard is part of a desktop media production center package. Fairlight designed Xynergi to meet the needs of small, professional media editing studios. With Xynergi, engineers can capture audio, manipulate individual tracks, add effects, mix multiple tracks together and edit video files. While the device's complexity and price tag mean the average consumer isn't going to buy it, Xynergi might be a good choice for someone with a small recording studio or media companies that need an interface that will let them edit audio and video quickly.
In this article, we'll take a look at what makes Xynergi tick, examine some of Xynergi's functions and learn more about Fairlight's market strategy for Xynergi, including where you can pick one up and how much it'll set you back.
 The real source of Xynergi's amazing functionality is Fairlight's
CC-1 card. "CC" stands for Crystal Core, Fairlight's processing platform
for its audio production hardware. The CC-1 is both a microprocessor and a Peripheral Component Interconnect Express (PCI-Express) card. To use a Xynergi device, an engineer has to first connect it to a PC using the CC-1 card. He or she would need to install the card in one of the computer's expansion slots, which connects the card to the computer's motherboard.
The real source of Xynergi's amazing functionality is Fairlight's
CC-1 card. "CC" stands for Crystal Core, Fairlight's processing platform
for its audio production hardware. The CC-1 is both a microprocessor and a Peripheral Component Interconnect Express (PCI-Express) card. To use a Xynergi device, an engineer has to first connect it to a PC using the CC-1 card. He or she would need to install the card in one of the computer's expansion slots, which connects the card to the computer's motherboard.
The CC-1 is a field-programmable gate array (FPGA) device. An FPGA device can contain thousands of logic gates, which are the basic building blocks of digital circuits (to learn more about logic gates, head to our article on How Boolean Logic Works). Fairlight designed the CC-1 to act as a processor. All audio production functions run through the CC-1, not the host computer's CPU. This means that the PC's processing power is available for other programming tasks. In the past, PC-based audio editing devices required a computer almost entirely dedicated to audio production, because audio processing demands are so high. Since the CC-1 handles this load on its own, you can install it on a PC and still run other processes while you edit and mix audio and video tracks.
The Xynergi media production center runs on proprietary Fairlight production software. Xynergi can create and edit most media file formats, but its interactive keyboard isn't designed to work with other video and audio production software.
Xynergi's hardware and software give the system amazing capabilities .

Xynergi's interactive keyboard
has application awareness, which means the keys display only the
symbols and commands appropriate for the application currently in use.
If an engineer needs to jot some notes down in Microsoft Word,
for example, he or she can push a key on the Xynergi keyboard to
activate Word. The Xynergi's keyboard then switches to a QWERTY
keyboard. When finished, the engineer can push the Edit key to return to
Xynergi's editing software, and the keys will change again.
Because every key is actually a small color monitor, keys change colors to indicate active functions. For example, if an engineer wants to work on a specific track, he or she can push a button mapped to that track. The key will change from blue to red, indicating the track is active and ready for mixing or editing applications. If the engineer assigns a name to a specific track, the name will appear on the key mapped to that track.
Here are just a few of Xynergi's functions:
The Xynergi system includes the same functions you'd find on a
large audio or video editing console, but has a price tag that's only a
fraction of what those systems cost. In the next section, we'll find out
just how much the Xynergi system costs and where you can find one.
X . II
Without your computer keyboard, whether it's part of a desktop or a
laptop, it might've been fairly difficult to get to this article. Sure,
maybe you've bookmarked the Web site and you used your mouse to click
around between several links, but most of the time, you probably type
the Web site address into your browser to get here. Most of us with
personal computers use a keyboard almost every day to compose e-mails,
type out word processing documents, visit Web sites and perform
searches. And as easy as it may seem, typing is a skill we have to learn
and practice in order to perform properly. Most students take typing
classes as early as elementary school, and word processing is one of the
most common skills listed on a job-seeker's resume.
Without keyboards, communicating between family, friends and businesses would be a much less streamlined affair. Today, even smartphones come equipped with smaller keyboards. Phones that are more focused on e-mail and text messaging, like the BlackBerry or several of the slider phones, offer these as a more straightforward way of typing out text. On a typical cell phone with a three-by-four numeric keypad, for instance, where at least three letters are assigned to a number, you often have to punch through each key several times to get one word on the screen. Some people are remarkably adept at this -- just watch some people on a train or at the airport rifle through several text messages in a matter of no time -- but for some, the act is cumbersome and takes far too long. Miniature keyboards, however, attempt to solve that problem by giving users a complete QWERTY setup to type e-mails, text messages and reminders.

At their most basic, all keyboards, whether they're physical or
virtual, are input devices -- once you type in a certain series of
keystrokes, you're telling the keyboard to deliver a command to your
computer. This allows you to write in a word-processing document, close
out a program or write out a Web site's URL in a browser. But apart from
the science-fiction element, what sets a virtual laser keyboard apart
from a regular keyboard?
A traditional keyboard, one that hooks up to a desktop computer or is part of a laptop, is very much like another smaller computer. If you take it apart, it has a processor and circuitry similar to the insides of your computer. Underneath each key is a grid of circuits, and once you press a key, the switch closes. This sends a small electrical current through the grid, which the processor recognizes and analyzes. The processor, in turn, sends the information regarding your keystrokes to your computer, and it can do this several ways. Most desktop users connect their keyboard using cables, although common wireless technologies like Bluetooth let you type from a distance, as long as the computer has the necessary receiver. Laptop keyboards, on the other hand, connect directly to the computer's hardware.
So how do you use a virtual laser keyboard?


If it sounds like a gadget from the future, a virtual laser
keyboard sort of looks like one, too, especially when it's on full
working display. They're small and sleek, weigh about two ounces (56.7
grams) and comparable in size to a pack of gum, so they can fit easily
into pockets or carrying bags.
But when it's time to use the virtual laser keyboard, the full science-fiction novelty comes into play. Most devices either stand up straight on a rectangular base or prop up with the help of a stand that flips out from the back. Once powered up, the keyboard can connect to a smartphone, PDA or laptop via USB cable or, more commonly, Bluetooth wireless technology. These two connection options allow the virtual laser keyboard to send keystroke information to a word processing document, e-mail or any other program in question.
Mice first broke onto the public stage with the introduction of
the Apple Macintosh in 1984, and since then they have helped to
completely redefine the way we use computers.
Every day of your computing life, you reach out for your mouse whenever you want to move your cursor or activate something. Your mouse senses your motion and your clicks and sends them to the computer so it can respond appropriately.
It is amazing how simple and effective a mouse is, and it is also
amazing how long it took mice to become a part of everyday life. Given
that people naturally point at things -- usually before they speak -- it
is surprising that it took so long for a good pointing device to
develop. Although originally conceived in the 1960s, a couple of decades
passed before mice became mainstream.
In the beginning, there was no need to point because computers used crude interfaces like teletype machines or punch cards for data entry. The early text terminals did nothing more than emulate a teletype (using the screen to replace paper), so it was many years (well into the 1960s and early 1970s) before arrow keys were found on most terminals. Full screen editors were the first things to take real advantage of the cursor keys, and they offered humans the first way to point.
 The main goal of any mouse is to translate the motion of your hand
into signals that the computer can use. Let's take a look inside a
track-ball mouse to see how it works:
The main goal of any mouse is to translate the motion of your hand
into signals that the computer can use. Let's take a look inside a
track-ball mouse to see how it works:
 In this optomechanical arrangement, the disk moves
mechanically, and an optical system counts pulses of light. On this
mouse, the ball is 21 mm in diameter. The roller is 7 mm in diameter.
The encoding disk has 36 holes. So if the mouse moves 25.4 mm (1 inch),
the encoder chip detects 41 pulses of light.
In this optomechanical arrangement, the disk moves
mechanically, and an optical system counts pulses of light. On this
mouse, the ball is 21 mm in diameter. The roller is 7 mm in diameter.
The encoding disk has 36 holes. So if the mouse moves 25.4 mm (1 inch),
the encoder chip detects 41 pulses of light.
 This piece of plastic provides a window through which the infrared
sensor can "see." The window on one side of the disk is located
slightly higher than it is on the other -- one-half the height of one of
the holes in the encoder disk, to be exact. That difference causes the
two infrared sensors to see pulses of light at slightly different times.
There are times when one of the sensors will see a pulse of light when
the other does not, and vice versa.
This piece of plastic provides a window through which the infrared
sensor can "see." The window on one side of the disk is located
slightly higher than it is on the other -- one-half the height of one of
the holes in the encoder disk, to be exact. That difference causes the
two infrared sensors to see pulses of light at slightly different times.
There are times when one of the sensors will see a pulse of light when
the other does not, and vice versa.
X . IIII
Technology keyboard
In the first electronic keyboards in the early 1970s, the key
switches were individual switches inserted into holes in metal frames.
These keyboards cost from 80 to 120 USD and were used in mainframe data terminals. The most popular switch types were reed switches (contacts enclosed in a vacuum in a glass capsule, affected by a magnet mounted on the switch plunger).
In the mid-1970s, lower-cost direct-contact key switches were introduced, but their life in switch cycles was much shorter (rated ten million cycles) because they were open to the environment. This became more acceptable, however, for use in computer terminals at the time, which began to see increasingly shorter model lifespans as they advanced.
In 1978, Key Tronic Corporation introduced keyboards with capacitive-based switches, one of the first keyboard technologies to not use self-contained switches. There was simply a sponge pad with a conductive-coated Mylar plastic sheet on the switch plunger, and two half-moon trace patterns on the printed circuit board below. As the key was depressed, the capacitance between the plunger pad and the patterns on the PCB below changed, which was detected by integrated circuits (IC). These keyboards were claimed to have the same reliability as the other "solid-state switch" keyboards such as inductive and Hall-effect, but competitive with direct-contact keyboards. Prices of $60 for keyboards were achieved, and Key Tronic rapidly became the largest independent keyboard manufacturer.
Meanwhile, IBM made their own keyboards, using their own patented technology: Keys on older IBM keyboards were made with a "buckling spring" mechanism, in which a coil spring under the key buckles under pressure from the user's finger, triggering a hammer that presses two plastic sheets (membranes) with conductive traces together, completing a circuit. This produces a clicking sound and gives physical feedback for the typist, indicating that the key has been depressed.
The first electronic keyboards had a typewriter key travel distance of 0.187 inches (4.75 mm), keytops were a half-inch (12.7 mm) high, and keyboards were about two inches (5 cm) thick. Over time, less key travel was accepted in the market, finally landing on 0.110 inches (2.79 mm). Coincident with this, Key Tronic was the first company to introduce a keyboard that was only about one inch thick. And now keyboards measure only about a half-inch thick.
Keytops are an important element of keyboards. In the beginning, keyboard keytops had a "dish shape" on top, like typewriters before them. Keyboard key legends must be extremely durable over tens of millions of depressions, since they are subjected to extreme mechanical wear from fingers and fingernails, and subject to hand oils and creams, so engraving and filling key legends with paint, as was done previously for individual switches, was never acceptable. So, for the first electronic keyboards, the key legends were produced by two-shot (or double-shot, or two-color) molding, where either the key shell or the inside of the key with the key legend was molded first, and then the other color molded second. But, to save cost, other methods were explored, such as sublimation printing and laser engraving, both methods which could be used to print a whole keyboard at the same time.
Initially, sublimation printing, where a special ink is printed onto the keycap surface and the application of heat causes the ink molecules to penetrate and commingle with the plastic modules, had a problem because finger oils caused the molecules to disperse, but then a necessarily very hard clear coating was applied to prevent this. Coincident with sublimation printing, which was first used in high volume by IBM on their keyboards, was the introduction by IBM of single-curved-dish keycaps to facilitate quality printing of key legends by having a consistently curved surface instead of a dish. But one problem with sublimation or laser printing was that the processes took too long and only dark legends could be printed on light-colored keys. On another note, IBM was unique in using separate shells, or "keycaps", on keytop bases. This might have made their manufacturing of different keyboard layouts more flexible, but the reason for doing this was that the plastic material that needed to be used for sublimation printing was different from standard ABS keytop plastic material.
Three final mechanical technologies brought keyboards to where they are today, driving the cost well under $10:
Computer keyboards include control circuitry to convert key presses into key codes (usually scancodes)
that the computer's electronics can understand. The key switches are
connected via the printed circuit board in an electrical X-Y matrix
where a voltage is provided sequentially to the Y lines and, when a key
is depressed, detected sequentially by scanning the X lines.
The first computer keyboards were for mainframe computer data terminals and used discrete electronic parts. The first keyboard microprocessor was introduced in 1972 by General Instruments, but keyboards have been using the single-chip 8048 microcontroller variant since it became available in 1978. The keyboard switch matrix is wired to its inputs, it converts the keystrokes to key codes, and, for a detached keyboard, sends the codes down a serial cable (the keyboard cord) to the main processor on the computer motherboard. This serial keyboard cable communication is only bi-directional to the extent that the computer's electronics controls the illumination of the caps lock, num lock and scroll lock lights.
One test for whether the computer has crashed is pressing the caps lock key. The keyboard sends the key code to the keyboard driver running in the main computer; if the main computer is operating, it commands the light to turn on. All the other indicator lights work in a similar way. The keyboard driver also tracks the Shift, alt and control state of the keyboard.
Some lower-quality keyboards have multiple or false key entries due to inadequate electrical designs. These are caused by inadequate keyswitch "debouncing" or inadequate keyswitch matrix layout that don't allow multiple keys to be depressed at the same time, both circumstances which are explained below:
When pressing a keyboard key, the key contacts may "bounce" against each other for several milliseconds before they settle into firm contact. When released, they bounce some more until they revert to the uncontacted state. If the computer were watching for each pulse, it would see many keystrokes for what the user thought was just one. To resolve this problem, the processor in a keyboard (or computer) "debounces" the keystrokes, by aggregating them across time to produce one "confirmed" keystroke.
Some low-quality keyboards also suffer problems with rollover (that is, when multiple keys pressed at the same time, or when keys are pressed so fast that multiple keys are down within the same milliseconds). Early "solid-state" keyswitch keyboards did not have this problem because the keyswitches are electrically isolated from each other, and early "direct-contact" keyswitch keyboards avoided this problem by having isolation diodes for every keyswitch. These early keyboards had "n-key" rollover, which means any number of keys can be depressed and the keyboard will still recognize the next key depressed. But when three keys are pressed (electrically closed) at the same time in a "direct contact" keyswitch matrix that doesn't have isolation diodes, the keyboard electronics can see a fourth "phantom" key which is the intersection of the X and Y lines of the three keys. Some types of keyboard circuitry will register a maximum number of keys at one time. "Three-key" rollover, also called "phantom key blocking" or "phantom key lockout", will only register three keys and ignore all others until one of the three keys is lifted. This is undesirable, especially for fast typing (hitting new keys before the fingers can release previous keys), and games (designed for multiple key presses).
As direct-contact membrane keyboards became popular, the available rollover of keys was optimized by analyzing the most common key sequences and placing these keys so that they do not potentially produce phantom keys in the electrical key matrix (for example, simply placing three or four keys that might be depressed simultaneously on the same X or same Y line, so that a phantom key intersection/short cannot happen), so that blocking a third key usually isn't a problem. But lower-quality keyboard designs and unknowledgeable engineers may not know these tricks, and it can still be a problem in games due to wildly different or configurable layouts in different games.
Wireless keyboards have become popular for their increased user freedom. A wireless keyboard often includes a required combination transmitter and receiver unit that attaches to the computer's keyboard port. The wireless aspect is achieved either by radio frequency (RF) or by infrared (IR) signals sent and received from both the keyboard and the unit attached to the computer. A wireless keyboard may use an industry standard RF, called Bluetooth. With Bluetooth, the transceiver may be built into the computer. However, a wireless keyboard needs batteries to work and may pose a security problem due to the risk of data "eavesdropping" by hackers. Wireless solar keyboards charge their batteries from small solar panels using sunlight or standard artificial lighting. An early example of a consumer wireless keyboard is that of the Olivetti Envision.
Optical character recognition
(OCR) is preferable to rekeying for converting existing text that is
already written down but not in machine-readable format (for example, a Linotype-composed
book from the 1940s). In other words, to convert the text from an image
to editable text (that is, a string of character codes), a person could
re-type it, or a computer could look at the image and deduce what each
character is. OCR technology has already reached an impressive state
(for example, Google Book Search) and promises more for the future.
Speech recognition converts speech into machine-readable text (that is, a string of character codes). This technology has also reached an advanced state and is implemented in various software products. For certain uses (e.g., transcription of medical or legal dictation; journalism; writing essays or novels) speech recognition is starting to replace the keyboard. However, the lack of privacy when issuing voice commands and dictation makes this kind of input unsuitable for many environments.
Pointing devices can be used to enter text or characters in contexts where using a physical keyboard would be inappropriate or impossible. These accessories typically present characters on a display, in a layout that provides fast access to the more frequently used characters or character combinations. Popular examples of this kind of input are Graffiti, Dasher and on-screen virtual keyboards.
Keystroke logging (often called keylogging) is a method of capturing and recording user keystrokes. While it is used legally to measure employee productivity on certain clerical tasks, or by law enforcement agencies to find out about illegal activities, it is also used by hackers for various illegal or malicious acts. Hackers use keyloggers as a means to obtain passwords or encryption keys and thus bypass other security measures.
Keystroke logging can be achieved by both hardware and software means. Hardware key loggers are attached to the keyboard cable or installed inside standard keyboards. Software keyloggers work on the target computer's operating system and gain unauthorized access to the hardware, hook into the keyboard with functions provided by the OS, or use remote access software to transmit recorded data out of the target computer to a remote location. Some hackers also use wireless keylogger sniffers to collect packets of data being transferred from a wireless keyboard and its receiver, and then they crack the encryption key being used to secure wireless communications between the two devices.
Anti-spyware applications are able to detect many keyloggers and cleanse them. Responsible vendors of monitoring software support detection by anti-spyware programs, thus preventing abuse of the software. Enabling a firewall does not stop keyloggers per se, but can possibly prevent transmission of the logged material over the net if properly configured. Network monitors (also known as reverse-firewalls) can be used to alert the user whenever an application attempts to make a network connection. This gives the user the chance to prevent the keylogger from "phoning home" with his or her typed information. Automatic form-filling programs can prevent keylogging entirely by not using the keyboard at all. Most keyloggers can be fooled by alternating between typing the login credentials and typing characters somewhere else in the focus window.
Keyboards are also known to emit electromagnetic signatures that can be detected using special spying equipment to reconstruct the keys pressed on the keyboard. Neal O'Farrell, executive director of the Identity Theft Council, revealed to InformationWeek that "More than 25 years ago, a couple of former spooks showed me how they could capture a user's ATM PIN, from a van parked across the street, simply by capturing and decoding the electromagnetic signals generated by every keystroke," O'Farrell said. "They could even capture keystrokes from computers in nearby offices, but the technology wasn't sophisticated enough to focus in on any specific computer."
The use of any keyboard may cause serious injury (that is, carpal tunnel syndrome or other repetitive strain injury) to hands, wrists, arms, neck or back. The risks of injuries can be reduced by taking frequent short breaks to
get up and walk around a couple of times every hour. As well, users
should vary tasks throughout the day, to avoid overuse of the hands and
wrists. When inputting at the keyboard, a person should keep the
shoulders relaxed with the elbows at the side, with the keyboard and
mouse positioned so that reaching is not necessary. The chair height and
keyboard tray should be adjusted so that the wrists are straight, and
the wrists should not be rested on sharp table edges. Wrist or palm
rests should not be used while typing.
Some adaptive technology ranging from special keyboards, mouse replacements and pen tablet interfaces to speech recognition software can reduce the risk of injury. Pause software reminds the user to pause frequently. Switching to a much more ergonomic mouse, such as a vertical mouse or joystick mouse may provide relief. Switching from using a mouse to using a stylus pen with graphic tablet or a trackpad can lessen the repetitive strain on the arms and hands.
A wireless keyboard is a computer keyboard that allows the user to communicate with computers, tablets, or laptops with the help of radio frequency (RF), infrared (IR) or Bluetooth technology. It is common for wireless keyboards available these days to be accompanied by a wireless mouse.
Wireless keyboards based on infrared technology use light waves to transmit signals to other infrared-enabled devices. But, in case of radio frequency technology, a wireless keyboard communicates using signals which range from 27 MHz to up to 2.4 GHz. Most wireless keyboards today work on 2.4 GHz radio frequency. Bluetooth is another technology that is being widely used by wireless keyboards. These devices connect and communicate to their parent device via the bluetooth protocol.
A wireless keyboard can be connected using RF technology with the help of two parts, a transmitter and a receiver. The radio transmitter is inside the wireless keyboard. The radio receiver plugs into a keyboard port or USB port. Once the receiver and transmitter are plugged in, the computer recognizes the keyboard and mouse as if they were connected via a cable.
A Bluetooth keyboard is a wireless keyboard that connects and communicates with its parent device via the Bluetooth protocol. These devices are widely used with such portable devices as smart phones and tablets, though they are also used with laptops and ultrabooks. Bluetooth keyboards became popular in 2011, coincident with the popularity of portable devices.
In computing, a keyboard shortcut is a sequence or combination of keystrokes on a computer keyboard which invokes commands in software.
Most keyboard shortcuts require the user to press a single key or a sequence of keys one after the other. Other keyboard shortcuts require pressing and holding several keys simultaneously (indicated in the tables below by this sign: +). Keyboard shortcuts may depend on the keyboard layout (localization)
Keyboard Types Based on the Connector1. Serial KeyboardKeyboard this type is usually used for computer type AT. Because the type of connector on this keyboard is a serial connector, then to connect it with the computer must be inserted into the serial port.
 2. Keyboard PS / 2
2. Keyboard PS / 2
The PS / 2 keyboard is a keyboard connected to the computer using the PS / 2 port. Usually used on ATX computers and still commonly used in older computers. Installation of this type of keyboard must be implemented carefully, because the port is the same as the port for the mouse.3. USB KeyboardThe latest computer today has many who use a type of USB connector that ensures faster data transfers, other than that how to install it more easily.

| Esc | F1 | F2 | F3 | F4 | F5 | F6 | F7 | F8 | F9 | F10 | F11 | F12 | PrtSc | ScrLk | Pause | |||||||||
 |
Ins | Home | PgUp | NumLk | / | * | - | |||||||||||||||||
| Del | End | PgDn | 7 | 8 | 9 | + | ||||||||||||||||||
| 4 | 5 | 6 | ||||||||||||||||||||||
| ↑ | 1 | 2 | 3 | En ter | ||||||||||||||||||||
X . I
How Computer Keyboards Work

An average Windows keyboard.
But no matter how many bells and whistles they offer, most keyboards operate using similar technology. They use switches and circuits to translate a person's keystrokes into a signal a computer can understand. In this article we will explore keyboard technology along with different key layouts, options and designs.
Keyboard Basics

Keyboards differ by manufacturer and the operating system they are designed for.
Most keyboards have between 80 and 110 keys, including:
* Typing keys
- A numeric keypad
- Function keys
- Control keys
Keyboards can also use a variety of other typing key arrangements. The most widely known is Dvorak, named for its creator, August Dvorak. The Dvorak layout places all of the vowels on the left side of the keyboard and the most common consonants on the right. The most commonly used letters are all found along the home row. The home row is the main row where you place your fingers when you begin typing. People who prefer the Dvorak layout say it increases their typing speed and reduces fatigue. Other layouts include ABCDE, XPeRT, QWERTZ and AZERTY. Each is named for the first keys in the pattern. The QWERTZ and AZERTY arrangements are commonly used in Europe.
The numeric keypad is a more recent addition to the computer keyboard. As the use of computers in business environments increased, so did the need for speedy data entry. Since a large part of the data was numbers, a set of 17 keys, arranged in the same configuration found on adding machines and calculators, was added to the keyboard.

The Apple keyboard's control keys include the "Command" key.
Other common control keys include:
- Home
- End
- Insert
- Delete
- Page Up
- Page Down
- Control (Ctrl)
- Alternate (Alt)
- Escape (Esc)
Inside the Keyboard

The microprocessor and controller circuitry of a keyboard
The key matrix is a grid of circuits underneath the keys. In all keyboards (except for capacitive models, which we'll discuss in the next section), each circuit is broken at a point below each key. When you press a key, it presses a switch, completing the circuit and allowing a tiny amount of current to flow through. The mechanical action of the switch causes some vibration, called bounce, which the processor filters out. If you press and hold a key, the processor recognizes it as the equivalent of pressing a key repeatedly.
When the processor finds a circuit that is closed, it compares the location of that circuit on the key matrix to the character map in its read-only memory (ROM).
A character map is basically a comparison chart or lookup table. It
tells the processor the position of each key in the matrix and what each
keystroke or combination of keystrokes represents. For example, the
character map lets the processor know that pressing the a key by itself corresponds to a small letter "a," but the Shift and a keys pressed together correspond to a capital "A."

The key matrix
Keyboard Switches

This keyboard uses rubber dome switches.
All of the other types of switches used in keyboards are mechanical in nature. Each provides a different level of audible and tactile response -- the sounds and sensations that typing creates. Mechanical key switches include:
. Rubber dome
- Membrane
- Metal contact
- Foam element

This keyboard uses rubber dome switches.
Rather than having a switch for each key, membrane keyboards use a continuous membrane that stretches from one end to another. A pattern printed in the membrane completes the circuit when you press a key. Some membrane keyboards use a flat surface printed with representations of each key rather than keycaps. Membrane keyboards don't have good tactile response, and without additional mechanical components they don't make the clicking sound that some people like to hear when they're typing. However, they're generally inexpensive to make.
Metal contact and foam element keyboards are increasingly less common. Metal contact switches simply have a spring-loaded key with a strip of metal on the bottom of the plunger. When the key is pressed, the metal strip connects the two parts of the circuit. The foam element switch is basically the same design but with a small piece of spongy foam between the bottom of the plunger and the metal strip, providing a better tactile response. Both technologies have good tactile response, make satisfyingly audible "clicks," and are inexpensive to produce. The problem is that the contacts tend to wear out or corrode faster than on keyboards that use other technologies. Also, there is no barrier that prevents dust or liquids from coming in direct contact with the circuitry of the key matrix.
Different manufacturers have used these standard technologies, and a few others, to create a wide range of non-traditional keyboards. We'll take a look at some of these non-traditional keyboards in the next section.
Non-Traditional Keyboards

The SafeType keyboard places the two halves of the keyboard perpendicular to the desk surface.
The simplest ergonomic keyboards look like traditional keyboards that have been divided down the middle, keeping a person's hands farther apart and aligning the wrists with the forearms. More complex designs place the two halves of the keyboard at varying angles to one another and to the surface on which the keyboard rests. Some go even further, placing the two halves of the keyboard on the armrests of chairs or making them completely perpendicular to the desk surface. Others, like the Datahand, don't look much like keyboards at all.

Saitek Truview backlit keyboard buttons
- Das Keyboard is a completely black keyboard with weighted keys that require more pressure from a person's strongest fingers and less pressure from the weaker ones.
- The Virtual Laser Keyboard projects a representation of a keyboard onto a flat surface. When used successfully, a person's fingers pass through the beam of infrared light above the projected surface, and a sensor interprets it as a keystroke.
- The True-touch Roll-up keyboard is flexible and can be rolled up to fit in a backpack or bag. Blue backlit keyboard 'on' Blue backlit keyboard 'off'
- Illuminated keyboards, like the Ion Illuminated Keyboard, use light-emitting diodes or electroluminescent film to send light through the keys or the spaces between keys. Photo courtesy www.artlebedev.com Optimus keyboard programmable hot keys
- The Optimus keyboard has organic light-emitting diodes (OLEDs) in the keys. Users can change what letter, command or action each key represents, and the OLED can change to display the new information.

This Optimus keyboard is set for keystrokes used to play Quake.
From the Keyboard to the Computer

A PS/2 type keyboard connector.
Many keyboards connect to the computer through a cable with a PS/2 or USB (Universal Serial Bus) connector. Laptops use internal connectors. Regardless of which type of connector is used, the cable must carry power to the keyboard, and it must carry signals from the keyboard back to the computer.
Wireless keyboards, on the other hand, connect to the computer through infrared (IR), radio frequency (RF) or Bluetooth connections. IR and RF connections are similar to what you'd find in a remote control. Regardless of which sort of signal they use, wireless keyboards require a receiver,
either built in or plugged in to the USB port, to communicate with the
computer. Since they don't have a physical connection to the computer,
wireless keyboards have an AC power connection or use batteries for power.

Microsoft wireless keyboard

This Microsoft wireless keyboard is battery-powered.
The application determines whether the keyboard data is a command, like Alt-f, which opens the File menu in a Windows application. If the data is not a command, the application accepts it as content, which can be anything from typing a document to entering a URL to performing a calculation. If the current application does not accept keyboard data, it simply ignores the information. This whole process, from pressing the key to entering content into an application, happens almost instantaneously.
How the Xynergi Keyboard Works

The Xynergi keyboard is part of a desktop media production center package. Fairlight designed Xynergi to meet the needs of small, professional media editing studios. With Xynergi, engineers can capture audio, manipulate individual tracks, add effects, mix multiple tracks together and edit video files. While the device's complexity and price tag mean the average consumer isn't going to buy it, Xynergi might be a good choice for someone with a small recording studio or media companies that need an interface that will let them edit audio and video quickly.
The Xynergi keyboard looks like a large computer keyboard with several extra keys, a few knobs, a dial called a jog wheel and a rectangular color monitor above the main array of keys. Fairlight calls the monitor and the surrounding controls the pad. Xynergi's main key array is in the standard QWERTY layout with a number pad on the right. Engineers use the knobs, keys and jog wheel to manipulate digital audio and video files.
If you've ever seen a professional audio mixing console or video
editing control system, you know that there are many more switches,
knobs and toggles than you'll find on the Xynergi keyboard. In order to
replicate the functions that these large consoles have, Fairlight came
up with a clever idea -- self-labeling keys. These are keys that can
change functions and key labels depending on what you're trying to do.
Each key is a small computer monitor that can display different
characters, including letters, symbols and words. Xynergi has an
"animate" feature that makes keys flash on and off or change colors
during specific tasks. The keys can even display video. As engineers
switch from one operating mode to another (for example, moving from a
word processing mode to an audio mixing mode), the key labels change and
the keys themselves map to new functions.In this article, we'll take a look at what makes Xynergi tick, examine some of Xynergi's functions and learn more about Fairlight's market strategy for Xynergi, including where you can pick one up and how much it'll set you back.
Xynergi Components

The CC-1 is a field-programmable gate array (FPGA) device. An FPGA device can contain thousands of logic gates, which are the basic building blocks of digital circuits (to learn more about logic gates, head to our article on How Boolean Logic Works). Fairlight designed the CC-1 to act as a processor. All audio production functions run through the CC-1, not the host computer's CPU. This means that the PC's processing power is available for other programming tasks. In the past, PC-based audio editing devices required a computer almost entirely dedicated to audio production, because audio processing demands are so high. Since the CC-1 handles this load on its own, you can install it on a PC and still run other processes while you edit and mix audio and video tracks.
Fairlight offers four different configurations for the Xynergi
system -- every version can perform the same basic tasks, but the
higher-end versions have more processing capability. The top-of-the-line
system is the Xynergi MPC-230F, which has 230 processing
channels, 96 concurrent recording tracks and 192 concurrent playback
tracks. In other words, Xynergi engineers can record, edit, mix and play
back dozens of individual audio tracks to make rich, complex master
recordings.
Xynergi systems also include an I/O toolbox called an SX-20. The SX-20 has two preamps,
which are outputs that boost the power of a signal before sending the
signal to another component. The system also has two analog
inputs, 12 analog outputs, four digital inputs and eight digital
outputs, which allow the engineer to connect the system to other
components, including microphones, instruments and speakers.The Xynergi media production center runs on proprietary Fairlight production software. Xynergi can create and edit most media file formats, but its interactive keyboard isn't designed to work with other video and audio production software.
Xynergi's hardware and software give the system amazing capabilities .
Xynergi Functions

An audio engineer uses Xynergi to manipulate tracks.
Because every key is actually a small color monitor, keys change colors to indicate active functions. For example, if an engineer wants to work on a specific track, he or she can push a button mapped to that track. The key will change from blue to red, indicating the track is active and ready for mixing or editing applications. If the engineer assigns a name to a specific track, the name will appear on the key mapped to that track.
Engineers use the jog wheel whenever they need to scan
through an audio track quickly. Rotating the jog wheel clockwise or
counterclockwise advances or reverses the track, respectively. This
feature also allows engineers to designate specific sections of a track
for editing -- the engineer uses the wheel to mark the beginning and end
of a range within a track. The engineer can then add effects to the
marked range without affecting the rest of the recording.
Fairlight calls the area that includes the color screen and the surrounding buttons and knobs the pad.
The screen displays information about audio tracks, giving users a
visual representation of the digital file. It can show the name of an
audio track, bars that indicate the distribution of the track's sound
across different speaker channels, an equalizer and a time code
display. The buttons and knobs surrounding the screen allow an engineer
to manipulate the track or set Xynergi in its automated editor mode.Here are just a few of Xynergi's functions:
- Recording tracks: Xynergi can record incoming audio. Audio can come from other digital devices or straight from an instrument or microphone feed.
- Editing tracks: Engineers can edit audio tracks extensively, adding in effects like echo or reverberation, looping sections of track and adjusting frequency equalization.
- Mixing tracks: Once an engineer has his or her audio tracks adjusted just right, he or she can mix it with other tracks, eventually creating a complex master track. Xynergi can even take over mixing duties with an automated mixing program.
- Playback: Xynergi can play audio tracks, sending the signal to speakers connected to the media center. Engineers can isolate a specific speaker to make sure the right level of sound is reaching it, or listen to all the speakers together to create a surround sound effect.
X . II
How Virtual Laser Keyboards Work
Without keyboards, communicating between family, friends and businesses would be a much less streamlined affair. Today, even smartphones come equipped with smaller keyboards. Phones that are more focused on e-mail and text messaging, like the BlackBerry or several of the slider phones, offer these as a more straightforward way of typing out text. On a typical cell phone with a three-by-four numeric keypad, for instance, where at least three letters are assigned to a number, you often have to punch through each key several times to get one word on the screen. Some people are remarkably adept at this -- just watch some people on a train or at the airport rifle through several text messages in a matter of no time -- but for some, the act is cumbersome and takes far too long. Miniature keyboards, however, attempt to solve that problem by giving users a complete QWERTY setup to type e-mails, text messages and reminders.
But there's another problem. People with bigger fingers may find
the keyboards on smartphones and PDAs too small. To make up for this,
some manufactures have developed special virtual laser keyboards to
accompany handheld devices. Instead of having to poke lightly around
your phone's keyboard, a virtual laser keyboard connects to the phone
and projects a full-sized virtual keyboard onto any flat surface. So how
do they work?
How Virtual Laser Keyboards Work
Mechanics of Virtual Laser Keyboards

Although virtual laser keyboards perform the same function as
traditional keyboards, how they analyze and send information to another
device is a different process.
A traditional keyboard, one that hooks up to a desktop computer or is part of a laptop, is very much like another smaller computer. If you take it apart, it has a processor and circuitry similar to the insides of your computer. Underneath each key is a grid of circuits, and once you press a key, the switch closes. This sends a small electrical current through the grid, which the processor recognizes and analyzes. The processor, in turn, sends the information regarding your keystrokes to your computer, and it can do this several ways. Most desktop users connect their keyboard using cables, although common wireless technologies like Bluetooth let you type from a distance, as long as the computer has the necessary receiver. Laptop keyboards, on the other hand, connect directly to the computer's hardware.
When you type on a virtual laser keyboard, there aren't any
switches involved. In fact, there aren't any mechanical moving parts at
all. The device projects the image of a QWERTY keyboard onto a flat,
non-reflective surface using a red diode laser. The laser, similar to
the kind you see on those cheap laser pointers people wave at rock
concerts, shines through a Diffractive Optical Element (DOE), which is
simply a tiny image of the keyboard. The DOE, along with special optical
lenses, expands the image to a usable size and projects it onto a
surface.
But a simple image of a keyboard won't get you anywhere --
something needs to analyze the information you type in. Situated near
the bottom of the device is an infrared (IR) laser diode, which shoots
out a thin plane of infrared light. The plane, which is invisible and
runs parallel to the surface, rests only millimeters above the image of
the keyboard. When you start typing, you pass your fingers through
certain areas of the infrared light. A CMOS (complimentary metal-oxide
semiconductor) images your finger's position within the area of the
keyboard, and a special sensor chip called a Virtual Interface
Processing Core analyzes the location of the intended keystroke. The
device then sends this information to the computer receiving the
commands.So how do you use a virtual laser keyboard?

How Virtual Laser Keyboards Work
Using Virtual Laser Keyboards

Virtual laser keyboards are about the size of a pack of gum,
and can slip into your pocket. Most work with a variety of smartphones,
PDAs and desktop and laptop setups.
But when it's time to use the virtual laser keyboard, the full science-fiction novelty comes into play. Most devices either stand up straight on a rectangular base or prop up with the help of a stand that flips out from the back. Once powered up, the keyboard can connect to a smartphone, PDA or laptop via USB cable or, more commonly, Bluetooth wireless technology. These two connection options allow the virtual laser keyboard to send keystroke information to a word processing document, e-mail or any other program in question.
Although they're small and convenient to carry around, you can't
simply pull out the virtual laser keyboard and start typing away in any
location. If you were sitting on the bus, for instance, and wanted to
write a quick e-mail on your BlackBerry, you couldn't shine the device's
red laser onto your lap and expect it to work properly. Virtual laser
keyboards require flat, opaque and non-reflective surfaces for working
projection and typing. Once you have the keyboard set up on the right
type of surface, the device displays a full-size QWERTY keyboard, which
typically contains 60 or more keys. Then you simply type just like you
would on a normal keyboard, although the sensation you normally get when
typing on a laptop or desktop -- the pops and clicks associated with
the keystrokes punching up and down -- won't be there. In fact, it takes
a little bit of practice for many users to become accustomed to
pressing their fingers on a smooth surface.
X . III
How Computer Mice Work
Every day of your computing life, you reach out for your mouse whenever you want to move your cursor or activate something. Your mouse senses your motion and your clicks and sends them to the computer so it can respond appropriately.
Evolution of the Computer Mouse
In the beginning, there was no need to point because computers used crude interfaces like teletype machines or punch cards for data entry. The early text terminals did nothing more than emulate a teletype (using the screen to replace paper), so it was many years (well into the 1960s and early 1970s) before arrow keys were found on most terminals. Full screen editors were the first things to take real advantage of the cursor keys, and they offered humans the first way to point.
Light pens were used on a variety of machines as a pointing
device for many years, and graphics tablets, joy sticks and various
other devices were also popular in the 1970s. None of these really took
off as the pointing device of choice, however.
When the mouse hit the scene -- attached to the Mac, it was an
immediate success. There is something about it that is completely
natural. Compared to a graphics tablet, mice are extremely inexpensive
and they take up very little desk space. In the PC world, mice took longer to gain ground, mainly because of a lack of support in the operating system.
Once Windows 3.1 made Graphical User Interfaces (GUIs) a standard, the
mouse became the PC-human interface of choice very quickly.
Inside a Mouse

The guts of a mouse
- A ball inside the mouse touches the desktop and rolls when the mouse moves. The underside of the mouse's logic board: The exposed portion of the ball touches the desktop.
- Two rollers inside the mouse touch the ball. One of the rollers is oriented so that it detects motion in the X direction, and the other is oriented 90 degrees to the first roller so it detects motion in the Y direction. When the ball rotates, one or both of these rollers rotate as well. The following image shows the two white rollers on this mouse: The rollers that touch the ball and detect X and Y motion
- The rollers each connect to a shaft, and the shaft spins a disk with holes in it. When a roller rolls, its shaft and disk spin. The following image shows the disk: A typical optical encoding disk: This disk has 36 holes around its outer edge.
- On either side of the disk there is an infrared LED and an infrared sensor. The holes in the disk break the beam of light coming from the LED so that the infrared sensor sees pulses of light. The rate of the pulsing is directly related to the speed of the mouse and the distance it travels. A close-up of one of the optical encoders that track mouse motion: There is an infrared LED (clear) on one side of the disk and an infrared sensor (red) on the other.
- An on-board processor chip reads the pulses from the infrared sensors and turns them into binary data that the computer can understand. The chip sends the binary data to the computer through the mouse's cord.

The logic section of a mouse is dominated by an encoder
chip, a small processor that reads the pulses coming from the infrared
sensors and turns them into bytes sent to the computer. You can also see
the two buttons that detect clicks (on either side of the wire
connector).
You might have noticed that each encoder disk has two infrared
LEDs and two infrared sensors, one on each side of the disk (so there
are four LED/sensor pairs inside a mouse). This arrangement allows the
processor to detect the disk's direction of rotation. There is a
piece of plastic with a small, precisely located hole that sits between
the encoder disk and each infrared sensor. It is visible in this photo:

A close-up of one of the optical encoders that track mouse
motion: Note the piece of plastic between the infrared sensor (red) and
the encoding disk.
X . IIII
Technology keyboard
Keys with integrated LED indicator lights.
Technology
In the mid-1970s, lower-cost direct-contact key switches were introduced, but their life in switch cycles was much shorter (rated ten million cycles) because they were open to the environment. This became more acceptable, however, for use in computer terminals at the time, which began to see increasingly shorter model lifespans as they advanced.
In 1978, Key Tronic Corporation introduced keyboards with capacitive-based switches, one of the first keyboard technologies to not use self-contained switches. There was simply a sponge pad with a conductive-coated Mylar plastic sheet on the switch plunger, and two half-moon trace patterns on the printed circuit board below. As the key was depressed, the capacitance between the plunger pad and the patterns on the PCB below changed, which was detected by integrated circuits (IC). These keyboards were claimed to have the same reliability as the other "solid-state switch" keyboards such as inductive and Hall-effect, but competitive with direct-contact keyboards. Prices of $60 for keyboards were achieved, and Key Tronic rapidly became the largest independent keyboard manufacturer.
Meanwhile, IBM made their own keyboards, using their own patented technology: Keys on older IBM keyboards were made with a "buckling spring" mechanism, in which a coil spring under the key buckles under pressure from the user's finger, triggering a hammer that presses two plastic sheets (membranes) with conductive traces together, completing a circuit. This produces a clicking sound and gives physical feedback for the typist, indicating that the key has been depressed.
The first electronic keyboards had a typewriter key travel distance of 0.187 inches (4.75 mm), keytops were a half-inch (12.7 mm) high, and keyboards were about two inches (5 cm) thick. Over time, less key travel was accepted in the market, finally landing on 0.110 inches (2.79 mm). Coincident with this, Key Tronic was the first company to introduce a keyboard that was only about one inch thick. And now keyboards measure only about a half-inch thick.
Keytops are an important element of keyboards. In the beginning, keyboard keytops had a "dish shape" on top, like typewriters before them. Keyboard key legends must be extremely durable over tens of millions of depressions, since they are subjected to extreme mechanical wear from fingers and fingernails, and subject to hand oils and creams, so engraving and filling key legends with paint, as was done previously for individual switches, was never acceptable. So, for the first electronic keyboards, the key legends were produced by two-shot (or double-shot, or two-color) molding, where either the key shell or the inside of the key with the key legend was molded first, and then the other color molded second. But, to save cost, other methods were explored, such as sublimation printing and laser engraving, both methods which could be used to print a whole keyboard at the same time.
Initially, sublimation printing, where a special ink is printed onto the keycap surface and the application of heat causes the ink molecules to penetrate and commingle with the plastic modules, had a problem because finger oils caused the molecules to disperse, but then a necessarily very hard clear coating was applied to prevent this. Coincident with sublimation printing, which was first used in high volume by IBM on their keyboards, was the introduction by IBM of single-curved-dish keycaps to facilitate quality printing of key legends by having a consistently curved surface instead of a dish. But one problem with sublimation or laser printing was that the processes took too long and only dark legends could be printed on light-colored keys. On another note, IBM was unique in using separate shells, or "keycaps", on keytop bases. This might have made their manufacturing of different keyboard layouts more flexible, but the reason for doing this was that the plastic material that needed to be used for sublimation printing was different from standard ABS keytop plastic material.
Three final mechanical technologies brought keyboards to where they are today, driving the cost well under $10:
- "Monoblock" keyboard designs were developed where individual switch housings were eliminated and a one-piece "monoblock" housing used instead. This was possible because of molding techniques that could provide very tight tolerances for the switch-plunger holes and guides across the width of the keyboard so that the key plunger-to-housing clearances were not too tight or too loose, either of which could cause the keys to bind.
- The use of contact-switch membrane sheets under the monoblock. This technology came from flat-panel switch membranes, where the switch contacts are printed inside of a top and bottom layer, with a spacer layer in between, so that when pressure is applied to the area above, a direct electrical contact is made. The membrane layers can be printed by very-high volume, low-cost "reel-to-reel" printing machines, with each keyboard membrane cut and punched out afterwards.
Control processor
Scanning procedure
The first computer keyboards were for mainframe computer data terminals and used discrete electronic parts. The first keyboard microprocessor was introduced in 1972 by General Instruments, but keyboards have been using the single-chip 8048 microcontroller variant since it became available in 1978. The keyboard switch matrix is wired to its inputs, it converts the keystrokes to key codes, and, for a detached keyboard, sends the codes down a serial cable (the keyboard cord) to the main processor on the computer motherboard. This serial keyboard cable communication is only bi-directional to the extent that the computer's electronics controls the illumination of the caps lock, num lock and scroll lock lights.
One test for whether the computer has crashed is pressing the caps lock key. The keyboard sends the key code to the keyboard driver running in the main computer; if the main computer is operating, it commands the light to turn on. All the other indicator lights work in a similar way. The keyboard driver also tracks the Shift, alt and control state of the keyboard.
Some lower-quality keyboards have multiple or false key entries due to inadequate electrical designs. These are caused by inadequate keyswitch "debouncing" or inadequate keyswitch matrix layout that don't allow multiple keys to be depressed at the same time, both circumstances which are explained below:
When pressing a keyboard key, the key contacts may "bounce" against each other for several milliseconds before they settle into firm contact. When released, they bounce some more until they revert to the uncontacted state. If the computer were watching for each pulse, it would see many keystrokes for what the user thought was just one. To resolve this problem, the processor in a keyboard (or computer) "debounces" the keystrokes, by aggregating them across time to produce one "confirmed" keystroke.
Some low-quality keyboards also suffer problems with rollover (that is, when multiple keys pressed at the same time, or when keys are pressed so fast that multiple keys are down within the same milliseconds). Early "solid-state" keyswitch keyboards did not have this problem because the keyswitches are electrically isolated from each other, and early "direct-contact" keyswitch keyboards avoided this problem by having isolation diodes for every keyswitch. These early keyboards had "n-key" rollover, which means any number of keys can be depressed and the keyboard will still recognize the next key depressed. But when three keys are pressed (electrically closed) at the same time in a "direct contact" keyswitch matrix that doesn't have isolation diodes, the keyboard electronics can see a fourth "phantom" key which is the intersection of the X and Y lines of the three keys. Some types of keyboard circuitry will register a maximum number of keys at one time. "Three-key" rollover, also called "phantom key blocking" or "phantom key lockout", will only register three keys and ignore all others until one of the three keys is lifted. This is undesirable, especially for fast typing (hitting new keys before the fingers can release previous keys), and games (designed for multiple key presses).
As direct-contact membrane keyboards became popular, the available rollover of keys was optimized by analyzing the most common key sequences and placing these keys so that they do not potentially produce phantom keys in the electrical key matrix (for example, simply placing three or four keys that might be depressed simultaneously on the same X or same Y line, so that a phantom key intersection/short cannot happen), so that blocking a third key usually isn't a problem. But lower-quality keyboard designs and unknowledgeable engineers may not know these tricks, and it can still be a problem in games due to wildly different or configurable layouts in different games.
Connection types
There are several ways of connecting a keyboard to a system unit (more precisely, to its keyboard controller) using cables, including the standard AT connector commonly found on motherboards, which was eventually replaced by the PS/2 and the USB connection. Prior to the iMac line of systems, Apple used the proprietary Apple Desktop Bus for its keyboard connector.Wireless keyboards have become popular for their increased user freedom. A wireless keyboard often includes a required combination transmitter and receiver unit that attaches to the computer's keyboard port. The wireless aspect is achieved either by radio frequency (RF) or by infrared (IR) signals sent and received from both the keyboard and the unit attached to the computer. A wireless keyboard may use an industry standard RF, called Bluetooth. With Bluetooth, the transceiver may be built into the computer. However, a wireless keyboard needs batteries to work and may pose a security problem due to the risk of data "eavesdropping" by hackers. Wireless solar keyboards charge their batteries from small solar panels using sunlight or standard artificial lighting. An early example of a consumer wireless keyboard is that of the Olivetti Envision.
Alternative text-entering methods
An on-screen keyboard controlled with the mouse can be used by users with limited mobility.
Speech recognition converts speech into machine-readable text (that is, a string of character codes). This technology has also reached an advanced state and is implemented in various software products. For certain uses (e.g., transcription of medical or legal dictation; journalism; writing essays or novels) speech recognition is starting to replace the keyboard. However, the lack of privacy when issuing voice commands and dictation makes this kind of input unsuitable for many environments.
Pointing devices can be used to enter text or characters in contexts where using a physical keyboard would be inappropriate or impossible. These accessories typically present characters on a display, in a layout that provides fast access to the more frequently used characters or character combinations. Popular examples of this kind of input are Graffiti, Dasher and on-screen virtual keyboards.
Other issues
Keystroke logging
Unencrypted wireless bluetooth keyboards are known to be vulnerable to signal theft by placing a covert listening devices in the same room as the keyboard to sniff and record bluetooth packets for the purpose of logging keys typed by the user. Microsoft wireless keyboards 2011 and earlier are documented to have this vulnerability.Keystroke logging (often called keylogging) is a method of capturing and recording user keystrokes. While it is used legally to measure employee productivity on certain clerical tasks, or by law enforcement agencies to find out about illegal activities, it is also used by hackers for various illegal or malicious acts. Hackers use keyloggers as a means to obtain passwords or encryption keys and thus bypass other security measures.
Keystroke logging can be achieved by both hardware and software means. Hardware key loggers are attached to the keyboard cable or installed inside standard keyboards. Software keyloggers work on the target computer's operating system and gain unauthorized access to the hardware, hook into the keyboard with functions provided by the OS, or use remote access software to transmit recorded data out of the target computer to a remote location. Some hackers also use wireless keylogger sniffers to collect packets of data being transferred from a wireless keyboard and its receiver, and then they crack the encryption key being used to secure wireless communications between the two devices.
Anti-spyware applications are able to detect many keyloggers and cleanse them. Responsible vendors of monitoring software support detection by anti-spyware programs, thus preventing abuse of the software. Enabling a firewall does not stop keyloggers per se, but can possibly prevent transmission of the logged material over the net if properly configured. Network monitors (also known as reverse-firewalls) can be used to alert the user whenever an application attempts to make a network connection. This gives the user the chance to prevent the keylogger from "phoning home" with his or her typed information. Automatic form-filling programs can prevent keylogging entirely by not using the keyboard at all. Most keyloggers can be fooled by alternating between typing the login credentials and typing characters somewhere else in the focus window.
Keyboards are also known to emit electromagnetic signatures that can be detected using special spying equipment to reconstruct the keys pressed on the keyboard. Neal O'Farrell, executive director of the Identity Theft Council, revealed to InformationWeek that "More than 25 years ago, a couple of former spooks showed me how they could capture a user's ATM PIN, from a van parked across the street, simply by capturing and decoding the electromagnetic signals generated by every keystroke," O'Farrell said. "They could even capture keystrokes from computers in nearby offices, but the technology wasn't sophisticated enough to focus in on any specific computer."
Physical injury
Proper ergonomic design of computer keyboard desks is necessary to
prevent repetitive strain injuries, which can develop over time and can
lead to long-term disability.
Research suggests that the upright position formerly advocated can lead
to degenerative disc disease, and that a 45 degree reclined position is
healthier.
Some adaptive technology ranging from special keyboards, mouse replacements and pen tablet interfaces to speech recognition software can reduce the risk of injury. Pause software reminds the user to pause frequently. Switching to a much more ergonomic mouse, such as a vertical mouse or joystick mouse may provide relief. Switching from using a mouse to using a stylus pen with graphic tablet or a trackpad can lessen the repetitive strain on the arms and hands.
Pathogen transmission
Some keyboards were found to contain five times more potentially harmful germs than a toilet seat. This can be a concern when using shared keyboards; the keyboards can serve as vectors for pathogens that cause the cold, flu, and other communicable diseases easily spread by indirect contact.Wireless keyboard
Visual depiction of a compact wireless keyboard
A wireless keyboard is a computer keyboard that allows the user to communicate with computers, tablets, or laptops with the help of radio frequency (RF), infrared (IR) or Bluetooth technology. It is common for wireless keyboards available these days to be accompanied by a wireless mouse.
Wireless keyboards based on infrared technology use light waves to transmit signals to other infrared-enabled devices. But, in case of radio frequency technology, a wireless keyboard communicates using signals which range from 27 MHz to up to 2.4 GHz. Most wireless keyboards today work on 2.4 GHz radio frequency. Bluetooth is another technology that is being widely used by wireless keyboards. These devices connect and communicate to their parent device via the bluetooth protocol.
A wireless keyboard can be connected using RF technology with the help of two parts, a transmitter and a receiver. The radio transmitter is inside the wireless keyboard. The radio receiver plugs into a keyboard port or USB port. Once the receiver and transmitter are plugged in, the computer recognizes the keyboard and mouse as if they were connected via a cable.
Types
A wireless keyboard combo
- Standard size wireless keyboard: These keyboards are standard size wireless keyboard.
- Foldable - hinges allow for folding of keyboard
- Portable keyboard with touchpad: Keyboard Comes with integrated touch pad.
- Portable with Stand - comes with tablet/smartphone stand
- Roll-up wireless keyboard: wireless keyboard that can be rolled up when not in use.
- Mini Wireless Keyboard: Palm sized keyboard with an integrated touch pad; uses thumb typing
- slim keyboard
- With touch pad - combined keyboard and touchpad
Bluetooth keyboard
Bluetooth keyboard
A Bluetooth keyboard is a wireless keyboard that connects and communicates with its parent device via the Bluetooth protocol. These devices are widely used with such portable devices as smart phones and tablets, though they are also used with laptops and ultrabooks. Bluetooth keyboards became popular in 2011, coincident with the popularity of portable devices.
In computing, a keyboard shortcut is a sequence or combination of keystrokes on a computer keyboard which invokes commands in software.
Most keyboard shortcuts require the user to press a single key or a sequence of keys one after the other. Other keyboard shortcuts require pressing and holding several keys simultaneously (indicated in the tables below by this sign: +). Keyboard shortcuts may depend on the keyboard layout (localization)






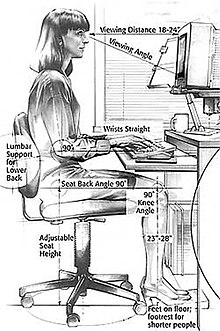



Go Look Importantbook: A Series Of Computer Keyboards To Modern Keyboards And Working Principles So Do Virtual Laser Keyboard Amnimarjeslow Al Do Four Do Al One Ljbusaf Thankyume Orbit >>>>> Download Now
BalasHapus>>>>> Download Full
Go Look Importantbook: A Series Of Computer Keyboards To Modern Keyboards And Working Principles So Do Virtual Laser Keyboard Amnimarjeslow Al Do Four Do Al One Ljbusaf Thankyume Orbit >>>>> Download LINK
>>>>> Download Now
Go Look Importantbook: A Series Of Computer Keyboards To Modern Keyboards And Working Principles So Do Virtual Laser Keyboard Amnimarjeslow Al Do Four Do Al One Ljbusaf Thankyume Orbit >>>>> Download Full
>>>>> Download LINK 2E