Telephone
people have devised methods for communicating over long distances. The earliest methods involved crude systems such as drum beating or smoke signaling. These systems evolved into optical telegraphy, and by the early 1800s, electric telegraphy. The first simple telephones, which were comprised of a long string and two cans, were known in the early eighteenth century.
A working electrical voice-transmission system was first demonstrated by Johann Philipp Reis in 1863. His machine consisted of a vibrating membrane that opened or closed an electric circuit. While Reis only used his machine to demonstrate the nature of sound, other inventors tried to find more practical applications of this technology. They were found by Alexander Graham Bell in 1876 when he was awarded a patent for the first operational telephone. This invention proved to revolutionize the way people communicate throughout the world.
Bell's interest in telephony was primarily derived from his background in vocal physiology and his speech instruction to the deaf. His breakthrough experiment occurred on June 2, 1875. He and his assistant, Thomas Watson, were working on a harmonic telegraph. When a reed stuck on Watson's transmitter an intermittent current was converted to a continuous current. Bell was able to hear the sound on his receiver confirming his belief that sound could be transmitted and reconverted through an electric wire by using a continuous electric current.
The original telephone design that Bell patented was much different than the phone we know today. In a real sense, it was just a modified version of a telegraph. The primary difference was that it could transmit true sound. Bell continued to improve upon his design. After two years, he created a magnetic telephone which was the precursor to modern phones. This design consisted of a transmitter, receiver, and a magnet. The transmitter and receiver each contained a diaphragm, which is a metal disk. During a phone call, the vibrations of the caller's voice caused the diaphragm in the transmitter to move. This motion was transferred along the phone line to the receiver. The receiving diaphragm began vibrating thereby producing sound and completing the call.
While the magnetic phone was an important breakthrough, it had significant drawbacks. For example, callers had to shout to overcome noise and voice distortions. Additionally, there was a time lapse in the transmission which resulted in nearly incoherent conversations. These problems were eventually solved as the telephone underwent numerous design changes. The first phones made available to consumers used a single microphone. This required the user to speak into it and then put it to the ear to listen. Thomas Edison introduced a model that had a moveable listening earpiece and stationary speaking tube. When placing a call, the receiver was lifted and the user was connected directly to an operator who would then switch wires manually to transmit. In 1878, the first manual telephone exchange was opened. It served 21 customers in New Haven, Connecticut. Use of the telephone spread rapidly and in 1891, the first automatic number calling mechanism was introduced.
Long-distance service was first made available in 1881. However, the transmission rates were not good and it was difficult to hear. In 1900, two workers at Bell System designed loading coils that could minimize distortions. In 1912, the vacuum tube was adapted to the phone as an amplifier. This made it possible to have a transcontinental phone line, first demonstrated in 1915. In 1956, a submarine cable was laid across the Atlantic to allow transatlantic telephone communication. The telecommunication industry was revolutionized in 1962 when orbiting communication satellites were utilized. In 1980, a fiber-optic system was introduced, again revolutionizing the industry.
Background
Telephones still operate on the same basic principles that Bell introduced over one hundred years ago. If a person wishes to make a call, they pick up the handset. This causes the phone to be connected to a routing network. When the numbers are pressed on a touch-tone keypad, signals are sent down the phone line to the routing station. Here, each digit is recognized as a combination of tone frequencies. The specific number combination causes a signal to be sent to another phone causing it to ring. When that phone is picked up, a connection between the two phones is initiated.
The mouthpiece acts as a microphone. Sound waves from the user's voice cause a thin, plastic disk inside the phone to vibrate. This changes the distance between the plastic disk and another metal disk. The intensity of an electric field between the two disks is changed as a result and a varying electric current is sent down the phone line. The receiver on the other phone picks up this current. As it enters the receiver, it passes through a set of electromagnets. These magnets cause a metal diaphragm to vibrate. This vibration reproduces the voice that initiated the current. An amplifier in the receiver makes it easier to hear. When one of the phones is hung up the electric current is broken, causing all of the routing connections to be released.
 Eiisha Gray
Eiisha Gray
Elisha Gray was Alexander Graham Bell's principle rival, first for invention of the harmonic telegraph and then of the telephone. He was a prolific inventor, granted some 70 patents during his lifetime. Born in Barnesville, Ohio, on August 2, 1935, and brought up on a farm, Gray had to leave school early when his father died but later continued his studies at Oberlin College, where he concentrated on physical sciences, especially electricity, and supported himself as a carpenter.
After leaving Oberlin, Gray continued his electrical experiments, concentrating on telegraphy. In 1867, he patented an improved telegraph relay, and later, a telegraph switch, an "annunciator" for hotels and large business offices, a telegraphic repeater, and a telegraph line printer. He also experimented with ways to transmit multiple, separate messages simultaneously across a single wire, a subject that was also engaging the efforts of Bell. Gray prevailed, filing his harmonic telegraph patent application in February 1875, two days before Bell's similar application.
Gray now began investigating ways to transmit voice messages, soon developing a telephone design that featured a liquid transmitter and variable resistance. In one of the most remarkable coincidences in the history of invention, Gray filed notice of his intent to patent his device on February 14, 1876—just two hours after Bell had filed his own telephone patent at the same office. Western Union Telegraph Company purchased the rights to Gray's telephone and went into the telephone business; the Bell Telephone Company launched a bitter lawsuit in return.
Meanwhile, Gray had been a founding partner in 1869 of Gray and Barton, an electric-equipment shop in Cleveland, Ohio. This became Western Electric Manufacturing of Chicago in 1872, which evolved into Western Electric Company, which, ironically, became the largest single component of Bell Telephone in 1881.
The system of transmission presented describes what happens during a local call. It varies slightly for other types of calls such as long distance or cellular. Long distance calls are not always connected directly through wires. In some cases, the signal is converted
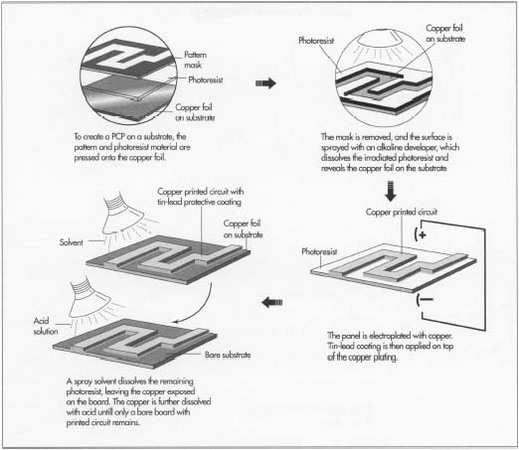 The electronic components of the telephone are sophisticated and use the latest in electronic processing technology. The circuit board is produced the same way that boards are made for other types of electronic equipment. The preprinted, nonconductive board is passed through a series of machines that place the appropriate chips, diodes, capacitors, and other electronic parts in the appropriate places. To affix the electronic parts to the board, a wave soldering machine is used.
to a satellite dish signal and transmitted via a satellite. For cellular phones, the signal is sent to a cellular antenna. Here, it is sent via radio waves to the appropriate cell phone.
The electronic components of the telephone are sophisticated and use the latest in electronic processing technology. The circuit board is produced the same way that boards are made for other types of electronic equipment. The preprinted, nonconductive board is passed through a series of machines that place the appropriate chips, diodes, capacitors, and other electronic parts in the appropriate places. To affix the electronic parts to the board, a wave soldering machine is used.
to a satellite dish signal and transmitted via a satellite. For cellular phones, the signal is sent to a cellular antenna. Here, it is sent via radio waves to the appropriate cell phone.

Eiisha Gray
Elisha Gray was Alexander Graham Bell's principle rival, first for invention of the harmonic telegraph and then of the telephone. He was a prolific inventor, granted some 70 patents during his lifetime. Born in Barnesville, Ohio, on August 2, 1935, and brought up on a farm, Gray had to leave school early when his father died but later continued his studies at Oberlin College, where he concentrated on physical sciences, especially electricity, and supported himself as a carpenter.
After leaving Oberlin, Gray continued his electrical experiments, concentrating on telegraphy. In 1867, he patented an improved telegraph relay, and later, a telegraph switch, an "annunciator" for hotels and large business offices, a telegraphic repeater, and a telegraph line printer. He also experimented with ways to transmit multiple, separate messages simultaneously across a single wire, a subject that was also engaging the efforts of Bell. Gray prevailed, filing his harmonic telegraph patent application in February 1875, two days before Bell's similar application.
Gray now began investigating ways to transmit voice messages, soon developing a telephone design that featured a liquid transmitter and variable resistance. In one of the most remarkable coincidences in the history of invention, Gray filed notice of his intent to patent his device on February 14, 1876—just two hours after Bell had filed his own telephone patent at the same office. Western Union Telegraph Company purchased the rights to Gray's telephone and went into the telephone business; the Bell Telephone Company launched a bitter lawsuit in return.
Meanwhile, Gray had been a founding partner in 1869 of Gray and Barton, an electric-equipment shop in Cleveland, Ohio. This became Western Electric Manufacturing of Chicago in 1872, which evolved into Western Electric Company, which, ironically, became the largest single component of Bell Telephone in 1881.

The electronic components of the telephone are sophisticated and use the latest in electronic processing technology. The circuit board is produced the same way that boards are made for other types of electronic equipment. The preprinted, nonconductive board is passed through a series of machines that place the appropriate chips, diodes, capacitors, and other electronic parts in the appropriate places. To affix the electronic parts to the board, a wave soldering machine is used.
Raw Materials
A variety of raw materials are used for making telephones. Materials range from glass, ceramics, paper, metals, rubber and plastics. The primary components on the circuit board are made from silicon. The outer housing of the phone is typically made of a strong, high-impact resistant polymer. To modify the characteristics of this polymer, various fillers and colorants are used. The speakers require magnetic materials.
Design
Modern telephones come in many shapes and sizes, but they all have the same general features. They consist of a single handset which contains both the transmitter and receiver. The handset rests on the base when the phone is not in use. They also have a dialing system which is either a rotary dial or a touch-tone keypad. Recently, rotary phones have been phased out in favor of the more useful keypad. To alert the consumer that they have an incoming call, phones are equipped with ringers. A wide variety of specialized phones are also produced. Speaker phones are made to allow the consumer to carry on a telephone conversation
 The individual parts of the telephone are assembled both automatically and manually. The transmitter and receiver are put together by machines. These parts are then fed onto the main assembly line and inserted into the molded headset. Similarly, the internal electronics, including the touch-tone pad, are inserted into the main housing and attached with screws.
without holding the handset. Cordless phones are also available. These models do not require direct connection of the handset to the base. Instead the user's voice is converted to radio waves and then sent to the phone base. This, in turn, gets converted to an electric signal and sent down the phone lines. Another type of common phone is the cellular phone. These phones use radio waves and an antenna system to communicate between phones.
The individual parts of the telephone are assembled both automatically and manually. The transmitter and receiver are put together by machines. These parts are then fed onto the main assembly line and inserted into the molded headset. Similarly, the internal electronics, including the touch-tone pad, are inserted into the main housing and attached with screws.
without holding the handset. Cordless phones are also available. These models do not require direct connection of the handset to the base. Instead the user's voice is converted to radio waves and then sent to the phone base. This, in turn, gets converted to an electric signal and sent down the phone lines. Another type of common phone is the cellular phone. These phones use radio waves and an antenna system to communicate between phones.

The individual parts of the telephone are assembled both automatically and manually. The transmitter and receiver are put together by machines. These parts are then fed onto the main assembly line and inserted into the molded headset. Similarly, the internal electronics, including the touch-tone pad, are inserted into the main housing and attached with screws.
The Manufacturing
Process
Since there are so many different parts that go into making a telephone, the components are typically produced by different companies and then assembled by the phone manufacturer. The main components include the internal electronics, the handset, and the various plastic parts.
Plastic parts
- 1 To produce the plastic parts like the base, handset casing, and push buttons, injection molding is typically done. In this process, pellets of plastic polymer are put into the hopper of an injection molding machine. They then pass through a hydraulically controlled screw and are melted. While the screw rotates, the melted plastic is moved through a nozzle and injected into a mold. Just prior to this injection, the two halves of a mold are brought together to form a cavity which matches the shape of the telephone part. While inside the mold, the plastic is held under pressure for a set amount of time and then allowed to cool. As it cools, it hardens and forms into the shape of the part. This mold is coated with chromium to create a shiny surface.
- 2 After a short while, the mold halves are opened and the part is ejected. The mold then closes again and the process begins again. At this point in process, many of the parts are manually inspected to ensure that no significantly damaged parts are used. If there are damaged parts, they are set aside to be remelted and reformed into new parts.
Internal electronics
- 3 The electronic components of the telephone are sophisticated and use the latest in electronic processing technology. The circuit board is produced the same way that boards are made for other types of electronic equipment. The process begins with a board made of non-conducting material that has the electronic configuration printed on it using a conducting material. This board is then passed through a series of machines that place the appropriate chips, diodes, capacitors and other electronic parts in the appropriate places. To prevent damage caused by dust, the process is completed in a specially cleaned room. When completed, it is sent to the next step for soldering.
- 4 To affix the electronic parts to the board, a wave soldering machine is used. Before being put into the machine, the board is washed to remove contaminants. Upon entering, the board is heated using infrared heat. The underside of the board is passed over a wave of molten solder and through capillary action, all of the necessary spots are filled. As the board is allowed to cool, the solder hardens and the pieces stay in place. This creates an electrical connection between the printed circuits and the components.
Assembly and Packaging
- 5 The individual parts are assembled both automatically and manually. The transmitter and receiver are put together by machines. These parts are then fed onto the main assembly line and inserted into the molded headset. Similarly, the internal electronics, including the touch-tone pad, are inserted into the main housing and attached with screws. The headset is then put on the phone base and the phone chord may also be put on.
- 6 After all of the phone pieces are assembled, the completed phones are put in final packaging. Typically, they are wrapped in plastic and put in boxes. A packaging material such as polystyrene is also included to protect the device from damage during shipping. An owner's manual or other literature is included and the box is sealed with tape. The boxes are stacked on pallets, shipped to distributors and finally, customers.
Quality Control
To ensure the quality of each telephone, visual and electrical inspections are done throughout the entire production process and most flaws are detected. Additionally, the each completed phone is tested to make sure it works. Often these tests are done under different environmental conditions such as excessive heat and humidity to simulate the extremes that are experienced in a real life setting. Plastic parts are given torture tests to ensure they will still function even after a level of consumer abuse. For example, the numbers on a touch tone pad are put under a rubber-finger that taps the buttons enough times that it equals forty years of dialing. Since many of the parts that make up the telephone are produced by subcontractors, telephone manufacturers rely heavily on these suppliers for good quality. To ensure consistent manufacturing, most telephone makers set quality specifications for individual parts that the suppliers must meet.
The Future
Telephone technology is improving rapidly. In the future, cordless phones will be designed to be smaller and lighter. They will have wider transmission and better reception ranges. The sound quality will also be improved. Other technologies that integrate the phone with computers and cable television will be commonplace. Dialing systems will also be improved. In a recent demonstration, one company showed a technology that accepted voice command to dial a phone number.
XXX . V Mobile Phones

Mobile phones are very useful for people with low vision and there are plenty of models to choose from with different levels of functionality.
If a mobile is primarily required for making phone calls, a simple phone with basic functions is ideal. It should have large, high contrast keys and display, loud ring tones and emergency call functions. Some phones can be personalised to have just a few pre-programmed numbers that are accessible at the push of a single button.
If a mobile is primarily required for making phone calls, a simple phone with basic functions is ideal. It should have large, high contrast keys and display, loud ring tones and emergency call functions. Some phones can be personalised to have just a few pre-programmed numbers that are accessible at the push of a single button.
If a mobile phone is needed for additional functions, select a model with screen reader software. The phone will then speak all of the information on the screen, including contacts, caller information and text messages. It should also have a screen enlargement function, to increase the font size on the screen, and a high contrast display panel for easier reading.
Smart Phones, such as the Apple iPhones, have a broad range of features including functions to support people with low vision. Some of these features are magnification and speech accessibility for voice navigation commands.In addition to the usual tools of phone, email and web accessibility, smart phones can provide GPS navigation and support applications such as talking books.
XXX . V0 TELEVISION AND RADIO
Television and Radio

When it comes to watching television, there are many large screen options available, along with universal remote controls that have large buttons. When choosing a television, consider an LED TV, which offers more vibrant colours and sharper contrast.
Some televisions now come with built-in voice guidance. Voice guidance speaks aloud onscreen information using text-to-speech technology and enables blind and visually impaired viewers to control their TV by voice, for example, changing channels and searching for programs.
Digital radios provide very clear sound output. There is now a wide range to choose from including those with large print, large buttons and high colour contrast.
Radio for the Print Handicapped (RPH) provides a radio reading service for people who cannot see, handle or understand printed material. Programming includes readings from daily newspapers and articles from magazines as well as book readings and extracts from a variety of publications on topics such as health, music, art, entertainment, science.
Audio Technology Audio books Audio books, or talking books, can be sourced from a range of providers including low vision agencies, council libraries and audio book websites. The content can be played on a range of devices including standard CD players, MP3 devices and tablet computers. Some newspapers are also available in audio format. Navigator audio book The Navigator is a ‘low tech’ portable audio book device. Digital files of books or newspapers are loaded on to the Navigator from a computer. It can hold an average of five books in its memory (approximately thirty hours of listening). The Navigator is available from Macular Disease Foundation Australia and also in selected libraries around Australia and some low vision organisations. Macular Disease Foundation Australia’s Navigator Home Access Program allows users to access audio books and newspapers from a website and download them onto the Navigator audio book unit. The download process requires some computer experience so some people with low vision may require assistance from family or friends. Once loaded, the Navigator is very easy to use and, as it is light and portable, it can be used at home or out and about
XXX . V00 Computers and Software

XXX . V000 Electronic Magnifiers
Some televisions now come with built-in voice guidance. Voice guidance speaks aloud onscreen information using text-to-speech technology and enables blind and visually impaired viewers to control their TV by voice, for example, changing channels and searching for programs.
Digital radios provide very clear sound output. There is now a wide range to choose from including those with large print, large buttons and high colour contrast.
Radio for the Print Handicapped (RPH) provides a radio reading service for people who cannot see, handle or understand printed material. Programming includes readings from daily newspapers and articles from magazines as well as book readings and extracts from a variety of publications on topics such as health, music, art, entertainment, science.
Audio Technology Audio books Audio books, or talking books, can be sourced from a range of providers including low vision agencies, council libraries and audio book websites. The content can be played on a range of devices including standard CD players, MP3 devices and tablet computers. Some newspapers are also available in audio format. Navigator audio book The Navigator is a ‘low tech’ portable audio book device. Digital files of books or newspapers are loaded on to the Navigator from a computer. It can hold an average of five books in its memory (approximately thirty hours of listening). The Navigator is available from Macular Disease Foundation Australia and also in selected libraries around Australia and some low vision organisations. Macular Disease Foundation Australia’s Navigator Home Access Program allows users to access audio books and newspapers from a website and download them onto the Navigator audio book unit. The download process requires some computer experience so some people with low vision may require assistance from family or friends. Once loaded, the Navigator is very easy to use and, as it is light and portable, it can be used at home or out and about
XXX . V00 Computers and Software

Technology has changed the way we undertake many tasks, from accessing information to driving a car.
Even if it hasn’t been part of your education or life experience so far, it is possible to learn the skills necessary to make use of computer technology and software. Talk to one of the many low vision service providers about computer training programs and typing courses. Local Computer Pals clubs for seniors, which offer a fun and supportive environment, may also be suitable for learning computer skills. Technical Aid to the Disabled (TAD) can help to provide affordable computer packages for people with a disability.
Another excellent resource is Media Access Australia (MAA). MAA is a not-for-profit organisation devoted to increasing access to media for people with disabilities. Their website contains information on assistive technology.
Additionally, starting with both magnification and a reader may simplify the transition to speech only if vision deteriorates further.
Some of the popular screen magnifiers and readers are Guide, Zoom Text and Jaws.
Guide
Guide is a good program to use for those who are not familiar with using the computer but want to learn to send and receive emails and browse the Iinternet. It is specifically designed for beginners, with an easy to use menu, built in magnification, colour contrast and text-to-speech capability.
Zoom Text
Zoom Text is suitable for people using Windows operating systems who need to magnify images on the computer. It has magnification capabilities up to 60x, as well as enhanced mouse pointers and cursors. Zoom Text also has the ability to change background colours to increase contrast, and an optional text-to-speech output.
JAWS
JAWS works with computers to provide access to operating systems, software applications and the internet. JAWS has a text-to-speech application that vocalises everything on screen in an orderly way. It also supports a large number of Braille applications.
Microsoft Windows has a built-in narrator, and has third party software support, which allows for greater access.
Apple Mac has built-in full-screen magnification, a voice over feature that converts text-to-speech, voice command capability and high-contrast settings.
Non-Visual Desktop Access – or NVDA - provides Windows users with a free text-to-speech program.
Web Anywhere is a text-to-speech tool that integrates into the web browser in virtually any operating system, providing free basic voice access to the internet. The voice software can work on almost any computer with sound and will start almost immediately after download.
System Access to Go is an online screen reader, available from any Internet Explorer connected Windows Computer.
Even if it hasn’t been part of your education or life experience so far, it is possible to learn the skills necessary to make use of computer technology and software. Talk to one of the many low vision service providers about computer training programs and typing courses. Local Computer Pals clubs for seniors, which offer a fun and supportive environment, may also be suitable for learning computer skills. Technical Aid to the Disabled (TAD) can help to provide affordable computer packages for people with a disability.
Another excellent resource is Media Access Australia (MAA). MAA is a not-for-profit organisation devoted to increasing access to media for people with disabilities. Their website contains information on assistive technology.
Maximising vision using computer technology
There are many ways you can maximise remaining vision by using technology, including choosing a large screen to increase the viewing area and increasing the size of items displayed on the screen.
To make type easier to read, choose simple fonts without decorative curves, such as Arial or Calibri, and type in upper and lower case instead of all capitals. Add extra space between words and lines of text.
To make type easier to read, choose simple fonts without decorative curves, such as Arial or Calibri, and type in upper and lower case instead of all capitals. Add extra space between words and lines of text.
The following modifications will help you get the most from your computer:
- A large monitor to increase your viewing area
- A large print keyboard or large font keyboard stickers applied to the keys
- Software that increases the cursor size
- If the mouse or cursor is difficult to use, it may be easier to learn to touch type and use keyboard commands
- Enlarge the toolbar display
- Change the colour contrast
Computer technology for people with low vision
Electronic note takers
An electronic note taker is basically an adapted personal data service. Users can do the same tasks that a typical personal data device allows including: taking notes, reading email, diary functions, calculator, playing music, or digital books and data transfer to or from computers. Because the electronic note takers are adapted for persons who are blind or vision impaired, they have built in speech output.Tablets and small personal computers
Netbooks, ultrabooks, and tablet personal computers are essentially just small computers. They are highly portable which means that those with low vision can readily access low vision technology when out and about.Software options for people with low vision
Screen magnification software
Screen magnification software increases the size of the image displayed on the screen. This means only a portion of the original screen image can be seen at one time. The mouse or keyboard can then be used to move the magnified window to view other parts of the original screen image.Screen reading software
Screen reading software is also available to translate text into speech and is designed for people with very little usable vision. They may also be built in to some websites such as this one – by pressing the ‘Listen’ button at the top of the screen, the text will be read aloud.Screen magnifier and reader
At times, a program with a screen magnifier AND speech reader may help. For example, Type Echo - hearing text as it is typed can be useful for new or slow typists. Listening to long documents or web pages may be less tiring than reading with a screen magnifier.Additionally, starting with both magnification and a reader may simplify the transition to speech only if vision deteriorates further.
| Function | ||
| Program | Screen magnifier | Screen reader |
| Guide Zoom Text MAGic | ✔ | ✔ |
| Magnifying Glass Pro Mouse Magnifier Utility Lightning | ✔ | |
| JAWS Windows-Eyes Thunder Dragon Dictate | ✔ | |
Popular screen magnifiers and readers
Some of the popular screen magnifiers and readers are Guide, Zoom Text and Jaws.Guide
Guide is a good program to use for those who are not familiar with using the computer but want to learn to send and receive emails and browse the Iinternet. It is specifically designed for beginners, with an easy to use menu, built in magnification, colour contrast and text-to-speech capability.
Zoom Text
Zoom Text is suitable for people using Windows operating systems who need to magnify images on the computer. It has magnification capabilities up to 60x, as well as enhanced mouse pointers and cursors. Zoom Text also has the ability to change background colours to increase contrast, and an optional text-to-speech output.
JAWS
JAWS works with computers to provide access to operating systems, software applications and the internet. JAWS has a text-to-speech application that vocalises everything on screen in an orderly way. It also supports a large number of Braille applications.
Free software options
There are a number of free software options to choose from, provided by suppliers that include Microsoft, Apple and Linux.Microsoft Windows has a built-in narrator, and has third party software support, which allows for greater access.
Apple Mac has built-in full-screen magnification, a voice over feature that converts text-to-speech, voice command capability and high-contrast settings.
Non-Visual Desktop Access – or NVDA - provides Windows users with a free text-to-speech program.
Web Anywhere is a text-to-speech tool that integrates into the web browser in virtually any operating system, providing free basic voice access to the internet. The voice software can work on almost any computer with sound and will start almost immediately after download.
System Access to Go is an online screen reader, available from any Internet Explorer connected Windows Computer.
Web browsers
Whether you use Windows or Mac, you access the Internet through a web browser. There are several web browsers available, the most popular being Internet Explorer, Mozilla Firefox and Chrome. Each contains a variety of features which can help people with low vision who rely on the use of a keyboard or need to make a webpage easier to see.XXX . V000 Electronic Magnifiers



Tidak ada komentar:
Posting Komentar