
Online banking
The basic theory of online banking in electronic equipment :
An A/D converter converts an analog signal into a stream of digital numbers, each representing the analog signal's amplitude at a moment in time. Each number is called a "sample." The number sample per second is called the sampling rate, measured in samples per second. The frequency range where the measured response is above a certain limit (for instance -3dB bandwidth describes the frequency range where the measured response is over -3dB).
ADX - Time-interleaving Technology for Analog-to-Digital Converters (ADCs)
Time‑interleaving of analog‑to‑digital converters (ADCs) is a way to increase the overall system sample rate by using several ADCs in parallel. The challenge is to handle the mismatch between the individual ADCs, especially at higher frequencies.
Higher speedThe SP Devices interleaving technology provides our customers with a method of increasing the sampling rates of their A/D solutions. The interleaving process involves the signal being sampled at different times by one of a number of parallel ADCs. The overall sampling rate is in this way multiplied by the number of ADCs. |
Handling the mismatch
The challenge with interleaving is to correct for the manufacturing variations of the characteristics of the individual ADC, in order to obtain the optimal resolution. The variation after correction must be less than 0.01% in order to achieve the successful interleaving of a typical 14‑bit ADC! Furthermore, these variations depend on temperature and age, making the corrections required even more complex.
The ADX technology
ADX is a digital block for the post‑processing of the output from interleaved ADCs that can be used with any ADC. The ADX technology features both the estimation of mismatch error and the reconstruction of the signal with all mismatch errors suppressed.The proprietary technology of ADX continuously provides a background estimate of the gain, offset and time‑skew errors of the ADCs without the need for any special calibration signal or post‑production trimming. Our patented reconstructor block recreates the signal with minimal latency.
Availability
ADX is available as software, FPGA and silicon IP. There are also several evaluation modules available thatLinearization of ADCs - ADL
Digital post‑linearization increases the effective resolution of analog‑to‑digital conversions. The linearization technology developed by SP Devices suppresses low order non‑linearities of high‑performance ADCs and non‑linearities caused by pre‑ADC analog components (such as amplifiers, filters and buffers).
The transfer function of ADCs
The SP Devices linearization technology increases the useful dynamic range of A/D solutions. An ADC can be viewed as a transfer function from the analog to digital domain. An ideal ADC has a completely linear transfer function. |  |
All ADCs are non-linearHowever, the transfer functions of all real ADCs suffer from non‑linearities. These non‑linearities limit the dynamic range of the ADC and often limit the usefulness of many applications.
|  |
The ADL technologyADL is a digital block for the post‑processing of the output from ADCs that enhances the linearity of the ADC. ADL improves the dynamic range in most applications by a factor of at least two.
| |
ADL compensates
|  |
ADL improvement results
The plots below show the result of applying ADL to the output of high-speed 16-bit ADCs mounted on reference boards available from each of the ADC manufacturers. The boards were operated at a sampling rate of 130 MSPS, and the plots show two-tone tests in the 5th Nyquist zone before (left) and after (right) being corrected by ADL. In this Nyquist zone, distortion is dominated by low order harmonic distortion, (HD2 and HD3). The plots show that regardless of the ADC model, the 2:nd and 3:rd order distortion spurs are attenuated to a level close to -100 dBFS. This means that the usable bandwidth is extended up to the 5th Nyquist Zone.Analog Devices AD9461

National Semiconductor ADC16V130

Texas Instruments ADS5483

Linear Technology LTC2209


IQE - Digital I/Q Imbalance correction IP for Wireless Applications
The IQE 100 is a wideband imbalance correction IP, that digitally match in-phase and quadrature signal paths in radio architectures employing complex demodulators such as direct down-conversion receivers. The IQE 100 IP core is available as FPGA IP and as a GDSII macro block.
 Distortion due to signal path imbalances is attenuated by 20 - 50 dB covering up to 100 MHz signal bandwidth. The IP is fully autonomous and offers a unique balancing performance for multi-band radio solutions. IQE 100 does not require any specific calibration signal nor does it interrupt normal operation of the receiver.
Distortion due to signal path imbalances is attenuated by 20 - 50 dB covering up to 100 MHz signal bandwidth. The IP is fully autonomous and offers a unique balancing performance for multi-band radio solutions. IQE 100 does not require any specific calibration signal nor does it interrupt normal operation of the receiver.
 The figure depicts a complex baseband spectrum of two wideband signals. The IQ imbalance creates images
The figure depicts a complex baseband spectrum of two wideband signals. The IQ imbalance creates images
 Distortion due to signal path imbalances is attenuated by 20 - 50 dB covering up to 100 MHz signal bandwidth. The IP is fully autonomous and offers a unique balancing performance for multi-band radio solutions. IQE 100 does not require any specific calibration signal nor does it interrupt normal operation of the receiver.
Distortion due to signal path imbalances is attenuated by 20 - 50 dB covering up to 100 MHz signal bandwidth. The IP is fully autonomous and offers a unique balancing performance for multi-band radio solutions. IQE 100 does not require any specific calibration signal nor does it interrupt normal operation of the receiver. The figure depicts a complex baseband spectrum of two wideband signals. The IQ imbalance creates images
The figure depicts a complex baseband spectrum of two wideband signals. The IQ imbalance creates images Online banking
Online banking, also known as internet banking, e-banking or virtual banking, is an electronic payment system that enables customers of a bank or other financial institution to conduct a range of financial transactions through the financial institution's website. The online banking system will typically connect to or be part of the core banking system operated by a bank and is in contrast to branch banking which was the traditional way customers accessed banking services.
To access a financial institution's online banking facility, a customer with internet access will need to register with the institution for the service, and set up a password and other credentials for customer verification. The credentials for online banking is normally not the same as for telephone or mobile banking. Financial institutions now routinely allocate customers numbers, whether or not customers have indicated an intention to access their online banking facility. Customer numbers are normally not the same as account numbers, because a number of customer accounts can be linked to the one customer number. Technically, the customer number can be linked to any account with the financial institution that the customer controls, though the financial institution may limit the range of accounts that may be accessed to, say, cheque, savings, loan, credit card and similar accounts.
The customer visits the financial institution's secure website, and enters the online banking facility using the customer number and credentials previously set up. The types of financial transactions which a customer may transact through online banking are determined by the financial institution, but usually includes obtaining account balances, a list of the recent transactions, electronic bill payments and funds transfers between a customer's or another's accounts. Most banks also enable a customer to download copies of bank statements, which can be printed at the customer's premises (some banks charge a fee for mailing hard copies of bank statements). Some banks also enable customers to download transactions directly into the customer's accounting software. The facility may also enable the customer to order a cheque book, statements, report loss of credit cards, stop payment on a cheque, advise change of address and other routine actions.
Today, many banks are internet-only institutions. These "virtual banks" have lower overhead costs than their brick-and-mortar counterparts. In the United States, many online banks are insured by the Federal Deposit Insurance Corporation (FDIC) and can offer the same level of protection for the customers' funds as traditional banks.
Precursors
The precursor for the modern home loan banking services were the distance banking services over electronic media from the early 1980s. The term 'online' became popular in the late 1980s and referred to the use of a terminal, keyboard and TV (or monitor) to access the banking system using a phone line. 'Home banking' can also refer to the use of a numeric keypad to send tones down a phone line with instructions to the bank. Online services started in New York in 1981 when four of the city's major banks (Citibank, Chase Manhattan, Chemical and Manufacturers Hanover) offered home banking services.[2][3][4] using the videotex system. Because of the commercial failure of videotex these banking services never became popular except in France where the use of videotex (Minitel) was subsidised by the telecom provider and the UK, where the Prestel system was used.Internet and customer reluctance
When the clicks-and-bricks euphoria hit in the late 1990s, many banks began to view web-based banking as a strategic imperative. The attraction of banks to online banking are fairly obvious: diminished transaction costs, easier integration of services, interactive marketing capabilities, and other benefits that boost customer lists and profit margins. Additionally, online banking services allow institutions to bundle more services into single packages, thereby luring customers and minimizing overhead.A mergers-and-acquisitions wave swept the financial industries in the mid- and late 1990s, greatly expanding banks' customer bases. Following this, banks looked to the Web as a way of maintaining their customers and building loyalty. A number of different factors are causing bankers to shift more of their business to the virtual realm.
While financial institutions took steps to implement e-banking services in the mid-1990s, many consumers were hesitant to conduct monetary transactions over the internet. It took widespread adoption of electronic commerce, based on trailblazing companies such as America Online, Amazon.com and eBay, to make the idea of paying for items online widespread. By 2000, 80% of U.S. banks offered e-banking. Customer use grew slowly. At Bank of America, for example, it took 10 years to acquire 2 million e-banking customers. However, a significant cultural change took place after the Y2K scare ended. In 2001, Bank of America became the first bank to top 3 million online banking customers, more than 20% of its customer base. In comparison, larger national institutions, such as Citigroup claimed 2.2 million online relationships globally, while J.P. Morgan Chase estimated it had more than 750,000 online banking customers. Wells Fargo had 2.5 million online banking customers, including small businesses. Online customers proved more loyal and profitable than regular customers. In October 2001, Bank of America customers executed a record 3.1 million electronic bill payments, totaling more than $1 billion. In 2009, a report by Gartner Group estimated that 47% of United States adults and 30% in the United Kingdom bank online.
The early 2000s saw the rise of the branch-less banks as internet only institutions. These internet-based banks incur lower overhead costs than their brick-and-mortar counterparts. In the United States, deposits at most direct banks are FDIC-insured and offer the same level of insurance protection as traditional banks.
First online banking services in the United States
Online banking was first introduced in the early 1980s in New York, United States. Four major banks — Citibank, Chase Bank, Chemical Bank and Manufacturers Hanover — offered home banking services. Chemical introduced its Pronto services for individuals and small businesses in 1983, which enabled individual and small-business clients to maintain electronic checkbook registers, see account balances, and transfer funds between checking and savings accounts. Pronto failed to attract enough customers to break even and was abandoned in 1989. Other banks had a similar experience.Since its inception in the United States, online banking has been federally governed by the Electronic Funds Transfer Act of 1978.
First online banking in the United Kingdom
Almost simultaneously with the United States, online banking arrived in the United Kingdom. The UK's first home online banking services known as Homelink was set up by Bank of Scotland for customers of the Nottingham Building Society (NBS) in 1983. The system used was based on the UK's Prestel viewlink system and used a computer, such as the BBC Micro, or keyboard (Tandata Td1400) connected to the telephone system and television set. The system allowed on-line viewing of statements, bank transfers and bill payments. In order to make bank transfers and bill payments, a written instruction giving details of the intended recipient had to be sent to the NBS who set the details up on the Homelink system. Typical recipients were gas, electricity and telephone companies and accounts with other banks. Details of payments to be made were input into the NBS system by the account holder via Prestel. A cheque was then sent by NBS to the payee and an advice giving details of the payment was sent to the account holder. BACS was later used to transfer the payment directly.Stanford Federal Credit Union was the first financial institution to offer online internet banking services to all of its members in October 1994.[6]
First online banking in France
After a test period with 2500 users starting in 1994, online banking services were launched in 1998, using Minitel terminals that were distributed freely to the population by the government.Eventually, 6.5 millions Minitels were installed in households in 1990. Online banking was one of the most popular services.
Online banking services later migrated to Internet.
Banks and the World Wide Web
Around 1994, banks saw the rising popularity of the internet as an opportunity to advertise their services. Initially, they used the internet as another brochure, without interaction with the customer. Early sites featured pictures of the bank's officers or buildings, and provided customers with maps of branches and ATM locations, phone numbers to call for further information and simple listings of products.Interactive banking on the Web
In 1995, Wells Fargo was the first U.S. bank to add account services to its website, with other banks quickly following suit. That same year, Presidential became the first U.S. bank to open bank accounts over the internet. According to research by Online Banking Report, at the end of 1999 less than 0.4% of households in the U.S. were using online banking. At the beginning of 2004, some 33 million U.S. households (31%) were using some form of online banking. Five years later, 47% of Americans used online banking, according to a survey by Gartner Group. Meanwhile, in the UK online banking grew from 63% to 70% of internet users between 2011 and 2012.Online banking facilities typically have many features and capabilities in common, but also have some that are application specific. The common features fall broadly into several categories:
- A bank customer can perform non-transactional tasks through online banking, including –
- Viewing account balances
- Viewing recent transactions
- Downloading bank statements, for example in PDF format
- Viewing images of paid cheques
- Ordering cheque books
- Download periodic account statements
- Downloading applications for M-banking, E-banking etc.
- Bank customers can transact banking tasks through online banking, including –
- Funds transfers between the customer's linked accounts
- Paying third parties, including bill payments (see, e.g., BPAY) and third party fund transfers (see, e.g., FAST)
- Investment purchase or sale
- Loan applications and transactions, such as repayments of enrollments
- Credit card applications
- Register utility billers and make bill payments
- Financial institution administration
- Management of multiple users having varying levels of authority
- Transaction approval process
- Personal financial management support, such as importing data into personal accounting software. Some online banking platforms support account aggregation to allow the customers to monitor all of their accounts in one place whether they are with their main bank or with other institutions.
Advantages
There are some advantages on using e-banking both for banks and customers:- Permanent access to the bank
- Lower transaction costs / general cost reductions
- Access anywhere using mobile or computer
- Less time consuming
- Very safe and secure method
- Helps to transfer the money immediately and accurately
- Easy to use
Saving to electronic media :

Five security token devices for online banking.
The use of a secure website has been almost universally embraced.
Though single password authentication is still in use, it by itself is not considered secure enough for online banking in some countries. Basically there are two different security methods in use for online banking:
- The PIN/TAN system where the PIN represents a password, used for the login and TANs representing one-time passwords to authenticate transactions. TANs can be distributed in different ways, the most popular one is to send a list of TANs to the online banking user by postal letter. Another way of using TANs is to generate them by need using a security token. These token generated TANs depend on the time and a unique secret, stored in the security token (two-factor authentication or 2FA).
- More advanced TAN generators (chipTAN) also include the transaction data into the TAN generation process after displaying it on their own screen to allow the user to discover man-in-the-middle attacks carried out by Trojans trying to secretly manipulate the transaction data in the background of the PC.
- Another way to provide TANs to an online banking user is to send the TAN of the current bank transaction to the user's (GSM) mobile phone via SMS. The SMS text usually quotes the transaction amount and details, the TAN is only valid for a short period of time. Especially in Germany, Austria and the Netherlands many banks have adopted this "SMS TAN" service.
- Usually online banking with PIN/TAN is done via a web browser using SSL secured connections, so that there is no additional encryption needed.
- Signature based online banking where all transactions are signed and encrypted digitally. The Keys for the signature generation and encryption can be stored on smartcards or any memory medium, depending on the concrete implementation (see, e.g., the Spanish ID card DNI electrónico ).
Attacks
Attacks on online banking used today are based on deceiving the user to steal login data and valid TANs. Two well known examples for those attacks are phishing and pharming. Cross-site scripting and keylogger/Trojan horses can also be used to steal login information.A method to attack signature based online banking methods is to manipulate the used software in a way, that correct transactions are shown on the screen and faked transactions are signed in the background.
A 2008 U.S. Federal Deposit Insurance Corporation Technology Incident Report, compiled from suspicious activity reports banks file quarterly, lists 536 cases of computer intrusion, with an average loss per incident of $30,000. That adds up to a nearly $16-million loss in the second quarter of 2007. Computer intrusions increased by 150 percent between the first quarter of 2007 and the second. In 80 percent of the cases, the source of the intrusion is unknown but it occurred during online banking, the report states.[11]
Another kind of attack is the so-called man-in-the-browser attack, a variation of the man-in-the-middle attack where a Trojan horse permits a remote attacker to secretly modify the destination account number and also the amount in the web browser.
As a reaction to advanced security processes allowing the user to cross-check the transaction data on a secure device there are also combined attacks using malware and social engineering to persuade the user himself to transfer money to the fraudsters on the ground of false claims (like the claim the bank would require a "test transfer" or the claim a company had falsely transferred money to the user's account and he should "send it back"). Users should therefore never perform bank transfers they have not initiated themselves.
Countermeasures
There exist several countermeasures which try to avoid attacks. Digital certificates are used against phishing and pharming, in signature based online banking variants (HBCI/FinTS) the use of "Secoder" card readers is a measurement to uncover software side manipulations of the transaction data.To protect their systems against Trojan horses, users should use virus scanners and be careful with downloaded software or e-mail attachments.In 2001, the U.S. Federal Financial Institutions Examination Council issued guidance for multifactor authentication (MFA) and then required to be in place by the end of 2006.
In 2012, the European Union Agency for Network and Information Security advised all banks to consider the PC systems of their users being infected by malware by default and therefore use security processes where the user can cross-check the transaction data against manipulations like for example (provided the security of the mobile phone holds up) SMS TAN where the transaction data is sent along with the TAN number or standalone smartcard readers with an own screen including the transaction data into the TAN generation process while displaying it beforehand to the user (see chipTAN) to counter man-in-the-middle attacks .
XXX . V Electronic funds transfer
Electronic Funds Transfer (EFT) is the electronic transfer of money from one bank account to another, either within a single financial institution or across multiple institutions, via computer-based systems, without the direct intervention of bank staff. EFT transactions are known by a number of names. In the United States, they may be referred to as electronic checks or e-checks.
The term covers a number of different payment systems, for example:
- cardholder-initiated transactions, using a payment card such as a credit or debit card
- direct deposit payment initiated by the payer
- direct debit payments for which a business debits the consumer's bank accounts for payment for goods or services
- wire transfer via an international banking network such as SWIFT
- electronic bill payment in online banking, which may be delivered by EFT or paper check
- transactions involving stored value of electronic money, possibly in a private currency.
Steps
An EFT transaction requires the following steps:- Making application
- Data preparation
- Data transmission
- Debiting remittance banks
- Crediting receiving banks
- Crediting beneficiary
- Task at service branch
- Task at beneficiary branch
Interbank network
An interbank network, also known as an ATM consortium or ATM network, is a computer network that enables ATM cards issued by a financial institution that is a member of the network to be used to perform ATM transactions through ATMs that belong to another member of the network.
However, the functions which may be performed at the network ATM vary. For example, special services, such as the purchase of mobile phone airtime, may be available to own-bank but not to network ATM cardholders. Furthermore, the network ATM owner may charge a fee for use of network cards (in addition to any fees imposed by the own-bank).
Interbank networks enable ATM cardholders to have access to ATMs of other banks that are members of the network when their own bank's ATM is unavailable. This is especially convenient for travelers traveling abroad, where multinational interbank networks, like Plus or Cirrus, are widely available.
Interbank networks also permit, through different means, the use of ATM cards at a point of sale through the use of a special EFTPOS terminal where ATM cards are treated as debit cards .
Around the world
Major economies
| Major economy | Interbank network name | Real-time gross settlement payment system |
|---|---|---|
| Australia | Electronic Funds Transfer at Point Of Sale (EFTPOS) | Reserve Bank Information & Transfer System (RITS) |
| Canada | Interac | Large Value Transfer System (LVTS) |
| China | China Union Pay | China National Advanced Payment System (CNAPS) |
| France | Groupement des Cartes Bancaires CB | EBA Clearing (Euro1), Trans-European Automated Real-time Gross Settlement Express Transfer System (TARGET2) |
| Germany | Girocard | EBA Clearing (Euro1), Trans-European Automated Real-time Gross Settlement Express Transfer System (TARGET2) |
| Italy | Bancomat | EBA Clearing (Euro1), Trans-European Automated Real-time Gross Settlement Express Transfer System (TARGET2) |
| India | National Financial Switch (NFS), Banks ATM Network and Customer Services (BANCS), Cashnet | Reserve Bank of India Real Time Gross Settlement (RBI-RTGS) |
| Nigeria | Interswitch | National Interbank Settlement Scheme (NIBSS) |
| Japan | Yucho | Bank of Japan Financial Network System (BOJ-NET) |
| United Kingdom | LINK | Clearing House Automated Payment System (CHAPS) |
| United States | New York Currency Exchange (NYCE), Pulse, STAR | Clearing House Interbank Payments System (CHIPS), Fedwire |
| Card brand | Total assets (US$ billion) |
|---|---|
| American Express | 153 |
| Discover Financial Services | 69 |
| Visa International | 40 |
| MasterCard Worldwide | 14 |
| Japan Credit Bureau | 11 |
Brazil
In Brazil, the major interbank network is the Banco 24 Horas network.Caribbean
In the Caribbean, the major interbank network is the ATH network. Most banks issue dual ATH and MasterCard/Visa cards, using the ATH network for ATM transactions and MasterCard/Visa for EFTPOS transactions. Some banks (such as BanReservas) issue ATH-only cards which use the ATH network for both ATM and EFTPOS transactions.Germany Girocard
In Germany Girocard interbank network provides debit card service connecting virtually all German ATMs and banks.Japan
In Japan, many Electronic funds transfer interbank networks exist.- Major network is BANCS (urban bank) and YUCHO (Japan Post Bank)
- Minor network is ACS (local bank), SOCS (trust bank), LONGS (long term bank), SCS (secondary local bank), SINKIN-NETCASH (Shinkin bank), SANCS (credit union), ROCS (Labour Bank), JABANK-NET (Norinchukin Bank,).
Philippines
BancNet (also spelled Bancnet) is a Philippine-based interbank network connecting the ATM networks of local and offshore banks, and the largest interbank network in the Philippines in terms of the number of member banks and annual transactions.BancNet is also the exclusive gateway of China's UnionPay, allowing access to the nearly 1 billion ATM cardholders from the People's Republic of China. BancNet is allied with global payment brand JCB International. Through this alliance, JCB cardholders can now do cash advances at participating BancNet member ATMs nationwide. Bancnet interconnects with international card networks Diners Club, Discover Card, KFTC, MasterCard, and VISA
BancNet serves more than 41 million ATM cardholders of its 114 members and affiliates with over 12,000 ATMs and more than 5,000 POS terminals.
In 2008, ExpresNet outsourced its ATM operations to BancNet. On January 30, 2015, BancNet and MegaLink announced their merger and will retain itself as its brand.
Portugal
Multibanco is the single unified interbank network in Portugal, that links the ATMs of all Portuguese banks. This network has existed since 1985 and is owned by SIBS (Sociedade Interbancária de Serviços). Multibanco is a fully integrated interbank network and offers many more services than those usually found in other countries' networks.Multibanco also has a full-fledged EFTPOS network, the Multibanco Automatic Payment, and is also a provider of mobile phone and Internet banking services through the TeleMultibanco and MBNet services, respectively. It is also the provider of the Via Verde electronic toll collection service.
United States
Due to the historically fragmented nature of banking in the United States, there have been a large number of small banks, which resulted in a number of different interbank networks being established, mostly along geographic lines. These started to consolidate from the mid 1980s, resulting in three major interbank networks which, by 2003, had over 70% of the volume in the United States:[2]Society for Worldwide Interbank Financial Telecommunication
The Society for Worldwide Interbank Financial Telecommunication (SWIFT) provides a network that enables financial institutions worldwide to send and receive information about financial transactions in a secure, standardized and reliable environment. SWIFT also sells software and services to financial institutions, much of it for use on the SWIFTNet Network, and ISO 9362. Business Identifier Codes (BICs, previously Bank Identifier Codes) are popularly known as "SWIFT codes".
The majority of international interbank messages use the SWIFT network. As of 2015[update], SWIFT linked more than 11,000 financial institutions in more than 200 countries and territories, who were exchanging an average of over 15 million messages per day (compared to an average of 2.4 million daily messages in 1995).[1] SWIFT transports financial messages in a highly secure way but does not hold accounts for its members and does not perform any form of clearing or settlement.
SWIFT does not facilitate funds transfer: rather, it sends payment orders, which must be settled by correspondent accounts that the institutions have with each other. Each financial institution, to exchange banking transactions, must have a banking relationship by either being a bank or affiliating itself with one (or more) so as to enjoy those particular business features.
SWIFT is a cooperative society under Belgian law owned by its member financial institutions with offices around the world. SWIFT headquarters, designed by Ricardo Bofill Taller de Arquitectura are in La Hulpe, Belgium, near Brussels. The chairman of SWIFT is Yawar Shah,[2] originally from Pakistan,[3] and its CEO is Gottfried Leibbrandt, originally from the Netherlands.[4] SWIFT hosts an annual conference every year, called Sibos, specifically aimed at the financial services industry.
SWIFT was founded in Brussels in 1973 under the leadership of its inaugural CEO Carl Reuterskiöld (1973–1983) and was supported by 239 banks in fifteen countries. It started to establish common standards for financial transactions and a shared data processing system and worldwide communications network designed by Logica.[5] Fundamental operating procedures, rules for liability, etc., were established in 1975 and the first message was sent in 1977. SWIFT's first United States operating center was inaugurated by Governor John N. Dalton of Virginia in 1979.[6]
Standards
SWIFT has become the industry standard for syntax in financial messages. Messages formatted to SWIFT standards can be read by, and processed by, many well-known financial processing systems, whether or not the message traveled over the SWIFT network. SWIFT cooperates with international organizations for defining standards for message format and content. SWIFT is also Registration authority (RA) for the following ISO standards: [7]- ISO 9362: 1994 Banking—Banking telecommunication messages—Bank identifier codes
- ISO 10383: 2003 Securities and related financial instruments—Codes for exchanges and market identification (MIC)
- ISO 13616: 2003 IBAN Registry
- ISO 15022: 1999 Securities—Scheme for messages (Data Field Dictionary) (replaces ISO 7775)
- ISO 20022-1: 2004 and ISO 20022-2:2007 Financial services—Universal Financial Industry message scheme
Operations centers
The SWIFT secure messaging network is run from two redundant data centers, one in the United States and one in the Netherlands. These centers share information in near real-time. In case of a failure in one of the data centers, the other is able to handle the traffic of the complete network.SWIFT opened a third data center in Switzerland, which started operating in 2009. Since then, data from European SWIFT members are no longer mirrored to the U.S. data center. The distributed architecture partitions messaging into two messaging zones: European and Trans-Atlantic.European zone messages are stored in the Netherlands and in a part of the Switzerland operating center; Trans-Atlantic zone messages are stored in the United States and in a part of the Switzerland operating center that is segregated from the European zone messages. Countries outside of Europe were by default allocated to the Trans-Atlantic zone but could choose to have their messages stored in the European zone.
SWIFTNet network
SWIFT moved to its current IP network infrastructure, known as SWIFTNet, from 2001 to 2005,providing a total replacement of the previous X.25 infrastructure. The process involved the development of new protocols that facilitate efficient messaging, using existing and new message standards. The adopted technology chosen to develop the protocols was XML, where it now provides a wrapper around all messages legacy or contemporary. The communication protocols can be broken down into:InterAct
| FileAct
| Browse
|
Architecture
SWIFT provides a centralized store-and-forward mechanism, with some transaction management. For bank A to send a message to bank B with a copy or authorization with institution C, it formats the message according to standard and securely sends it to SWIFT. SWIFT guarantees its secure and reliable delivery to B after the appropriate action by C. SWIFT guarantees are based primarily on high redundancy of hardware, software, and people.SWIFTNet Phase 2
During 2007 and 2008, the entire SWIFT Network migrated its infrastructure to a new protocol called SWIFTNet Phase 2. The main difference between Phase 2 and the former arrangement is that Phase 2 requires banks connecting to the network to use a Relationship Management Application (RMA) instead of the former bilateral key exchange (BKE) system. According to SWIFT's public information database on the subject, RMA software should eventually prove more secure and easier to keep up-to-date; however, converting to the RMA system meant that thousands of banks around the world had to update their international payments systems to comply with the new standards. RMA completely replaced BKE on 1 January 2009.Products and interfaces
SWIFT means several things in the financial world:- a secure network for transmitting messages between financial institutions;
- a set of syntax standards for financial messages (for transmission over SWIFTNet or any other network)
- a set of connection software and services allowing financial institutions to transmit messages over SWIFT network.
- SWIFTNet Link (SNL) software which is installed on the SWIFT customer's site and opens a connection to SWIFTNet. Other applications can only communicate with SWIFTNet through the SNL.
- Alliance Gateway (SAG) software with interfaces (e.g., RAHA = Remote Access Host Adapter), allowing other software products to use the SNL to connect to SWIFTNet
- Alliance WebStation (SAB) desktop interface for SWIFT Alliance Gateway with several usage options:
- administrative access to the SAG
- direct connection SWIFTNet by the SAG, to administrate SWIFT Certificates
- so-called Browse connection to SWIFTNet (also by SAG) to use additional services, for example Target2
- Alliance Access (SAA) and Alliance Messaging Hub (AMH) are the main messaging software applications by SWIFT, which allow message creation for FIN messages, routing and monitoring for FIN and MX messages. The main interfaces are FTA (files transfer automated, not FTP) and MQSA, a WebSphere MQ interface.
- The Alliance Workstation (SAW) is the desktop software for administration, monitoring and FIN message creation. Since Alliance Access is not yet capable of creating MX messages, Alliance Messenger (SAM) has to be used for this purpose.
- Alliance Web Platform (SWP) as new thin-client desktop interface provided as an alternative to existing Alliance WebStation, Alliance Workstation (soon) and Alliance Messenger.
- Alliance Integrator built on Oracle's Java Caps which enables customer's back office applications to connect to Alliance Access or Alliance Entry.
- Alliance Lite2 is a secure and reliable, cloud-based way to connect to the SWIFT network which is a Lite version of Alliance Access specifically targeting customers with low volume of traffic.
Securities
| Treasury & Derivatives
| Cash Management
| Trade Services
|
SWIFTREFSwift Ref, the global payment reference data utility, is SWIFT’s unique reference data service. Swift Ref sources data direct from data originators, including central banks, code issuers and banks making it easy for issuers and originators to maintain data regularly and thoroughly. SWIFTRef constantly validates and cross-checks data across the different data sets.
SWIFTNet Mail SWIFT offers a secure person-to-person messaging service, SWIFTNet Mail, which went live on 16 May 2007. SWIFT clients can configure their existing email infrastructure to pass email messages through the highly secure and reliable SWIFTNet network instead of the open Internet. SWIFTNet Mail is intended for the secure transfer of sensitive business documents, such as invoices, contracts and signatories, and is designed to replace existing telex and courier services, as well as the transmission of security-sensitive data over the open Internet. Seven financial institutions, including HSBC, FirstRand Bank, Clearstream, DnB NOR, Nedbank, and Standard Bank of South Africa, as well as SWIFT piloted the service.
U.S. government involvement
Terrorist Finance Tracking Program
A series of articles published on 23 June 2006 in The New York Times, The Wall Street Journal, and the Los Angeles Times revealed a program, named the Terrorist Finance Tracking Program, which the US Treasury Department, Central Intelligence Agency (CIA), and other United States governmental agencies initiated after the 11 September attacks to gain access to the SWIFT transaction database.[16]After the publication of these articles, SWIFT quickly came under pressure for compromising the data privacy of its customers by allowing governments to gain access to sensitive personal information. In September 2006, the Belgian government declared that these SWIFT dealings with American governmental authorities were a breach of Belgian and European privacy laws.
In response, and to satisfy members' concerns about privacy, SWIFT began a process of improving its architecture by implementing a distributed architecture with a two-zone model for storing messages
Concurrently, the European Union negotiated an agreement with the United States Government to permit the transfer of intra-EU SWIFT transaction information to the United States under certain circumstances. Because of concerns about its potential contents, the European Parliament adopted a position statement in September 2009, demanding to see the full text of the agreement and asking that it be fully compliant with EU privacy legislation, with oversight mechanisms emplaced to ensure that all data requests were handled appropriately. An interim agreement was signed without European Parliamentary approval by the European Council on 30 November 2009, the day before the Lisbon Treaty—which would have prohibited such an agreement from being signed under the terms of the Codecision procedure—formally came into effect. While the interim agreement was scheduled to come into effect on 1 January 2010, the text of the agreement was classified as "EU Restricted" until translations could be provided in all EU languages and published on 25 January 2010.
On 11 February 2010, the European Parliament decided to reject the interim agreement between the EU and the USA with 378 to 196 votes. One week earlier, the parliament's civil liberties committee already rejected the deal, citing legal reservations.
In March 2011, it was reported that two mechanisms of data protection had failed: EUROPOL released a report complaining that the USA's requests for information had been too vague (making it impossible to make judgments on validity) and that the guaranteed right for European citizens to know whether their information had been accessed by USA authorities had not been put into practice.
Sanctions against Iran
In January 2012, the advocacy group United Against Nuclear Iran (UANI) implemented a campaign calling on SWIFT to end all relations with Iran's banking system, including the Central Bank of Iran. UANI asserted that Iran's membership in SWIFT violated U.S. and EU financial sanctions against Iran as well as SWIFT's own corporate rules.[23]Consequently, in February 2012, the U.S. Senate Banking Committee unanimously approved sanctions against SWIFT aimed at pressuring the Belgian financial telecommunications network to terminate its ties with blacklisted Iranian banks. Expelling Iranian banks from SWIFT would potentially deny Iran access to billions of dollars in revenue and spending using SWIFT but not from using IVTS. Mark Wallace, president of UANI, praised the Senate Banking Committee.[24]
Initially SWIFT denied it was acting illegally,[24] but now says "it is working with U.S. and European governments to address their concerns that its financial services are being used by Iran to avoid sanctions and conduct illicit business."[25] Targeted banks would be — amongst others — Saderat Bank of Iran, Bank Mellat, Post Bank of Iran and Sepah Bank.[26] On 17 March 2012, following agreement two days earlier between all 27 member states of the Council of the European Union and the Council's subsequent ruling, SWIFT disconnected all Iranian banks from its international network that had been identified as institutions in breach of current EU sanctions and warned that even more Iranian financial institutions could be disconnected from the network.
In February 2016, Iranian banks reconnected to the network following lift of sanctions on Joint Comprehensive Plan of Action.
U.S. control over transactions within the EU
On 26 February 2012 the Danish newspaper Berlingske reported that US authorities have sufficient control over SWIFT to seize money being transferred between two European Union (EU) countries (Denmark and Germany), since they succeeded in seizing around US$26,000 that was being transferred from a Danish businessman to a German bank. The transaction was automatically routed through the US, possibly because of the USD currency used in the transaction which is how the United States was able to seize the funds. The money was a payment for a batch of Cuban cigars previously imported to Germany by a German supplier. As justification for the seizure, the U.S. Treasury stated that the Danish businessman had violated the United States embargo against Cuba.Monitoring by the NSA
Der Spiegel reported in September 2013 that the National Security Agency (NSA) widely monitors banking transactions via SWIFT, as well as credit card transactions.[30] The NSA intercepted and retained data from the SWIFT network used by thousands of banks to securely send transaction information. SWIFT was named as a "target", according to documents leaked by Edward Snowden. The documents revealed that the NSA spied on SWIFT using a variety of methods, including reading "SWIFT printer traffic from numerous banks."[30] In April 2017, a group known as the Shadow Brokers released files allegedly from the NSA which indicate that the agency monitored financial transactions made through SWIFT.Use in sanctions
As mentioned above SWIFT has disconnected all Iranian banks from its international network as a sanction against Iran. Similarly, in August 2014 the UK planned to press the EU to block Russian use of SWIFT as a sanction due to Russian military intervention in Ukraine. However, SWIFT refused to do so. In their official statement they said, "SWIFT regrets the pressure, as well as the surrounding media speculation, both of which risk undermining the systemic character of the services that SWIFT provides its customers around the world". SWIFT also rejected calls to boycott Israeli banks from its network.Value transfer system
A value transfer system refers to any system, mechanism, or network of people that receives money for the purpose of making the funds or an equivalent value payable to a third party in another geographic location, whether or not in the same form.
The average size of the payment is an indicator of the system's use. Specialised large-value transfer system have developed because of the large size and critical timing of some payments market participants require services and mechanisms that meet their need for reliability, security, accuracy and timeliness.
A value transfer system may fall into one or more of these groups:
- Retail value transfer systems:
- Traditional retail value transfer systems, e.g. Bank transfer, Wire transfer, Post offices transfer service or specialist companies such as Western Union
- Internet-only value transfer systems, e.g. Electronic money such as PayPal, eGold, Liberty Reserve
- Cryptocurrencies: Bitcoin, Litecoin, Ethereum, etc.
- Institutional formal value transfer systems, e.g. SWIFT (International), domestic real-time gross settlement (RTGS) systems such as LVTS (Canada), Fedwire (USA), CHAPS (UK)
- Informal value transfer systems,
XXX . V000 Payment system
A payment system is any system used to settle financial transactions through the transfer of monetary value, and includes the institutions, instruments, people, rules, procedures, standards, and technologies that make such an exchange possible.A common type of payment system is the operational network that links bank accounts and provides for monetary exchange using bank deposits.
What makes a payment system a system is the use of cash-substitutes; traditional payment systems are negotiable instruments such as drafts (e.g., checks) and documentary credits such as letters of credit. With the advent of computers and electronic communications a large number of alternative electronic payment systems have emerged. These include debit cards, credit cards, electronic funds transfers, direct credits, direct debits, internet banking, and e-commerce payment systems. Some payment systems include credit mechanisms, but that is essentially a different aspect of payment. Payment systems are used in lieu of tendering cash in domestic and international transactions and consist of a major service provided by banks and other financial institutions.
Payment systems may be physical or electronic and each has its own procedures and protocols. Standardization has allowed some of these systems and networks to grow to a global scale, but there are still many country- and product-specific systems. Examples of payment systems that have become globally available are credit card and automated teller machine networks. Specific forms of payment systems are also used to settle financial transactions for products in the equity markets, bond markets, currency markets, futures markets, derivatives markets, options markets, and to transfer funds between financial institutions both domestically using clearing and real-time gross settlement (RTGS) systems and internationally using the SWIFT network.
The term electronic payment refers to a payment made from one bank account to another using electronic methods and forgoing the direct intervention of bank employees. Narrowly defined electronic payment refers to e-commerce—a payment for buying and selling goods or services offered through the Internet, or broadly to any type of electronic funds transfer.
National
An efficient national payment system reduces the cost of exchanging goods, services, and assets and is indispensable to the functioning of the interbank, money, and capital markets. A weak payment system may severely drag on the stability and developmental capacity of a national economy; its failures can result in inefficient use of financial resources, inequitable risk-sharing among agents, actual losses for participants, and loss of confidence in the financial system and in the very use of money The technical efficiency of payment system is important for a development of economy. Real-time gross settlement systems (RTGS) are funds transfer systems where transfer of money or securities takes place from one bank to another on a "real-time" and on "gross" basis. Settlement in "real time" means that payment transaction does not require any waiting period. The transactions are settled as soon as they are processed. "Gross settlement" means the transaction is settled on one to one basis without bunching or netting with any other transaction. Once processed, payments are final and irrevocable.TARGET2 is a RTGS system that covers the European Union member states that use the euro, and is part of the Eurosystem, which comprises the European Central Bank and the national central banks of those countries that have adopted the euro. TARGET2 is used for the settlement of central bank operations, large-value Euro interbank transfers as well as other euro payments. TARGET 2 provides real-time financial transfers, debt settlement at central banks which is immediate and irreversible.
International
Globalization is driving corporations to transact more frequently across borders. Consumers are also transacting more on a global basis—buying from foreign eCommerce sites; traveling, living, and working abroad. For the payments industry, the result is higher volumes of payments—in terms of both currency value and number of transactions. This is also leading to a consequent shift downwards in the average value of these payments.The ways these payments are made can be cumbersome, error prone, and expensive. Growth, after all, is often messy. Payments systems set up decades ago continue to be used sometimes retrofitted, sometimes force-fitted—to meet the needs of modern corporations. And, not infrequently, the systems creak and groan as they bear the strain.
For users of these systems, on both the paying and receiving sides, it can be difficult and time-consuming to learn how to use cross-border payments tools, and how to set up processes to make optimal use of them. Solution providers (both banks and non-banks) also face challenges, struggling to cobble together old systems to meet new demands. But for these providers, cross-border payments are both lucrative (especially given foreign exchange conversion revenue) and rewarding, in terms of the overall financial relationship created with the end customer.
The challenges for global payments are not simply those resulting from volume increases. A number of economic, political, and technical forces are changing the types of cross-border transactions conducted. Consider these factors:
- Corporations are making more cross-border purchases of services (as opposed to goods), as well as more purchases of complex fabricated parts rather than simple raw materials.
- Enterprises are purchasing from more countries, in more regions.
- Increased outsourcing is leading to new in-country and new cross-border intracompany transactions.
- More enterprises are participating in complex, automated supply chains, which in some cases drive automatic ordering and fulfillment. Online purchasing continues to grow, both by large enterprises as part of an automated procurement systems and by smaller enterprises purchasing directly.
- There is continued growth in the use of cross-border labor.
- Individuals are increasingly taking their investments abroad.
Payment card
A payment card is part of a payment system that enables its owner (the cardholder) to make a payment by electronic funds transfer.[1] There are a number of types of payment cards, the most common ones being credit cards and debit cards. Payment cards are usually embossed plastic cards, 85.60 × 53.98 mm in size, which comply with the ISO/IEC 7810 ID-1 standard. They usually also have an embossed card number conforming with the ISO/IEC 7812 numbering standard, the cardholder’s name and the card expiry date, in addition to other security features.
Most commonly, a payment card is electronically linked to an account or accounts belonging to the cardholder. These accounts may be deposit accounts or loan or credit accounts, and the card is a means of authenticating the cardholder. However, stored-value cards store money on the card itself and are not necessarily linked to an account at a financial institution.

Example of two credit cards
Payment cards have features in common, as well as distinguish features. Types of payment cards can be distinguished on the basis of the features of each type of card, including:
Credit card
A credit card is linked to a line of credit (usually called a credit limit) created by the issuer of the credit card for the cardholder on which the cardholder can draw (i.e. borrow), either for payment to a merchant for a purchase or as a cash advance to the cardholder. Most credit cards are issued by or through local banks or credit unions, but some non-bank financial institutions also offer cards directly to the public.
The cardholder can choose either to repay the full outstanding balance by the payment due date or to repay a smaller amount, not less than the "minimum amount", by that date. In the former case, interest is typically not charged; while in the latter case, the cardholder will be charged with interest. The rate of interest and method of calculating the charge vary between credit cards, even for different types of card issued by the same company. Many credit cards can also be used to take cash advances through ATMs, which also attract interest charges, usually calculated from the date of cash withdrawal. Some merchants charge a fee for purchases by credit card, as they will be charged a fee by the card issuer.
Debit card
With a debit card (also known as a bank card, check card or some other description) when a cardholder makes a purchase, funds are withdrawn directly either from the cardholder's bank account, or from the remaining balance on the card, instead of the holder repaying the money at a later date. In some cases, the "cards" are designed exclusively for use on the Internet, and so there is no physical card.
The use of debit cards has become widespread in many countries and has overtaken use of cheques, and in some instances cash transactions, by volume. Like credit cards, debit cards are used widely for telephone and internet purchases.
Debit cards can also allow instant withdrawal of cash, acting as the ATM card, and as a cheque guarantee card. Merchants can also offer "cashback"/"cashout" facilities to customers, where a customer can withdraw cash along with their purchase. Merchants usually do not charge a fee for purchases by debit card.
Charge card
With charge cards, the cardholder is required to pay the full balance shown on the statement, which is usually issued monthly, by the payment due date. It is a form of short-term loan to cover the cardholder's purchases, from the date of the purchase and the payment due date, which may typically be up to 55 days. Interest is usually not charged on charge cards and there is usually no limit on the total amount that may be charged.[citation needed] If payment is not made in full, this may result in a late payment fee, the possible restriction of future transactions, and perhaps the cancellation of the card.
ATM card
An ATM card (known under a number of names) is any card that can be used in automated teller machines (ATMs) for transactions such as deposits, cash withdrawals, obtaining account information, and other types of transactions, often through interbank networks. Cards may be issued solely to access ATMs, and most debit or credit cards may also be used at ATMs, but charge and proprietary cards cannot.
The use of a credit card to withdraw cash at an ATM is treated differently to an POS transaction, usually attracting interest charges from the date of the cash withdrawal. The use of a debit card usually does not attract interest. Third party ATM owners may charge a fee for the use of the ATM.
Stored-value card
With a stored-value card, a monetary value is stored on the card, and not in an externally recorded account. This differs from prepaid cards where money is on deposit with the issuer similar to a debit card. One major difference between stored value cards and prepaid debit cards is that prepaid debit cards are usually issued in the name of individual account holders, while stored-value cards are usually anonymous.
The term stored-value card means that the funds and or data are physically stored on the card. With prepaid cards the data is maintained on computers controlled by the card issuer. The value stored on the card can be accessed using a magnetic stripe embedded in the card, on which the card number is encoded; using radio-frequency identification (RFID); or by entering a code number, printed on the card, into a telephone or other numeric keypad.
Fleet card
A fleet card is used as a payment card, most commonly for gasoline, diesel and other fuels at gas stations. Fleet cards can also be used to pay for vehicle maintenance and expenses, at the discretion of the fleet owner or manager. The use of a fleet card reduces the need to carry cash, thus increasing the security for fleet drivers. The elimination of cash also helps to prevent fraudulent transactions at the fleet owner's or manager's expense.
Fleet cards provide convenient and comprehensive reporting, enabling fleet owners/managers to receive real time reports and set purchase controls with their cards, helping to keep them informed of all business related expenses.
Other
Other types of payment cards include:
- Gift card
- Electronic money
- Store card
Technologies
A number of International Organization for Standardization standards, ISO/IEC 7810, ISO/IEC 7811, ISO/IEC 7812, ISO/IEC 7813, ISO 8583, and ISO/IEC 4909, define the physical properties of payment cards, including size, flexibility, location of the magstripe, magnetic characteristics, and data formats. They also provide the standards for financial cards, including the allocation of card number ranges to different card issuing institutions.Embossing
Originally charge account identification was paper-based. In 1959 American Express was the first charge card operator to issue embossed plastic cards which enabled cards to be manually imprinted for processing, making processing faster and reducing transcription errors. Other credit card issuers followed suit. The information typically embossed are the bank card number, card expiry date and cardholder's name. Though the imprinting method has been predominantly superseded by the magnetic stripe and then by the integrated chip, cards continue to be embossed in case a transaction needs to be processed manually. Cards conform to the ISO/IEC 7810 ID-1 standard, ISO/IEC 7811 on embossing, and the ISO/IEC 7812 card numbering standard.Magnetic stripe

An example of the reverse side of a typical debit card:
Smart card
A smart card, chip card, or integrated circuit card (ICC), is any pocket-sized card with embedded integrated circuits which can process data. This implies that it can receive input which is processed — by way of the ICC applications — and delivered as an output. There are two broad categories of ICCs. Memory cards contain only non-volatile memory storage components, and perhaps some specific security logic. Microprocessor cards contain volatile memory and microprocessor components. The card is made of plastic, generally PVC, but sometimes ABS. The card may embed a hologram to avoid counterfeiting. Using smart cards is also a form of strong security authentication for single sign-on within large companies and organizations.EMV is the standard adopted by all major issuers of smart payment cards.[citation needed]
Proximity card
Proximity card (or prox card) is a generic name for contactless integrated circuit devices used for security access or payment systems. It can refer to the older 125 kHz devices or the newer 13.56 MHz contactless RFID cards, most commonly known as contactless smartcards.Modern proximity cards are covered by the ISO/IEC 14443 (proximity card) standard. There is also a related ISO/IEC 15693 (vicinity card) standard. Proximity cards are powered by resonant energy transfer and have a range of 0-3 inches in most instances. The user will usually be able to leave the card inside a wallet or purse. The price of the cards is also low, usually US$2–$5, allowing them to be used in applications such as identification cards, keycards, payment cards and public transit fare cards.
Re-programmable magnetic stripe card
Re-programmable/dynamic magnetic stripe cards are standard sized transaction cards that include a battery, a processor, and a means (inductive coupling or otherwise)of sending a variable signal to a magnetic stripe reader. Re-programmable stripe cards are often more secure than standard magnetic stripe cards and can transmit information for multiple cardholder accounts.[Payment terminal
A payment terminal, also known as a point of sale terminal, credit card terminal, EFTPOS terminal (or a PDQ terminal in East Africa - which stands for "Process Data Quickly"), is a device which interfaces with payment cards to make electronic funds transfers.
There are various types of terminals available to merchants, although most have the same basic purpose and functions. They allow a merchant to insert, swipe, or manually enter the required credit/debit card information, as well as to accept NFC Contactless transactions, and to transmit this data to the merchant service provider for authorization and finally, to transfer funds to the merchant.
Higher end models not only process credit and debit cards but also serve as a comprehensive customer engagement screen at the checkout. Common features include but are not limited to the ability to process gift cards, cheques, contactless and mobile wallet payments. Some are also programed to accept store loyalty cards or allow the customer to use the pin pad to enter their information (ex. phone number) to redeem points. POS screens also allow retailors to advertise near the register when the terminal isn't being used.[2] During the checkout process, many terminals are set to display a list of items purchased along with the running total. Other times, this functionality may be turned off or it may be used to supplement a dedicated screen that lists items being purchased. Some stores also use the terminal for customers to view and agree to the terms of a product warranty. Like ATMs, many POS terminals are also equipped raised tactile buttons and an earphone jack which allow the blind to audibly finish the payment process. [3][4]
The majority of card terminals transmit data over a standard telephone line or a internet connection. Some also have the ability to cache transactional data to be transmitted to the gateway processor when a connection becomes available; the major drawback to this is that immediate authorization is not available at the time the card was processed, which can subsequently result in failed payments. Wireless terminals transmit card data using Bluetooth, Wi-Fi, cellular, [5] or even satellite networks in remote areas and onboard airplanes.
A merchant can replace the functionality of dedicated credit card terminal hardware using a terminal application running on a PC or mobile device, such as a smartphone. They usually work with dedicated hardware readers that can transfer magnetic stripe data to the application, while there are also some that also work with smart cards (using technology such as EMV), although this is rarely seen on smartphone readers. In case the necessary hardware is unavailable, these applications usually support manual entry of the card number and other data. In addition, more and more devices are beginning to offer built-in RFID or NFC technology to accommodate contactless or mobile device payment methods, often without requiring additional external hardware.
By moving to the use of card terminals to directly capture card information instead of manually entering in card details, merchants benefit from the efficiency of decreased transaction processing times. In terms of security, major card terminal manufacturers usually offer software allowing end to end card data encryption. Still, there have been some cases of POS pin pad malware. In countries such as the US, where magnetic stripe cards aren't fully phased out, there have also been incidence of skimming at card terminals.That said, stand alone payment terminals are seen as superior to register attached payment methods because they don't require store cashers to take possession of the customer's card.
back to basics :
Prior to the development of payment terminals, merchants would use Manual Imprinters (also known as ZipZap machines) to capture the information from the embossed information on a credit card onto a paper slips with carbon paper copies.[9] These paper slips had to be taken to the bank for processing. This was a cumbersome and time consuming process.
Point of sale terminals emerged in 1979, when Visa introduced a bulky electronic data capturing terminal which was the first payment terminal. In the same year magnetic stripes were added to credit cards for the first time.[10] This allowed card information to be captured electronically and led to the development of payment terminals.
One of the first companies to produce dedicated payment terminals was Verifone. It started in 1981 in Hawaii as a small electronic company. In 1983 they introduced the ZON terminal series which would become the standard for modern payment terminals.
Hungarian born George Wallner in Sydney, Australia founded rival Hypercom in 1978 and in 1982 started producing dedicated payment terminals. It went on to dominate the south pacific region. In 1988 the company signed a deal with American Express to provide its terminals to them in the US. To consolidate the deal, Hypercom moved its head office from Australia to Arizona in the US. It then faced head to head competition with VeriFone on its home market.[11]
Over a decade later in 1994 Lipman Electronic Engineering, Ltd. was established in Israel. Lipman manufactured the Nurit line of processing terminals. Because of Verifone’s already firm place in the payment processing industry when Lipman was established, Lipman targeted an untapped niche in the processing industry. While, Lipman holds about a 10% share in wired credit card terminals, they are the undisputed leader with more than 95% share in wireless processing terminals in the late 1990s.
Verifone would later acquired both of these major rivals, acquiring Lipman in 2006 and the payment part of the Hypercom business including its brand in 2011.
In 1980 Jean-Jacques Poutrel and Michel Malhouitre in 1980 established Ingenico in France and developed their first payment terminal in 1984. It's Barcelona based R&D unit would lead the development of payment terminals for the next decade. Ingenico through a number of acquisitions would dominate the European market for payment terminals. They acquired French based Bull and UK based De La Rue payment terminal activity as well as German Epos in 2001.
Initially, information was captured from the magnetic strip on the back of the card, by swiping the card through the terminal. In the late 1990s, this started to be replaced by smart cards where the chip was embedded in the card. This was done for added security and required the card to be inserted into the credit card terminal. In the late 1990s and early 2000s contactless payment systems were introduced and the payment terminals were updated to include the ability to read this these cards using near field communication (NFC) technology.
Typical features
- Key entry (for customer not present mail and telephone order)
- Tips/gratuities
- Refunds and adjustments
- Settlement (including automatic)
- Pre-authorisation
- Payments using near field communication enabled devices
- Remote initialisation and software update
- POS integration
- Semi-integrated POS
- Multi-merchant capabilities
- Pen or PIN authorization by the customer
- Surcharge function
- Secure password operation
Major manufacturers
There are 3 main global players who offer both a wide range of payment terminals, sell each in over 100 countries worldwide, and have the long-term financial solidity to remain invested in upgrading payment terminals to the latest international payment industry standards.XXX . V00000 Computer terminal
A computer terminal is an electronic or electromechanical hardware device that is used for entering data into, and displaying or printing data from, a computer or a computing system. The teletype was an example of an early day hardcopy terminal , and predated the use of a computer screen by decades.
Early terminals were inexpensive devices but very slow compared to punched cards or paper tape for input, but as the technology improved and video displays were introduced, terminals pushed these older forms of interaction from the industry. A related development was timesharing systems, which evolved in parallel and made up for any inefficiencies of the user's typing ability with the ability to support multiple users on the same machine, each at their own terminal.
The function of a terminal is confined to display and input of data; a device with significant local programmable data processing capability may be called a "smart terminal" or fat client. A terminal that depends on the host computer for its processing power is called a "dumb terminal" or thin client. A personal computer can run terminal emulator software that replicates the function of a terminal, sometimes allowing concurrent use of local programs and access to a distant terminal host system.
The terminal of the first working programmable, fully automatic digital Turing-complete computer, the Z3, had a keyboard and a row of lamps to show results.
Hard-copy terminals
Early user terminals connected to computers were electromechanical teleprinters/teletypewriters (TeleTYpewriter, TTY), such as the Teletype Model 33 ASR, originally used for telegraphy or the Friden Flexowriter. Later printing terminals such as the DECwriter LA30 were developed. However printing terminals were limited by the speed at which paper could be printed, and for interactive use the paper record was unnecessary.
By the early 1970s, many users in the computer industry realized that an affordable video data entry terminal could supplant the ubiquitous punched cards and permit new uses for computers that would be more interactive. The problem was that the amount of memory needed to store the information on a page of text was comparable to the memory in low end minicomputers then in use. Displaying the information at video speeds was also a challenge and the necessary control logic took up a rack worth of pre-integrated circuit electronics. One company announced plans to build a video terminal for $15,000 and attracted a large backlog of orders, but folded when their engineering plans, which included fabricating their own ICs, proved too ambitious. Another approach involved the use of the storage tube, a specialized CRT developed by Tektronix that retained information written on it without the need to refresh.
The Datapoint 3300 from Computer Terminal Corporation was announced in 1967 and shipped in 1969, making it one of the earliest stand-alone display-based terminals. It solved the memory space issue mentioned above by using a digital shift-register design, and using only 72 columns rather than the later more common choice of 80.
Early VDUs
Early video computer displays were sometimes nicknamed "Glass TTYs" ("glass Teletypes") or "Visual Display Units" (VDUs), and used individual logic gates, with no CPU or very primitive LSI chips, yet quickly became extremely popular Input-Output devices on many different types of computer system once several suppliers gravitated to a set of common standards:
- ASCII character set (rather than, say, EBCDIC or anything specific to one company), but early/economy models often supported only capital letters (such as the original ADM-3, the Data General model 6052 – which could be upgraded to a 6053 with a lower-case character ROM – and the Heathkit H9)
- RS-232 serial ports (25-pin, ready to connect to a modem, yet some manufacturer-specific pin usage extended the standard, e.g. for use with 20-mA current loops)
- 24 lines (or possibly 25 – sometimes a special status line) of 80 characters of text (sometimes with two character width settings).
- Some type of blinking cursor that can be positioned (with arrow keys or "home" and other direct cursor address setting codes).
- Implementation of at least 3 control codes: Carriage Return (Ctrl-M), Line-Feed (Ctrl-J), and Bell (Ctrl-G), but usually many more, such as Escape sequences to provide underlining, dim or reverse-video character highlighting, and especially to clear the display and position the cursor.
Starting with the Datapoint 3300 in 1969, by the late 1970s and early 1980s, there were dozens of manufacturers of terminals, including Lear-Siegler, ADDS, Data General, DEC, Hazeltine Corporation, Heath/Zenith, Hewlett Packard, IBM, Televideo, and Wyse, many of which had incompatible command sequences (although many used the early ADM-3 as a starting point).
The great variations in the control codes between makers gave rise to software that identified and grouped terminal types so the system software would correctly display input forms using the appropriate control codes; In Unix-like systems the termcap or terminfo files, the stty utility, and the TERM environment variable would be used; in Data General's Business BASIC software, for example, at login-time a sequence of codes were sent to the terminal to try to read the cursor's position or the 25th line's contents using a sequence of different manufacturer's control code sequences, and the terminal-generated response would determine a single-digit number (such as 6 for Data General Dasher terminals, 4 for ADM 3A/5/11/12 terminals, 0 or 2 for TTY's with no special features) that would be available to programs to say which set of codes to use.
The great majority of terminals were monochrome, manufacturers variously offering green, white or amber and sometimes blue screen phosphors. (Amber was claimed to reduce eye strain). Terminals with modest colour capability were also available but not widely used, for example a colour version of the popular Wyse WY50, the WY350, offered 64 shades on each character cell.
"Intelligent" terminals
An "intelligent" terminal does its own processing, usually implying a microprocessor is built in, but not all terminals with microprocessors did any real processing of input: the main computer to which it was attached would have to respond quickly to each keystroke. The term "intelligent" in this context dates from 1969.
Notable examples include the IBM 2250 and IBM 2260, predecessors to the IBM 3270 and introduced with System/360 in 1964.
From the introduction of the IBM 3270, and the DEC VT100 (1978), the user and programmer could notice significant advantages in VDU technology improvements, yet not all programmers used the features of the new terminals (backward compatibility in the VT100 and later Televideo terminals, for example, with "dumb terminals" allowed programmers to continue to use older software).
Some dumb terminals had been able to respond to a few escape sequences without needing microprocessors: they used multiple printed circuit boards with many Integrated Circuits; the single factor that classed a terminal as "intelligent" was its ability to process user-input within the terminal—not interrupting the main computer at each keystroke—and send a block of data at a time (for example: when the user has finished a whole field or form). Most terminals in the early 1980s, such as ADM-3A, TVI912, Data General D2, DEC VT52, despite the introduction of ANSI terminals in 1978, were essentially "dumb" terminals, although some of them (such as the later ADM and TVI models) did have a primitive block-send capability.
The advance in microprocessors and lower memory costs made it possible for the terminal to handle editing operations such as inserting characters within a field that may have previously required a full screen-full of characters to be re-sent from the computer, possibly over a slow modem line. Around the mid 1980s intelligent terminals, costing less than most dumb terminals would have a few years earlier, could provide enough user-friendly local editing of data and send the completed form to the main computer. Providing even more processing possibilities, workstations like the Televideo TS-800 could run CP/M-86, blurring the distinction between terminal and Personal Computer.
Another of the motivations for development of the microprocessor was to simplify and reduce the electronics required in a terminal. That also made it practicable to load several "personalities" into a single terminal, so a Qume QVT-102 could emulate many popular terminals of the day, and so be sold into organizations that did not wish to make any software changes. Frequently emulated terminal types included:
- Lear Siegler ADM-3A and later models
- Televideo 910 to 950 (these models copied ADM3 codes and added several of their own, eventually being copied by Qume and others)
- Digital Equipment Corporation VT52 and VT100
- Data General D1 to D3 and especially D200 and D210
- Hazeltine Corporation H1500
- Tektronix 4014
- Wyse W50, W60 and W99
The ANSI X3.64 escape code standard produced uniformity to some extent, but significant differences remained (for example, the VT100, Heathkit H19 in ANSI mode, Televideo 970, Data General D460, and Qume QVT-108 terminals all followed the ANSI standard, yet differences might exist of codes from function keys, what character attributes were available, block-sending of fields within forms, "foreign" character facilities, and handling of printers connected to the back of the screen).
Most terminals were connected to minicomputers or mainframe computers and often had a green or amber screen. Typically terminals communicate with the computer via a serial port via a null modem cable, often using an EIA RS-232 or RS-422 or RS-423 or a current loop serial interface. IBM systems communicated over a coaxial cable using IBM's SNA protocol, but for many DEC, Data General and NCR (and so on) computers there were many visual display suppliers competing against the computer manufacturer for terminals to expand the systems. In fact, the instruction design for the Intel 8008 was originally conceived at Computer Terminal Corporation as the processor for the Datapoint 2200.
Contemporary
While early IBM PCs had single color green screens, these screens were not terminals. The screen of a PC did not contain any character generation hardware; all video signals and video formatting were generated by the video display card in the PC, or (in most graphics modes) by the CPU and software. An IBM PC monitor, whether it was the green monochrome display or the 16-color display, was technically much more similar to an analog TV set (without a tuner) than to a terminal. With suitable software a PC could, however, emulate a terminal, and in that capacity it could be connected to a mainframe or minicomputer. The Data General One could be booted into terminal emulator mode from its ROM. Eventually microprocessor-based personal computers greatly reduced the market demand for conventional terminals.
In the 1990s especially, "thin clients" and X terminals have combined economical local processing power with central, shared computer facilities to retain some of the advantages of terminals over personal computers:
Today, most PC telnet clients provide emulation of the most common terminal, the DEC VT100, using the ANSI escape code standard X3.64, or could run as X terminals using software such as Cygwin/X under Microsoft Windows or X.Org Server software under Linux.
Since the advent and subsequent popularization of the personal computer, few genuine hardware terminals are used to interface with computers today. Using the monitor and keyboard, modern operating systems like Linux and the BSD derivatives feature virtual consoles, which are mostly independent from the hardware used.
When using a graphical user interface (or GUI) like the X Window System, one's display is typically occupied by a collection of windows associated with various applications, rather than a single stream of text associated with a single process. In this case, one may use a terminal emulator application within the windowing environment. This arrangement permits terminal-like interaction with the computer (for running a command line interpreter, for example) without the need for a physical terminal device; it can even allow the running of multiple terminal emulators on the same device.
Capabilities
Text terminals
A text terminal, or often just terminal (sometimes text console) is a serial computer interface for text entry and display. Information is presented as an array of pre-selected formed characters. When such devices use a video display such as a cathode-ray tube, they are called a "video display unit" or "visual display unit" (VDU) or "video display terminal" (VDT).
The System console is a text terminal used to operate a computer. Modern computers have a built-in keyboard and display for the console. Some Unix-like operating systems such as Linux and FreeBSD have virtual consoles to provide several text terminals on a single computer.
The fundamental type of application running on a text terminal is a command line interpreter or shell, which prompts for commands from the user and executes each command after a press of Enter. This includes Unix shells and some interactive programming environments. In a shell, most of the commands are small applications themselves.
Another important application type is that of the text editor. A text editor occupies the full area of display, displays one or more text documents, and allows the user to edit the documents. The text editor has, for many uses, been replaced by the word processor, which usually provides rich formatting features that the text editor lacks. The first word processors used text to communicate the structure of the document, but later word processors operate in a graphical environment and provide a WYSIWYG simulation of the formatted output.
Programs such as Telix and Minicom control a modem and the local terminal to let the user interact with remote servers. On the Internet, telnet and ssh work similarly.
In the simplest form, a text terminal is like a file. Writing to the file displays the text and reading from the file produces what the user enters. In unix-like operating systems, there are several character special files that correspond to available text terminals. For other operations, there are special escape sequences, control characters and termios functions that a program can use, most easily via a library such as ncurses. For more complex operations, the programs can use terminal specific ioctl system calls. For an application, the simplest way to use a terminal is to simply write and read text strings to and from it sequentially. The output text is scrolled, so that only the last several lines (typically 24) are visible. Unix systems typically buffer the input text until the Enter key is pressed, so the application receives a ready string of text. In this mode, the application need not know much about the terminal. For many interactive applications this is not sufficient. One of the common enhancements is command line editing (assisted with such libraries as readline); it also may give access to command history. This is very helpful for various interactive command line interpreters.
Even more advanced interactivity is provided with full-screen applications. Those applications completely control the screen layout; also they respond to key-pressing immediately. This mode is very useful for text editors, file managers and web browsers. In addition, such programs control the color and brightness of text on the screen, and decorate it with underline, blinking and special characters (e.g. box drawing characters). To achieve all this, the application must deal not only with plain text strings, but also with control characters and escape sequences, which allow to move cursor to an arbitrary position, to clear portions of the screen, change colors and display special characters, and also respond to function keys. The great problem here is that there are so many different terminals and terminal emulators, each with its own set of escape sequences. In order to overcome this, special libraries (such as curses) have been created, together with terminal description databases, such as Termcap and Terminfo.
Dumb terminals
Dumb terminals are those that can interpret a limited number of control codes (CR, LF, etc.) but do not have the ability to process special escape sequences that perform functions such as clearing a line, clearing the screen, or controlling cursor position. In this context dumb terminals are sometimes dubbed glass Teletypes, for they essentially have the same limited functionality as does a mechanical Teletype. This type of dumb terminal is still supported on modern Unix-like systems by setting the environment variable TERM to dumb. Smart or intelligent terminals are those that also have the ability to process escape sequences, in particular the VT52, VT100 or ANSI escape sequences.
Graphical terminals
A graphical terminal can display images as well as text. Graphical terminals are divided into vector-mode terminals, and raster mode.
A vector-mode display directly draws lines on the face of a cathode-ray tube under control of the host computer system. The lines are continuously formed, but since the speed of electronics is limited, the number of concurrent lines that can be displayed at one time is limited. Vector-mode displays were historically important but are no longer used. Practically all modern graphic displays are raster-mode, descended from the picture scanning techniques used for television, in which the visual elements are a rectangular array of pixels. Since the raster image is only perceptible to the human eye as a whole for a very short time, the raster must be refreshed many times per second to give the appearance of a persistent display. The electronic demands of refreshing display memory meant that graphic terminals were developed much later than text terminals, and initially cost much more.
Most terminals today are graphical, that is, they can show images on the screen. The modern term for graphical terminal is "thin client". A thin client typically uses a protocol like X11 for Unix-terminals, or RDP for Microsoft Windows. The bandwidth needed depends on the protocol used, the resolution, and the color depth.
Modern graphic terminals allow display of images in color, and of text in varying sizes, colors, and fonts (type faces).
In the early 1990s an industry consortium attempted to define a standard, AlphaWindows, that would allow a single CRT screen to implement multiple windows, each of which was to behave as a distinct terminal. Unfortunately like I2O this suffered from being run as a closed standard: non-members were unable to obtain even minimal information and there was no realistic way a small company or independent developer could join the consortium. Possibly because of this the standard disappeared without trace.
Emulation
A terminal emulator is a piece of software that emulates a text terminal. In the past, before the widespread use of local area networking and broadband internet access, many computers would use a serial access program to communicate with other computers via telephone line or serial device.
When the first Macintosh was released, a program called MacTerminal was used to communicate with many computers, including the IBM PC.
Dec Terminal was one of the first terminal programs for the popular Altair.
The Win32 console on Windows does not emulate a physical terminal that supports escape sequences[8][dubious ] so SSH and Telnet programs (for logging in textually to remote computers) for Windows, including the Telnet program bundled with some versions of Windows, often incorporate their own code to process escape sequences.
The terminal emulators on most Unix-like systems, such as, for example, gnome-terminal, qterminal, xterm, terminal.app, do emulate physical terminals including support for escape sequences; e.g. xterm can emulate the VT220 and Tektronix 4010 hardware terminals.
Modes
Terminals can operate in various modes, relating to when they send input typed by the user on the keyboard to the receiving system (whatever that may be):
- Character mode (a.k.a. character-at-a-time mode): In this mode, typed input is sent immediately to the receiving system.
- Line mode (a.k.a. line-at-a-time mode): In this mode, the terminal provides a local line editing function, and sends an entire input line, after it has been locally edited, when the user presses a return key.[9] A so-called "line mode terminal" operates solely in this mode.[10]
- Block mode (a.k.a. screen-at-a-time mode): In this mode, the terminal provides a local full-screen data function. The user can enter input into multiple fields in a form on the screen (defined to the terminal by the receiving system), moving the cursor around the screen using keys such as Tab ↹ and the arrow keys and performing editing functions locally using insert, delete, ← Backspace and so forth. The terminal sends only the completed form, consisting of all the data entered on the screen, to the receiving system when the user presses an ↵ Enter key.[11][12][9]
There is a distinction between the return and the ↵ Enter keys. In some multiple-mode terminals, that can switch between modes, pressing the ↵ Enter key when not in block mode does not do the same thing as pressing the return key. Whilst the return key will cause an input line to be sent to the host in line-at-a-time mode, the ↵ Enter key will rather cause the terminal to transmit the contents of the character row where the cursor is currently positioned to the host, host-issued prompts and all.[
Different computer operating systems require different degrees of mode support when terminals are used as computer terminals. The POSIX terminal interface, as provided by Unix and POSIX-compliant operating systems, does not accommodate block-mode terminals at all, and only rarely requires the terminal itself to be in line-at-a-time mode, since the operating system is required to provide canonical input mode, where the terminal device driver in the operating system emulates local echo in the terminal, and performs line editing functions at the host end. Most usually, and especially so that the host system can support non-canonical input mode, terminals for POSIX-compliant systems are always in character-at-a-time mode. In contrast, IBM 3270 terminals connected to MVS systems are always required to be in block
Communication endpoint
A communication endpoint is a type of communication network node. It is an interface exposed by a communicating party or by a communication channel. An example of the latter type of a communication endpoint is a publish-subscribe topic or a group in group communication systems.
A communication endpoint is a discoverable node of communication whose scope may be varied to narrow or broaden the discovery zone. Endpoints facilitate a standard programmable layer of abstraction whereby heterogeneous software systems and/or subsystems may communicate with each other and that the means of communication are decoupled from the communicating subsystems.
In the context of telecommunications, a terminal is a device which ends a telecommunications link and is the point at which a signal enters and/or leaves a network. Examples of equipment containing network terminations are telephones, fax machines, computer terminals and network devices, printers and workstations.
XXX . V0000000 Wire transfer
Wire transfer, bank transfer or credit transfer is a method of electronic funds transfer from one person or entity to another. A wire transfer can be made from one bank account to another bank account or through a transfer of cash at a cash office.
Different wire transfer systems and operators provide a variety of options relative to the immediacy and finality of settlement and the cost, value, and volume of transactions. Central bank wire transfer systems, such as the Federal Reserve's FedWire system in the United States, are more likely to be real time gross settlement (RTGS) systems. RTGS systems provide the quickest availability of funds because they provide immediate "real-time" and final "irrevocable" settlement by posting the gross (complete) entry against electronic accounts of the wire transfer system operator. Other systems such as CHIPS provide net settlement on a periodic basis. More immediate settlement systems tend to process higher monetary value time-critical transactions, have higher transaction costs, and have a smaller volume of payments. A faster settlement process allows less time for currency fluctuations while money is in transit.
The first widely used service for wire transfers was launched by Western Union in 1872 on its existing telegraph network. Using passwords and code books, a telegraph operator in one office could "wire" money that had been paid to that office by the sending customer to another telegraph office to be paid out to the receiving customer. By 1877 the service was used to transfer almost $2.5 million each year.[1] Because the earliest wire transfers were using telegraph networks, it was termed telegraphic transfer and this name is still used in some countries, although more advanced electronic transfer networks are used .
A bank wire transfer is effected as follows:
- The entity wishing to do a transfer approaches a bank and gives the bank the order to transfer a certain amount of money. IBAN and BIC codes are given as well so the bank knows where the money needs to be sent.
- The sending bank transmits a message, via a secure system (such as SWIFT or Fedwire), to the receiving bank, requesting that it effect payment according to the instructions given.
- The message also includes settlement instructions. The actual transfer is not instantaneous: funds may take several hours or even days to move from the sender's account to the receiver's account.
- Either the banks involved must hold a reciprocal account with each other, or the payment must be sent to a bank with such an account, a correspondent bank, for further benefit to the ultimate recipient.
Regulation and price
Since 2009 the European Union Regulation No 924/2009 controls cross-border payments in the European Union. In the new regulation Article 1 (q.v., Ref.4) states that an IBAN/BIC transfer within Single Euro Payments Area (SEPA) must not cost more than a national transfer, no matter which currency is used. The receiving bank can charge for exchanging to local currency.Prior to this, in 2002 the European Union relegated the regulation of fees a bank may charge for payments in euro between EU member states down to the domestic level,[4] resulting in very low or no fees for electronic transfers within the Eurozone. In 2005, Iceland, Liechtenstein, and Norway joined the EU regulation on electronic transfers. However, this regulation was superseded by the Single Euro Payments Area (SEPA), consisting of 32 European countries.
In the United States, domestic wire transfers are governed by Federal Regulation J[5] and by Article 4A of the Uniform Commercial Code.[6] US wire transfers can be costly. In 2016, among the 15 largest retail banks, the average fee for an outgoing domestic wire was $25. Incoming domestic wire fees were about evenly split between $0 (free) and $15.
Security
With bank-to-bank wire transfer, each account holder must have a proven identity. Chargebacks are unlikely, although wires can be recalled. Information contained in wires are transmitted securely through encrypted communications methods. The price of bank wire transfers varies greatly, depending on the bank and its location; in some countries, the fee associated with the service can be costly.Wire transfers done through cash offices are essentially anonymous[citation needed] and are designed for transfer between persons who trust each other. It is unsafe to send money by wire to an unknown person to collect at a cash office; the receiver of the money may, after collecting it, not provide whatever goods or services they promised in return for the payment, but instead simply disappear. This scam has been used often,[8] especially in the so-called 419 scams which often nominate Western Union for collection.
International transfers involving the United States are subject to monitoring by the Office of Foreign Assets Control (OFAC), which monitors information provided in the text of the wire and then decides whether, according to the US Government's federal regulations[5][6] and political positions, money is being transferred to terrorist groups, or countries or entities under sanction by the United States government. If a financial institution suspects that funds are being sent from or to one of these entities, it must block the transfer and freeze the funds.
SWIFT or IBAN wire transfers are not completely free of vulnerabilities. Every intermediary bank that handles a wire transaction can take a fee directly out of the wire payload (the assets being transferred) without the account holder's knowledge or consent. In many places, there is no legislation or technical means to protect customers from this practice. If bank S is the sending bank (or brokerage), and bank R is the receiving bank (or brokerage), and banks I1, I2 and I3 are intermediary banks, the client may only have a contract with bank S and/or R, but banks I1, I2 and I3 can (and often do) take money from the wire without any direct arrangement with the client. Clients are sometimes taken by surprise when less money arrives at bank R. Contrast this with cheques, where the amount transferred is guaranteed in full, and fees (if there are any) can be charged only at endpoint banks.
The European Union offers some partial protection from this practice by prohibiting European intermediary banks from taking a fee out of the amount being transferred, even for transatlantic transfers.[ However, it's still common practice for a European brokerage firm to state that they charge no transfer fee, and then contract their bank to take an unpublished fee from the amount transferred as a means to compensate their bank with their clients' assets—e.g., CMC Markets implements this policy in partnership with Natwest.
Methods
Retail money transfers
One of the largest companies that offer wire transfer is Western Union, which allows individuals to transfer or receive money without an account with Western Union or any financial institution.[10] Concern and controversy about Western Union transfers have increased in recent years, because of the increased monitoring of money-laundering transactions, as well as concern about terrorist groups using the service, particularly in the wake of the September 11, 2001 attacks. Although Western Union keeps information about senders and receivers, some transactions can be done essentially anonymously, for the receiver is not always required to show identification.There are other companies in this market, like ACE Money Transfer, RIA Financial Services, MoneyGram and VFX Financial PLC and LCC Money Transfer (both based in Europe) as well as Azimo, Dwolla, TransferGo, and TransferWise.
Another option for consumers and businesses transferring money internationally is to use specialised brokerage houses for their international money transfer needs. Many of these specialised brokerage houses can transfer money at better exchange rates compared to banks, thus saving up to 4%. These providers can offer a range of currency exchange products like Spot Contracts, Forward Contracts and Limit Orders. However, not all such providers are regulated by appropriate government bodies. For example, in the UK, even though such companies are regulated by the Financial Conduct Authority, not all of them fall under (FCA) scrutiny. Regulators include the Australian Securities and Investments Commission (ASIC), the Financial Transactions Reports Analysis Centre of Canada (FINTRAC) in Canada, the Hong Kong Customs and Excise Department in China and the Financial Conduct Authority (FCA) in the UK.
International
Most international transfers are executed through SWIFT, a co-operative society founded in 1974 by seven international banks, which operate a global network to facilitate the transfer of financial messages. Using these messages, banks can exchange data for the transfer of funds between financial institutions. SWIFT's headquarters are in La Hulpe, on the outskirts of Brussels, Belgium. The society also acts as a United Nations–sanctioned international standards body for the creation and maintenance of financial-messaging standards. See SWIFT Standards.Each financial institution is assigned an ISO 9362 code, also called a Bank Identifier Code (BIC) or SWIFT Code. These codes are generally eight characters long.[17] For example: Deutsche Bank is an international bank with its head office in Frankfurt, Germany, the SWIFT Code for which is DEUTDEFF:
- DEUT identifies Deutsche Bank.
- DE is the country code for Germany.
- FF is the code for Frankfurt.
European banks making transfers within the European Union and within Switzerland also use the International Bank Account Number, or IBAN.
International prepaid cards
International prepaid cards are an alternative way for transferring funds. Companies can provide a debit card for worldwide employees' payments. The recipients don’t need to have a bank account and can use the card in places that a debit card is accepted at point-of-sale or online and may withdraw funds in local currency at an ATM.United States of America
Banks in the United States use SWIFT to send messages to notify banks in other countries that a payment has been made. Banks use the CHIPS or Fedwire system to actually effect the payment.Domestic bank-to-bank transfers are conducted through the Fedwire system, which uses the Federal Reserve System and its assignment of routing transit number, which uniquely identify each bank.
Other electronic transfers
In the United States, such EFTS transfers are often called "ACH transfers," because they take place through the Automated Clearing House.
One important way ACH transfers differ from wire transfer is that the recipient can initiate it. There are of course restrictions, but this is the way people often set up automatic bill payment with utility companies, for example.
XXX . V00000000 Automated Clearing House
Automated Clearing House (ACH) is an electronic network for financial transactions in the United States. ACH processes large volumes of credit and debit transactions in batches. ACH credit transfers include direct deposit, payroll and vendor payments. ACH direct debit transfers include consumer payments on insurance premiums, mortgage loans, and other kinds of bills. Debit transfers also include new applications such as the point-of-purchase (POP) check conversion pilot program sponsored by the National Automated Clearing House Association (NACHA). Both the government and the commercial sectors use ACH payments. Businesses increasingly use ACH online to have customers pay, rather than via credit or debit cards.
ACH is a computer-based clearing and settlement facility established to process the exchange of electronic transactions between participating depository institutions.
Rules and regulations that govern the ACH network are established by NACHA and the Federal Reserve. In 2015, this network processed nearly 24 billion ACH transactions with a total value of $41.6 trillion.[2] Credit card payments are handled by separate networks.
The Federal Reserve Banks, through the FedACH system, are collectively the nation's largest ACH operator. In 2005, they processed 60% of commercial interbank ACH transactions; the remaining 40% was processed by the Electronic Payments Network (EPN), the United States' only private-sector ACH operator. EPN and the Reserve Banks rely on each other for the processing of some transactions when either party to the transaction is not their customer. These interoperator transactions are settled by the Reserve Banks. These Automated Clearing houses are used to settle transactions between Banks and Government and Central Bank. Banks use Reserve deposits to settle transactions because bank credit is usable only in the bank in which it was created. Central banks control the supply of Reserve Deposits. Reserve Deposits are a digital form of cash which is created by the central banks
Uses of the ACH payment system
- Bank treasury management departments sell this service to business and government customers
- Business-to-business payments
- Direct debit payment of consumer bills such as mortgages, loans, utilities, insurance premiums, rents, and any other regular payment
- Direct deposit of payroll, Social Security and other government payments, and tax refunds
- E-commerce payments
- Federal, state, and local tax payments
- Non-immediate transfer of funds between accounts at different financial institutions (when a real-time transfer is required, a wire transfer using a system such as the Federal Reserve's Fedwire is employed instead)
- Charitable Donations.
SEC codes
Some common Standard Entry Class (SEC) codes: AT- ARC
- Accounts receivable conversion. A consumer check converted to a one-time ACH debit. The difference between ARC and POP is that ARC can result from a check mailed in whereas POP is in-person.
- BOC
- Back office conversion. A single entry debit initiated at the point of purchase or at a manned bill payment location to transfer funds through conversion to an ACH debit entry during back office processing. Unlike ARC entries, BOC conversions require that the customer be present, and that the vendor post a notice that checks may be converted to BOC ACH entries.
- CBR
- Corporate cross-border payment. Used for international business transactions, replaced by SEC Code IAT.
- CCD
- Corporate Credit or Debit Entry. Used to consolidate and sweep cash funds within an entity's controlled accounts, or make/collect payments to/from other corporate entities.
- CIE
- Customer Initiated Entries. Use limited to credit applications where the consumer initiates the transfer of funds to a company for payment of funds owed to that company, typically through some type of home banking product or bill payment service provider.
- CTX
- Corporate trade exchange. Transactions that include ASC X12 or EDIFACT information.
- DNE
- Death notification entry. Issued by the federal government.
- IAT
- International ACH transaction. This is a SEC code for cross-border payment traffic to replace the PBR and CBR codes. The code has been implemented since September 18, 2009.
- PBR
- Consumer cross-border payment. Used for international household transactions, replaced by SEC Code IAT.
- POP
- Point-of-purchase. A check presented in-person to a merchant for purchase is presented as an ACH entry instead of a physical check.
- POS
- Point-of-sale. A debit at an electronic terminal initiated by use of a plastic card. An example is using your debit card to purchase gas.
- PPD
- Prearranged payment and deposits. Used to credit or debit a consumer account. Popularly used for payroll direct deposits and preauthorized bill payments.
- RCK
- Represented check entries. A physical check that was presented but returned because of insufficient funds may be represented as an ACH entry.
- TEL
- Telephone-initiated entry. Oral authorization by telephone to issue an ACH entry such as checks by phone. (TEL code allowed for inbound telephone orders only. NACHA disallows the use of this code for outbound telephone solicitations unless a prior business arrangement with the customer has been established.)
- WEB
- Web-initiated entry. Electronic authorization through the Internet to create an ACH entry.
- XCK
- Destroyed check entry. A physical check that was destroyed because of a disaster can be presented as an ACH entry.
XXX . V00000000 Money transmitter
In the legal code of the United States, a money transmitter or money transfer service is a business entity that provides money transfer services or payment instruments. Money Transmitters in the US are part of a larger group of entities called Money Service Businesses or MSBs. Under federal law, 18 USC § 1960, businesses are required to register for a Money Transmitter license where their activity falls within the state definition of a money transmitter.
Regulation
Forty-nine US states (sans Montana) regulate money transmitters although the laws vary from one state to the other. Most of the states require a money transmitter surety bond with widely ranging amounts from as little as $25,000 to over $1 million and maintaining a minimum capital requirement. There is an association of state regulators, the Money Transfer Regulators Association (MTRA)[5] that seeks to create uniformity and common practices and efficient and effective regulation of money transmission industry in the United States of America. The MTRA membership consists of state regulatory authorities in charge of regulating money transmitters and sellers of traveler’s checks, money orders, drafts and other money instruments.The money transmitters themselves have a separate association, the National Money Transmitters Association (NMTA)[6] to have a voice in shaping and developing this industry. A related international association, the International Money Transfer Conferences (IMTC), brings together the money transfer industry once a year for the IMTC Miami conference. In 2012 the IMTC brought together close to 400 participants, 67% from the US.
The Financial Crimes Enforcement Network (FinCEN) of the U.S. Treasury Department requires MSBs to register.[9] It is also a felony to engage in money transmission without a license in any state that requires a license to operate.[10] Internet and mobile-based payment services are also required to seek a state money transmitter license to offer services to individuals residing in the state.
FINCEN has also ruled that Informal Value Transfer Systems (IVTS) are considered money transmitters for the purposes of registration and licensing. FINCEN defines an IVTS as "any system, mechanism, or network of people that receives money for the purpose of making the funds or an equivalent value payable to a third party in another geographic location, whether or not in the same form". These are known as Hawala in the Middle East, Afghanistan and Pakistan, as "hundi" in India and '"fei ch’ien" in China.
In regulations enacted in 2012 under the Dodd-Frank Act the Consumer Financial Protection Bureau (CFPB)[12] extended its regulation under a "Remittance Rule" that added some additional protection for US consumers who send money electronically to foreign countries. The rule targets any remittance institution defined as consumer-to-consumer transfers of low monetary value, made via money transmitters, banks or credit unions, through wire transfers or automated clearing house (ACH) transactions, to businesses as well as to individuals in foreign countries
Remittance
A remittance is a transfer of money by a foreign worker to an individual in his or her home country. Money sent home by migrants competes with international aid as one of the largest financial inflows to developing countries. Workers' remittances are a significant part of international capital flows, especially with regard to labour-exporting countries. In 2014, $436 billion went to developing countries, setting a new record. Overall global remittances totaled $582 billion in 2015. Some countries, such as India and China, receive tens of billions of US dollars in remittances each year from their expatriates. In 2014, India received an estimated $70 billion and China an estimated $64 billion.

Remittance advertising in Oxford Street, London with Polish and Russian
Global extent
Remittances are playing an increasingly large role in the economies of many countries. They contribute to economic growth and to the livelihoods of those countries. According to World Bank estimates, remittances will total US$585.1 billion in 2016, of which US$442 billion[4] went to developing countries that involved 250 million migrant workers.[5] For some individual recipient countries, remittances can be as high as a third of their GDP.Top recipient countries
| Country | Remittances 2012 | Remittances 2013 | Remittances 2014 | Remittances 2015 | Remittances 2016 | Remittances 2017 |
|---|---|---|---|---|---|---|
| 68.82 | 69.97 | 70.97 | 72.20 | 62.7 | 65.4 | |
| 57.99 | 59.49 | 61.49 | 63.90 | 61.0 | 62.9 | |
| 24.61 | 26.70 | 27.90 | 29.80 | 29.9 | 32.8 | |
| 23.37 | 23.02 | 24.50 | 25.70 | 28.5 | 30.5 | |
| 14.01 | 14.63 | 17.80 | 20.10 | 19.8 | 22.3 | |
| 20.63 | 20.89 | 20.88 | 20.89 | 19.0 | 19.8 | |
| 19.24 | 17.83 | 19.83 | 20.40 | 16.6 | 18.2 | |
| 14.24 | 13.86 | 15.10 | 15.80 | 13.7 | 13.8 | |
| 10.00 | 11.00 | 11.80 | 12.30 | 13.4 | 12.9 |
As a share of GDP, the top recipients of remittances in 2013 were Timor-Leste (216.6%), Tajikistan (42.1%), Kyrgyzstan (31.5%), Nepal (28.8%), Moldova (24.9%), Lesotho (24.4%), Samoa (23.8%), Haiti (21.1%), Armenia (21.0%), The Gambia (19.8%), Liberia (18.5%), Lebanon (17.0%), Honduras (16.9%), El Salvador (16.4%), Kosovo (16.1%), Jamaica (15.0%) and Bosnia and Herzegovina (13.4%, which is about 1.817 billion $ on 31 December 2014).[7][9]
Asia
A majority of the remittances have been directed to Asian countries like India (approx. 62.7 billion USD in 2016), China (approx. 61.0 billion USD in 2016), the Philippines (approx. 29.9 billion USD in 2016), Pakistan (19.8 billion USD in 2016) and more.[10]Most of the remittances happen by the conventional channel of agents, like Western Union, Ria Money Transfer, MoneyGram, UAE Exchange, and similar. However, with the increasing relevance and reach of the Internet, online and mobile phone money transfers have grown significantly.[11] Several companies such as Everex are exploring blockchain (the technology underlying cryptocurrencies such as BitCoin and Ethereum) to create descentralized microfinance and remittance services, cutting transaction fees and offering extremely competitive rates, while at the same time including underbanked individuals (people without a bank account) to the world economy.
Jordan
The flow of remittances to Jordan experienced rapid growth during the 1970s and 1980s when Jordan started exporting skilled labour to the Persian Gulf. These remittances represent an important source of funding for many developing countries, including Jordan.[12] According to the World Bank data on remittances, with about 3 billion USD in 2010 Jordan ranked at 10th place among all developing countries. Jordan ranked among the top 20 recipients of remittances for the preceding decade. In addition, the Arab Monetary Fund (AMF) statistics in 2010 indicate that Jordan was the third biggest recipient of remittances among Arab countries after Egypt and Lebanon. The host countries that have absorbed most of the Jordanian expatriates are Saudi Arabia and the United Arab Emirates, where the available data indicate that about 90% of Jordanian migrants are working in the Persian Gulf.Philippines
According to a World Bank Study,[14] the Philippines is the second largest recipient for remittances in Asia. It was estimated in 1994 that migrants sent over US$2.6 billion back to the Philippines through formal banking systems. With the addition of money sent through private finance companies and return migrants, the 1994 total was closer to US$6 billion annually.The total is estimated to have grown by 7.8 per cent annually to reach US$21.3 billion in 2010. Remittances are a reliable source of revenue for the Philippines, accounting for 8.9 per cent of the country's GDP.
The Estrada administration in 2000 declared it "The Year of Overseas Filipino Worker in the Recognition of the Determination and Supreme Self-Sacrifice of Overseas Filipino Workers." This declaration connects monetary remittances of overseas workers as the top foreign-exchange earnings in the Philippines.
Latin America and the Caribbean
In Latin America and the Caribbean, remittances play an important role in the economy of the region, totaling over 66.5 billion USD in 2007, with about 75% originating in the United States. This total represents more than the sum of Foreign direct investment and official development aid combined. In seven Latin American and Caribbean countries, remittances even account for more than 10% of GDP and exceed the dollar flows of the largest export product in almost every country in the region.Percentages ranged from 2% in Mexico, to 18% in El Salvador, 21% in Honduras, and up to 30% in Haiti.[18] The Inter American Development Bank's Multilateral Investment Fund (IDB-MIF) has been the leading agency on regional remittance research.
Mexico received remittance inflows of almost US$24 billion in 2007, 95% of which originated in the US.
North America
The United States
A 2004 study found that over 60% of the 16.5 million Latin American-born adults who resided in the United States at the time of the survey regularly sent money home. The remittances sent by these 10 million immigrants were transmitted via more than 100 million individual transactions per year and amounted to an estimated $30 billion during 2004. Each transaction averaged about $150–$250, and, because these migrants tended to send smaller amounts more frequently than others, their remittances had a higher percentage of costs due to transfer fees.Migrants sent approximately 10% of their household incomes; these remittances made up a corresponding 50–80% of the household incomes for the recipients. Significant amounts of remittances were sent from 37 U.S. states, but six states were identified as the "traditional sending" states: New York (which led the group with 81% of its immigrants making regular remittances), California, Texas, Florida, Illinois, and New Jersey. The high growth rate of remittances to Mexico (not the total amount) is unlikely to continue. In fact, according to the Mexican central bank, remittances grew just 0.6 during the first six months of 2007, as compared to 23% during the same period in 2006. Experts attribute the slowdown to a contraction in the U.S. construction industry, tighter border controls, and a crackdown in the U.S. on illegal immigration.
Remittance culture in the US has contributed to the formation of "micro-geographies," tightly knit networks that integrate U.S. communities with communities throughout Latin America, such as migrants from Oaxaca, Mexico who have settled in Venice Beach, California. Oaxacans not only send money back to their communities, but they also travel back and forth extensively.
As of recently, remittances from the U.S. to Latin America have been on the decline. While there were USD 69.2 billion worth of remittances sent in 2008, that figure has fallen to USD 58.9 billion for 2011. This trend is a result of many factors including the global recession, more economic opportunity in Latin American countries, and rising fees charged by coyotes to smuggle immigrants across the border.
The pattern of migration has changed from a circular flow, in which immigrants work in the U.S. for a few years before returning to their families in their home countries, to a one-way stream whereby migrants find themselves stuck in the United States. As a result, the new wave of migrants are both less likely to leave and more likely to stay in the U.S. for longer periods of time. Overall, this trend has contributed to falling levels of remittances sent to Latin American countries from the United States.
Africa
Remittances to Africa play an important role to national economies. However, little data exists as many rely on informal channels to send money home. Immigrants from Africa today number approximately 20 to 30 million adults, who send around $40 billion USD annually to their families and local communities back home. For the region as a whole, this represents 50 percent more than net official development assistance (ODA) from all sources, and, for most countries, the amount also exceeds foreign direct investment (FDI). In several fragile states, remittances are estimated to exceed 50 percent of GDP.[21]Most African countries restrict the payment of remittances to banks, which in turn, typically enter into exclusive arrangements with large money transfer companies, like Western Union or Money Gram, to operate on their behalf. This results in limited competition and limited access for consumers, which allows these Money Transfer Operators (MTOs) to charge the highest fees for remittances in the world.[22] However, there are a number of new players aiming to disrupt this established MTO model, such as Xoom and Willstream, which leverage increasing mobile phone penetration in the region and provide different rate structures to Diaspora customers.[23][24]
According to a World Bank study,[14] Nigeria is by far the top remittance recipient in Africa, accounting for $10 billion in 2010, a slight increase over the previous year ($9.6 billion). Other top recipients include Sudan ($3.2 billion), Kenya ($1.8 billion), Senegal ($1.2 billion), South Africa ($1.0 billion), Uganda ($0.8 billion), Lesotho ($0.5 billion), Ethiopia ($387 million), Mali ($385 million), and Togo ($302 million). As a share of Gross Domestic Product, the top recipients in 2009 were: Lesotho (25%), Togo (10%), Cape Verde (9%), Guinea-Bissau (9%), Senegal (9%), Gambia (8%), Liberia (6%), Sudan (6%), Nigeria (6%), and Kenya (5%).
Overview
Remittances are not a new phenomenon in the world, being a normal concomitant to migration which has always been a part of human history. Several European countries, for example Spain, Italy and Ireland were heavily dependent on remittances received from their emigrants during the 19th and 20th centuries. In the case of Spain, remittances amounted to the 21% of all of its current account income in 1946.All of those countries created policies on remittances developed after significant research efforts in the field. For instance, Italy was the first country in the world to enact a law to protect remittances in 1901 while Spain was the first country to sign an international treaty (with Argentina in 1960) to lower the cost of the remittances received.Since 2000, remittances have increased sharply worldwide, having almost tripled to $529 billion in 2012. In 2012, migrants from India and China alone sent more than $130 billion to their home countries.
In 2004 the G8 met at the Sea Island Summit and decided to take action to lower the costs for migrant workers who send money back to their friends and families in their country of origin. In light of this, various G8 government developmental organizations, such as the UK government's Department for International Development (DFID) and USAID began to look into ways in which the cost of remitting money could be lowered.
In September 2008, the World Bank established the first international database of remittance prices. The Remittance Prices Worldwide Database[39] provides data on sending and receiving remittances for over 200 "country corridors" worldwide. The "corridors" examined include remittance flows from 32 major sending countries to 89 receiving countries, which account for more than 60% of total remittances to developing countries. The resulting publication of the Remittance Prices Worldwide Database serves four major purposes: benchmarking improvements, allowing comparisons across countries, supporting consumers’ choices, and putting pressure on service providers to improve their services.
At the July 2009 summit in L'Aquila, Italy, G8 heads of government and states endorsed the objective of reducing the cost of remittance services by five percentage points in five years. To drive down costs, the World Bank has begun certifying regional and national databases that use a consistent methodology to compare the cost of sending remittances.
At the G20 2011 Summit in Cannes, Bill Gates stated that, "If the transaction costs on remittances worldwide were cut from where they are today at around 10% to an average of 5%…it would unlock $15bn a year in poor countries." A number of low-cost online services such as Azimo have emerged with the objective of lowering the cost of money transfers to developing and emerging economies.
Dynamics
Emergencies
During disasters or emergencies, remittances can be a vital source of income for people whose other forms of livelihood may have been destroyed by conflict or natural disaster. According to the Overseas Development Institute, this is being increasingly recognized as important by aid actors who are considering better ways of supporting people in emergency responses.Potential security concerns
The recent internationally coordinated effort to stifle possible sources of money laundering and/or terrorist financing has increased the cost of sending remittances, directly increasing costs to the companies facilitating the sending, and indirectly increasing the costs to the person remitting. As in some corridors a sizable amount of remittances is sent through informal channels (family connections, traveling friends, local money lenders, etc.). According to the World Bank, some countries do not report remittances data.Moreover, when data is available, the methodologies used by countries for remittance data compilation are not publicly available. A 2010 world survey of central banks found significant differences in the quality of remittance data collection across countries: some central banks only used remittances data reported from commercial banks, neglecting to account for remittance flows via money transfer operators and post offices.
Remittances can be difficult to track and potentially sensitive to money laundering (AML) and terror financing (CTF) concerns. Since 9/11 many governments and the Financial Action Task Force (FATF) have taken steps to address informal value transfer systems. This is done through nations' Financial Intelligence Units (FIUs). The principle legislative initiatives in this area are the USA PATRIOT Act, Title III in the United States and, in the EU, through a series of EU Money Laundering Directives. Though no serious terror risk should be associated with migrants sending money to their families, misuse of the financial system remains a serious government concern.
Economic benefits for developing countries
The extent to which remittances produce benefits for developing countries is contested.World Bank economists contend that remittance receivers' higher propensity to own a bank account means that remittances can promote access to financial services for the sender and recipient, claimed to be an essential aspect of leveraging remittances to promote economic development. Meanwhile, critical migration scholars have expressed concern about the ability of remittances to address the structural causes of economic underdevelopment and see an increasing policy emphasis on finance as symptomatic of a paradigmatic shift towards a 'self-help development' that burdens the poor.
Remittances are generally thought to be counter-cyclical. The stability of remittance flows amidst financial crises and economic downturns make them a reliable source of foreign exchange earnings for developing countries. As migrant remittances are sent cumulatively over the years and not only by new migrants, remittances are able to be persistent over time. This is particularly true of remittances sent by circular migrants, migrant workers who move back and forth between their home and host countries in a temporary and repetitive manner. At the state level, countries with diversified migration destinations are likely to have more sustainable remittance flows.
From a macroeconomic perspective, there is no conclusive relationship between remittances and GDP growth. While remittances can boost aggregate demand and thereby spur economic activity, other research indicates that remittances may also have adverse macroeconomic impacts by increasing income inequality and reducing labour supply among recipient countries.
The World Bank and the Bank for International Settlements have developed international standards for remittance services.[
XXX . V00000000 study case ; Acquisition of Qualifying Holdings
Acquisition of Qualifying Holdings
Legislative Requirements
The requirements in relation to the acquisition and disposal of Qualifying Holdings in credit institutions are set out in Chapter 2 of Part 3 of the European Union (Capital Requirements) Regulations 2014 (S.I. No. 158 of 2014).Guidance
Potential acquirers of qualifying holdings in credit institutions should refer to the Guidelines for the prudential assessment of acquisitions and increases in holdings in the financial sector required by Directive 2007/44/EC which was jointly published by the Committee of European Securities Regulators (CESR), the European Banking Authority (formerly the Committee of European Banking Supervisors (CEBS)) and the Committee of European Insurance and Occupational Pensions Supervisors (CEIOPS) on 18 December 2008.Notification and Assessment Process
The form below is to be used to provide prior notification to the Central Bank of Ireland and thereby to the European Central Bank, which is the competent authority for the approval of Qualifying Holding applications, of proposed acquisitions of, or increases in, direct or indirect qualifying holdings in respect of Irish authorised credit institutions.To avoid undue delays in the notification and assessment process, and to reduce the risk of submitting incomplete notifications, the proposed acquirer is expected to engage in pre-notification contacts/discussions with the Central Bank of Ireland.
Introduction to Money Transmission Businesses
A Money Transmission Service means a service that involves transmitting money by any means, other than a service -(a) that is a payment service to which the European Communities (Payment Services) Regulations 2009 (S.I. No. 383 of 2009) apply,
(b) that is provided to customers on a basis that is ancillary to any other services apart from debt management services,
(c) that is provided by—
(i) any charitable organisation within the meaning of section 2(1) of the Charities Act 2009,
(ii) the Money Advice and Budgeting Service,
(iii) any licensed bank, building society, credit union or friendly society,
(iv) a barrister, solicitor or accountant who provides money transmission services only in an incidental manner and is subject to regulation by a professional body,
(v) the Insolvency Service of Ireland, any approved intermediary authorised under section 47 of the Personal Insolvency Act 2012 acting as such or any personal insolvency practitioner authorised under Chapter 1 of Part 5 of that Act carrying on practice as such,
(vi) personal representatives (within the meaning of section 3 of the Succession Act 1965),
(vii) trustees of a trust, other than a trust which is established to provide money transmission services,
(viii) the Bank,
(ix) An Post,
(x) the National Asset Management Agency,
(xi) the National Treasury Management Agency,
(xii) the National Consumer Agency, and
(xiii) any other person constituted, or holding office, under an enactment or funded (in whole or in part).
The Central Bank is responsible for the approval of certain charges imposed by a Money Transmission Business in accordance with Section 149A of the Consumer Credit Act, 1995 (as amended) - It is also responsible for monitoring the anti-money laundering and prevention of the financing of terrorism measures adopted by Money Transmission Businesses.
Payment Institutions
A ‘payment institution’ is defined in the Payment Services Directive ('Directive') as a legal person (i.e. must be incorporated - sole traders cannot be authorised) that has been granted authorisation in accordance with Regulation 18 of the European Communities (Payment Services) Regulation 2009 ('Regulations') to provide and execute payment services throughout the European Community.The Directive was transposed by S.I. No. 383 of 2009 European Communities (Payment Services) Regulations 2009 which became effective in Ireland on 1 November 2009. The Central Bank of Ireland ('Central Bank') is the competent authority for the purpose of implementation of the Directive.
Payment institutions must obtain authorisation from the Central Bank in order to provide payment services. The provisions of the Regulations will apply to persons providing ‘payment services’.
Electronic Money Institutions
Progress in technology has contributed to the development of a new kind of payment instrument – electronic money.This may be in the form of value stored on a technical device such as a chip card or indeed, a computer memory. Electronic money (E-Money) can be best described as a digital form of cash since it has many of the characteristics of cash.
Customers buy the electronic equivalent of coins and notes. The customer, in effect, has exchanged cash for another means of payment. Instead of using a debit card (which requires a bank account) or a credit card (which requires a contract agreement) the customer has purchased a non-cash means of payment, which can be used in much the same way as cash or other forms of card payment but without the requirement of third party authorisation.
E-money can therefore be defined as monetary value as represented by a claim on the issuer, which is:
- electronically stored
- issued on receipt of funds for the purposes of making payment transactions
- accepted as means of payment by a natural or legal person other than the issuer
Directive 2009/110/EC of the European Parliament and of the Council on the taking up, pursuit and prudential supervision of the business of electronic money institutions [the 'Directive'] was signed on 16 September 2009. Member States had to adopt and publish, not later than 30 April 2011, the laws, regulations and administrative provisions necessary to comply with the Directive. The Directive was transposed into Irish law through the European Communities (Electronic Money) Regulations 2011.
Introduction to Debt Management Firms
Under Part V of the Central Bank Act 1997 (as amended) (the “Act”) a “debt management firm” is defined as meaning:“a person who for remuneration provides debt management services to one or more consumers, other than an excepted person[1]”
The Act defines “debt management services” as meaning:
“(a) giving advice about the discharge of debts (in whole or in part), including advice about budgeting in connection with the discharge of debts,
(b) negotiating with a person’s creditors for the discharge of the person’s debts (in whole or in part), or
(c) any similar activity associated with the discharge of debts”.
Under the Act, a person who meets the definition of a debt management firm is required to obtain authorisation from the Central Bank in order to provide these services. Please also note the Act identifies a number of “excepted persons”.
Please also note that the definition of a debt management firm identifies that it is remunerated for these services. The term “remuneration” is also defined in the Act.
Any person who provides services in relation to debt management should consider, in conjunction with their legal advisors, if their activities fall within the scope of the Act and therefore will require to be authorised by the Central Bank.
Please note that a firm authorised as a debt management firm will not be authorised to hold client funds except where it holds another appropriate authorisation such as an authorisation as a payment institution and / or a money transmission business pursuant to the European Communities (Payment Services) Regulations 2009 or Part V of the Act respectively.
Introduction to Money Transmission Businesses
A Money Transmission Service means a service that involves transmitting money by any means, other than a service -(a) that is a payment service to which the European Communities (Payment Services) Regulations 2009 (S.I. No. 383 of 2009) apply,
(b) that is provided to customers on a basis that is ancillary to any other services apart from debt management services,
(c) that is provided by—
(i) any charitable organisation within the meaning of section 2(1) of the Charities Act 2009,
(ii) the Money Advice and Budgeting Service,
(iii) any licensed bank, building society, credit union or friendly society,
(iv) a barrister, solicitor or accountant who provides money transmission services only in an incidental manner and is subject to regulation by a professional body,
(v) the Insolvency Service of Ireland, any approved intermediary authorised under section 47 of the Personal Insolvency Act 2012 acting as such or any personal insolvency practitioner authorised under Chapter 1 of Part 5 of that Act carrying on practice as such,
(vi) personal representatives (within the meaning of section 3 of the Succession Act 1965),
(vii) trustees of a trust, other than a trust which is established to provide money transmission services,
(viii) the Bank,
(ix) An Post,
(x) the National Asset Management Agency,
(xi) the National Treasury Management Agency,
(xii) the National Consumer Agency, and
(xiii) any other person constituted, or holding office, under an enactment or funded (in whole or in part).
The Central Bank is responsible for the approval of certain charges imposed by a Money Transmission Business in accordance with Section 149A of the Consumer Credit Act, 1995 (as amended) - see www.irishstatutebook.ie. It is also responsible for monitoring the anti-money laundering and prevention of the financing of terrorism measures adopted by Money Transmission Businesses.
Introduction to consumer protection
The Consumer Protection Directorate (CPD) is involved in the development, implementation and supervision on all financial conduct of business regulation for all types of regulated entities. CPD is also responsible for the prudential supervision of certain sectors who are classed as low impact under the PRISM Risk Framework, e.g. Retail Intermediaries, Debt Management Firms, Payment Institutions, Electronic Money Institutions, Bureau de Change, Moneylenders, Retail Credit Servicing Firms and Credit Servicing Firms.The Consumer Protection Directorate aims to deliver on its consumer protection mandate in the context of three important desired consumer protection outcomes:
- a positive consumer-focussed culture that is embedded and demonstrated within all firms;
- a consumer protection framework that is fit for purpose and ensures that consumers’ best interests are protected; and
- regulated firms that are fully compliant with their obligations and are treating their customers, existing and new, in a fair and transparent way.
This framework puts the Consumer at its centre, where the focus of firms must be on delivering positive consumer outcomes within a regulatory framework that is fit for purpose. This can only be achieved where firms have a consumer-focussed Culture which enables consumers to have Confidence in both the financial decisions they are making and the firms they are dealing with.
The Central Bank will continue to Challenge firms, where their focus is not on those consumer outcomes. This includes our gatekeeper role, where applicant firms can expect rigorous and challenging application of the published requirements and standards (including those derived from EU law). There is a need and appetite for appropriate regulatory action where Compliance standards are not being met.
We adopt a risk and evidence-based approach in prioritising our work (including carrying out an annual risk assessment to identify current and emerging risks), which ensures that we are focusing our resources on those areas where we consider there to be a significant threat to our consumer protection objectives. This is in addition to our ongoing engagements with key stakeholders and advice from the Consumer Advisory Group. We monitor compliance with consumer protection requirements through:
Protected Disclosures including Whistleblowing and Infringement Reports
What is a Protected Disclosure (including Whistleblowing and Infringement Reports)?
In summary:Where a worker makes a disclosure under the Protected Disclosures Act, 2014 (the 2014 Act) which they believe is substantially true, or a person in good faith makes a disclosure under the Central Bank (Supervision and Enforcement) Act, 2013 (the 2013 Act), to the Central Bank or to one of its employees or one of its authorised officers; and they have reasonable grounds for believing that the disclosure will show that there has been, is being or is likely to be a breach of, or an offence under, financial services legislation or the concealment or destruction of evidence relating to such an offence or breach; then the disclosure is a “protected disclosure” for the purposes of the legislation.
In broad terms, the protections which accompany a protected disclosure are:
- The confidentiality of the identity of the reporting person making the protected disclosure. This is subject to certain exclusions – for example, where disclosure is necessary for the effective investigation of any matter or is required by law.
- The reporting person making the protected disclosure is protected from civil liability.
- The reporting person making the protected disclosure has a right of action in tort.
- Where the reporting person making the protected disclosure is an employee, their employer may not penalise or threaten penalisation for making the protected disclosure and an employer may be prosecuted for penalising an employee. In addition, employees are protected from dismissal.
- Workers can submit anonymous disclosures to the Central Bank and such disclosures can be treated as a protected disclosure under the 2014 Act. However, where anonymous reports are provided by persons other than “workers”, they fall under the 2013 Act. In those circumstances, an anonymous report is not a “protected disclosure” due to the provisions of the 2013 Act.
- Disclosures made under the 2014 Act do not constitute a criminal offence if, at the time the worker made the disclosure, it was, or they reasonably believed it was, a protected disclosure under the 2014 Act.
Confidentiality
- The Central Bank has a legal obligation to protect the identity of the reporting person who makes a protected disclosure and not to disclose any information that might identify the reporting person, subject to the exceptions outlined below.
- The Central Bank will not inform a regulated financial services firm that a disclosure has been made.
Exceptions
The Central Bank may disclose the identity of the reporting person where the reporting person provides their consent.There are also certain limited circumstances provided for in the legislation, when the Central Bank may, or may be required to (where there is a legal basis for doing so), disclose the reporting person’s identity and/or identifying information. This may arise as follows:
Where the disclosure is made by a worker under the 2014 Act and:
- the Central Bank demonstrates that it took all reasonable steps to avoid disclosing the identifying information; or
- the Central Bank reasonably believes that the reporting person does not object to the disclosure of the identifying information; or
- the Central Bank reasonably believes that the disclosure of the identifying information is necessary for; (a) the effective investigation of the wrongdoing disclosed or; (b) the prevention of serious risk to the security of the state, public health, public safety or the environment or; (c) the prevention of a crime or the prosecution of a criminal offence; or
- the disclosure of the identifying information by the Central Bank was necessary in the public interest or required by law.
- it is necessary to disclose the identity of the reporting person for the effective investigation of the matter to which the protected disclosure relates; or
- it is necessary to disclose the identity of the reporting person for the purposes of one of the following in relation to any matter to which the protected disclosure relates:
- an inquiry under section 33AO or 33AR of the 2013 Act;
- an appeal to IFSAT;
- an assessment under Part 5 of the Market Abuse (Directive 2003/6/EC) Regulations 2005 (now Part 5 of the European Union (Market Abuse) Regulations 2016 - S.I. No. 349 of 2016);
- an assessment under Part 15 of the Prospectus Regulations 2005;
- an assessment under Part 10 of the Transparency Regulations 2007;
- an investigation or hearing under Part 3 of the Central Bank Reform Act 2010.
- In addition to the above exceptions under the 2014 and 2013 Acts, where the disclosure relates to market abuse under the 2016 Regulations, namely insider dealing, unlawful disclosure of inside information and/or market manipulation, the following specific exceptions to the disclosure of a reporting person’s identity or identifying information may also apply in the following circumstances: -
- where it is a necessary and proportionate obligation required by law subject to the appropriate safeguards in the context of investigations or subsequent judicial proceedings or in circumstances where it is necessary to protect the freedom/rights of others, and in particular, the right to a fair trial; or
- where there is an exchange of information between national competent authorities within the European Union, in relation to allegations of market abuse, in particular where such information is necessary for legal proceedings; or
- where information is transmitted to competent authorities in non-EU countries, which will only be done on a case by case basis, provided that the requirements of the Data Protection Acts have been adhered to. Further, it will be on condition that no further transmission of that information will occur without the express written authorisation of the Central Bank and where there has been compliance with the conditions imposed by the Central Bank in relation to the further transmission of the information; or
- in certain circumstances, where information is transmitted to a non-EU country, where a co-operation agreement exists between Ireland and that country.
Procedures
- The Central Bank will acknowledge receipt of the Report to the postal or electronic address indicated by the reporting person.
- The Central Bank may contact the reporting person to clarify the information reported or to request additional information that may be available to the reporting person. This contact will be to the postal or electronic address of the reporting person or by telephone or to the preferred communication channel, if indicated by the reporting person.
- The Central Bank is limited in the feedback it can provide to the reporting person and will only provide feedback where possible.
- Calls to the Protected Disclosures Desk may be recorded.
Protection for Employees
Both the Protected Disclosures Act, 2014 and Part 5 of the Central Bank (Supervision and Enforcement) Act, 2013, provide protections to employees who make protected disclosures. The legislation provides protections and remedies for reporting persons from penalisation and unfair dismissal in relation to their making a protected disclosure.The Workplace Relations Commission and/or the courts will determine whether or not a disclosure is a protected disclosure under the legislation, not the Central Bank. However, it should be noted that the 2014 Act provides that, in such proceedings, all disclosures are presumed to be protected disclosures unless otherwise proven.
The Central Bank cannot intervene in employment disputes and cannot provide legal advice in relation to employee protections under the legislation. If you are considering making a protected disclosure but are unsure of your legal rights, you should contact a lawyer.
Protected Disclosures Act 2014 (Central Bank of Ireland is a prescribed person)
Where a worker wishes to make a report to the Bank under the 2014 Act relating to breaches of financial services legislation by their employer they may make the disclosure through the following channels.
- E-mail: confidential@centralbank.ie
- Telephone: 1890 130014 : Calls are answered Monday to Friday 9.30am - 5.00pm
- Post: Protected Disclosures Desk, Central Bank of Ireland, PO Box 11517, Spencer Dock, Dublin 1, D01 W920.
Pre-Approval Controlled Function (PCF) Disclosures
Persons holding PCF roles in regulated firms who need to make a disclosure of an alleged offence, breach of financial services legislation or concealment or destruction of evidence of such in their firm are requested to make the disclosure by completing the form below and submitting it either by e-mail or post to the addresses provided.Should you call the protected disclosures telephone line out of hours and leave a message including your contact details, we will call you back within one working day to acknowledge receipt of your disclosure.
Should you raise your disclosure via e-mail, you will receive an automatic acknowledgement of receipt and we will make further contact with you thereafter, if the need arises. Should you submit your disclosure by post, you will receive a written acknowledgement within three working days of receipt (if you include your return postal address).
- E-mail: Protecteddisclosures@centralbank.ie
- Telephone: 1890 130015 (for general queries only); Calls are answered Monday to Friday 9.30am - 5.00pm
- Post: PCF Disclosure Desk, Central Bank of Ireland, PO Box 11517, Spencer Dock, Dublin 1, D01 W920.
Central Bank (Supervision & Enforcement) Act, 2013
Where a person wishes to disclose to the Central Bank an alleged offence, breach of financial services legislation or concealment or destruction of evidence of such, under the Central Bank (Supervision & Enforcement) Act 2013 they may make the disclosure through the following channels.- E-mail: confidential@centralbank.ie
- Telephone: 1890 130014: Calls are answered Monday to Friday 9.30am - 5.00pm
- Post : Protected Disclosures Desk, Central Bank of Ireland, PO Box 11517, Spencer Dock, Dublin 1, D01 W920.
European Union (Market Abuse) Regulations 2016
Where a person wishes to report an actual or potential infringement under the 2016 Regulations they may make the Report through the following channels.- E-mail: confidential@centralbank.ie (please refer to MAR infringement in email)
- Telephone: 1890 130014: Calls are answered Monday to Friday 9.30am - 5.00pm
- Post: MAR Disclosures Desk, Central Bank of Ireland, PO Box 11517, Spencer Dock, Dublin 1, D01 W920.
A person making a Report to the Central Bank can also seek to have a meeting with dedicated staff members of the Central Bank.
Overview of the Legislation
Please note that the Central Bank cannot give you legal advice if you are thinking about making a disclosure. You should contact a lawyer if you are unsure of your position.Part 5 of the Central Bank (Supervision and Enforcement) Act 2013
The Act came into force on 1 August 2013. This introduced new protections for persons making protected disclosures to the Central Bank as well as new obligations on certain categories of persons in firms to disclose breaches of financial services legislation to the Central Bank.Obligation on PCFs to report breaches of financial services legislation (S. 38 (2) Disclosures)
A person appointed to perform a pre-approval controlled function (“PCF”) is required under Section 38 of the 2013 Act, to disclose to the Central Bank information relating to a breach of, or offence under, financial services legislation or the concealment or destruction of evidence relating to such an offence or breach, which he or she believes will be of material assistance to the Central Bank.Protected Disclosures Acts 2014
A worker can make a report to the Bank under the 2014 Act relating to breaches of financial services legislation which they learned about in connection with their employment, as the Bank is a prescribed person by virtue of S.I. No. 339/2014 Protected Disclosures Act 2014 (Section 7(2)) Order 2014.ECB/Single Supervisory Mechanism Regulation
The EU SSM Regulation establishing the Single Supervisory Mechanism (SSM), which formally commenced on 4 November 2014, includes a provision in respect of reporting of breaches, i.e. whistleblower reports: Article 23. Under the Regulation, persons with information on potential breaches of relevant EU law by banks and/or by competent authorities, including the Central Bank, can report such breaches to the ECB.Reports received by the Central Bank in respect of the significant supervised entities, i.e., major Banks in Ireland, and in respect of prudential issues, must be submitted to the ECB by the Central Bank for processing, in accordance with the SSM Regulation. Reports in respect of less significant supervised entities, where the report is in respect of an alleged breach of an ECB decision or regulation or where the report is in respect of the Central Bank, will also need to be submitted to the ECB. Where such reports are in respect of breaches of the Central Bank's code of conduct or anti-money laundering these are not sent to the ECB but are assessed by the Central Bank.
Market Abuse - European Union (Market Abuse) Regulations 2016 (S.I. No.349 of 2016)
The 2016 Regulations impose obligations on the Central Bank to have appropriate structures and processes in place to receive reports of actual or potential infringements of market abuse law. The SI does not create a separate type of protected disclosure in respect of infringements of market abuse law, but sits with existing protections for persons making protected disclosures under the 2013 and 2014 Acts.Where a reporting person makes information available to the Central Bank in accordance with the 2016 Regulations, they are not considered to be: -
- infringing any restriction on disclosure of information imposed by contract or by any legislative, regulatory or administrative provision; or
- involved in liability of any kind related to such disclosure.
Introduction to Enforcement
A successful regulatory model is composed of a number of interlocking components, namely regulation (the rules), on-going supervision and enforcement. All components must interact with each other to ensure effective financial system governance.- Regulation: Legislative Rules, Codes, Standards Underpinning Supervision and Enforcement
- Supervision: Risk-Based, Assertive Inspection and Supervision of Regulated Entities
- Enforcement: Gatekeeping, Investigation and Enforcement Regime and Administrative Sanctions
The Enforcement division liaises closely with the Central Bank’s supervisory divisions and advises on appropriate outcomes such as consumer redress schemes and takes necessary measures, including enforcement action, where required.
The Enforcement division is comprised of several multi-disciplinary teams and adopts an intrusive approach to investigations, placing an emphasis on pursuing individual accountability, routinely undertaking data mining and conducting forensic interviews as part of the investigative process.
Enforcement deals with issues identified, amongst other things, during the normal course of work undertaken by a supervisory division or as a result of an on-site inspection at a regulated firm or a themed inspection across a particular sector.
Single Supervisory Mechanism (SSM)
Since 4 November 2014, the European Central Bank (the “ECB”) has directly supervised significant credit institutions within Ireland. As a result, the ECB can take direct enforcement and sanctions proceedings against significant institutions. The ECB can also instruct the Central Bank to use its supervisory powers or to open proceedings against significant institutions operating in Ireland.Enforcement Tools
Enforcement uses a wide range of tools to take action against regulated entities and/or individuals which fall short of our expected standards of behaviour including:- Administrative sanctions (under Part IIIC of the Central Bank Act 1942, and separately under Securities and Markets Regulations)
- Fitness and Probity investigations
- Refusals and revocation of authorisations
- Cancellation and refusal of registrations
- Summary criminal prosecution
- Supervisory Warning
- Imposition of a condition
- Issuance of a direction
- Reports to other agencies (including Gardaí, Revenue Commissioners, The Competition and Consumer Protection Commission).
Enforcement Outcomes
Funds collected from monetary penalties imposed under the Central Bank’s Administrative Sanctions regime are included in the Central Bank’s surplus income which is payable directly to the Exchequer.In accordance with the Central Bank’s principles of working with integrity and transparency, public statements are issued at the conclusion of enforcement actions. These statements also serve to inform and advise the financial sector and consumers of expected standards and behaviours.
The public notices regarding Settlement Agreements (concluded pursuant to Part IIIC of the Central Bank Act 1942) can be found on our Public Statements page.
Disqualification Notices, Suspension Notices and Prohibition Notices can be found on our Prohibition Notices page.
Enforcement also works with supervisory divisions and regulated entities to put in place redress schemes to compensate consumers for loss suffered as a result of the actions of such entities.
Resolution framework
On 15 May 2014, the Bank Recovery and Resolution Directive (BRRD) was adopted by the EU in order to provide national resolution authorities with comprehensive and effective powers for dealing with failing banks. This framework and related legislation enhances both the resilience and the resolvability of EU institutions and in-scope investment firms, which will be better prepared to deal with, and recover from, a crisis situation. Moreover, in the event that an institution does fail, the impact associated with that failure should be minimised.Specifically, the framework brings about the following changes:
- Credit institutions and in-scope investment firms are required to prepare recovery plans, which identify appropriate options that can be executed in the event of a significant financial deterioration of the institution, thereby reducing the likelihood of failure.
- In addition, the BRRD grants a new set of early intervention powers to supervisors. These powers include the requirement for institutions to execute recovery options, the removal of management and changing the structure of the institution.
- Resolution planning activity is undertaken by the Central Bank, or the SBR, in advance of failure to unsure this process is managed effectively.
- If required, the Central Bank and the SRB have at their disposal a set of resolution tools that can be used to resolve failing institutions in order to minimise the impact of failure on the financial system, the real economy, depositors and taxpayers.
- Both a national and a European resolution fund have been established to help finance the cost of resolution in the future.
Industry & Market Sectors
- Brokers / Retail Intermediaries
- Bureaux de Change
- Credit Institutions
- Credit Servicing Firms
- Credit Unions
- Debt Management Firms
- Electronic Money Institutions
- Funds
- Funds Service Providers
- Insurance & Reinsurance
- Investment Firms
- Moneylenders
- Money Transmission Businesses
- Payment Institutions
- Retail Credit & Home Reversion Firms
- Securities Markets
Unauthorised Firms
Register of Authorised Firms
All firms which hold an authorisation from the Central Bank of Ireland (‘Central Bank’), or where applicable, the SSM, to provide financial services in Ireland are listed in our Registers section. Prior to entering into a financial services transaction, members of the public can check the regulatory status of the firm they are dealing with.Please note that some firms based in the European Economic Area may be regulated in their Home State and may be authorised to provide services in Ireland under Passporting arrangements.
Consequences of Dealing with Unauthorised Firms
You should be aware that if you deal with unregulated firms you will not have access to the following protections:- Investor compensation schemes
- The services of the Financial Services Ombudsman
- The Directors and senior management of unregulated firms are not subject to the Fitness and Probity Regime
- Unregulated firms are not subject to prudential requirements such as regulatory capital requirements or safeguarding of client funds
Unauthorised Investment Firms and Warning Notices
- Under the Central Bank (Supervision and Enforcement) Act 2013, the Central Bank has the authority to publish warning notices naming persons or firms who are providing financial services without the appropriate authorisation or who are holding themselves out to be a regulated financial service provider where they do not have the appropriate authorisation to provide financial services.
- The Central Bank also publishes a list of unauthorised firms in respect of whom warning notices have been published.
Checking an Authorisation
The Central Bank publishes Registers of all the firms and individuals authorised by us on our website. You can use the search function to check whether or not a provider is authorised.Tips on Using the Registers
- Under European law, some firms may be allowed to operate in Ireland without being authorised by us. Such firms are regulated by their home state, although the Central Bank of Ireland is responsible for some regulation in the Consumer Protection area (known as conduct of business rules) such as advertising. These firms may not appear on the Registers, so if in doubt please contact us using the details below to confirm their status. You can also check on the firm's website, which should indicate which country regulates them, and search for them in that country's equivalent of the Registers.
- Many firms using one or more trading names in addition to their legal name (you may recall hearing ads on the radio saying 'X trading as Y is regulated by the Central Bank of Ireland). If the trading name does not appear, try searching for their legal name, which should be indicated on their website and literature.
- Try using fewer keywords if you do not get a hit the first time around- perhaps search for the first word in the firm's name.
- Some larger providers might operate using a number of companies, each with a different class of authorisation. Make sure you search for the correct name, which should be clearly indicated on the relevant literature and the website.
- Bear in mind that not all financial service providers require regulation by the Central Bank. Examples of financial service providers that do not presently require authorisation by us are:
- online betting and gaming websites
- debt collectors
- loss adjustors i.e. individuals/firms that are employed by the insurance company and not the consumer
- financial education companies
Financial Stability
The Central Bank of Ireland aims to identify, assess, communicate, propose actions and take actions to remove or reduce financial and economic risks in order to enhance the resilience of the financial system of Ireland and the euro areaXXX . V0000000000 High Performance Digitizers - Data Acquisition Products
Digitizers from Teledyne SP Devices are ideal for demanding measurement applications, and many of the products utilize SP Devices’ patented ADX technology in order to achieve an unique and unrivaled combination of high sampling rate and high vertical resolution. The products are available in a number of different form factors and supports multiple operating systems. Custom real-time signal processing can be added to the powerful on-board FPGAs through an optional firmware development kit, and the deep on-board memory in combination with advanced triggering and flexible data acquisition modes makes the digitizers versatile and suitable for a wide range of applications.
Hardware
Software
Overview
Our digitizers are delivered with an extensive set of software, documentation and examples that makes it easy to get started. The software development kit (SDK) is included free of charge when purchasing a digitizer and contains a number of tools which are described more in detail below. Software included in our optional firmware packages is also described below.Software Development Kit
The software development kit (SDK) is available for Windows and Linux operating systems (click here for a complete list of supported OS versions). Click the links below to learn more about individual software components:- Device drivers
- Application programming interface (API) library, header files, and a programmer's reference guide in which all functions/methods are described in great detail
- LabVIEW™ drivers including GUI example for ADQ7 and ADQ14
- Application notes and user guides
- Example code for controlling the digitizers via the API in C, C++, Python, Matlab, Visual Basic and LabVIEW™
- Software utilities for upgrading digitizer firmware and for installing new firmware package licenses
- ADCaptureLab, a GUI-based demo application (Windows only)
Additional Software
Our optional firmware packages offers a rich set of functions commonly used in specific applications. These functions are implemented inside the FPGA and therefore allows for signal processing in real-time. One of the primary benefits of this approach is that data reduction can be achieved and this helps lower the CPU load on the host PC plus it relaxes requirements on write speed and total storage capacity required for disk streaming solutions. Most of the firmware packages comes with an easy-to-use GUI:Overview
Field-Programmable Gate Arrays (FPGAs) are an ideal fit for data acquisition systems as they offer unparalleled real-time signal processing power. Moving functionality from the host PC to the on-board FPGAs helps offload the PCs central processing unit (CPU) and relaxes data transfer rate requirements. This capability is key in achieving the performance levels needed in many of today's leading-edge applications.All our data acquisition and generation modules host Xilinx FPGAs and are delivered with pre-installed general data acquisition firmware (for ADQ7 and ADQ14 we refer to this firmware as "FWDAQ"). In addition to the standard/default firmware we also offer optional firmware development kits (available for all models) and application-specific firmware packages (available for ADQ7 and ADQ14 only). More information about these below.
Firmware Development Kit
The optional firmware development kit opens up the FPGA to the user so that custom firmware can be integrated together with the pre-defined standard/default firmware inside the FPGA. The kit is based on the Xilinx development tool suite and access to these tools is hence a prerequisite. Learn more by clicking the link below:Optional Firmware Packages
The optional firmware packages extend the functionality provided by the standard/default firmware by offering a rich set of pre-compiled additional functions commonly used in different application areas and measurement scenarios. Click the links below to learn more about each individual package:Mass spectrometry is a large group of methods for analyzing the compounds of a substance. The ADQ series of digitizer is carefully designed for any Time-of-flight based method for Mass Spectrometry.
Optimizing ADQ digitizer for Mass Spectrometry
A high quality MS TOF measures a large span in concentration of substances and accurate resolution of different masses. This implies that the digitizer must have the combination of high dynamic range and high sample rate. SP Devices’ ADQ-series of digitizers are designed to provide the best combination of these parameters. The high resolution is achieved by 14 bit digitizers and application specific firmware for noise suppression. The high sample rate is achieved by interleaving of A/D converters. To maintain high signal quality when interleaving ADCs, the digitizers are empowered by SP Devices’ interleaving technologies ADX and DBS.Mass resolution through high sample rate
The mass resolution is set by the bandwidth of the detector, that is, how narrow peaks can be generated. Today a typical peak is in the range of a nanosecond. This implies that the digitizer has to provide several GSPS (sample at several GHz) to capture these pulses. The ADQ14 series of digitizers provides 14 bit resolution of up to 2 GSPS. The application note shows how to get 14 bits at 4 GSPS from the ADQ14.Mass concentration through high dynamic range
Although the 14 bits resolution of the ADQ14 is very high, it has to be enhanced many times to meet the requirements of a mass spectrometer. This is done by averaging a large number of repeated measurements. This process produce a huge amount of data. To build an efficient system an averaging function built into the firmware of the ADQ14-FWATD. The output is then only the accumulated result from very many measurements. With the waveform averaging function the dynamic range can reach to about 100 000 : 1.Efficient processing of low activity methods
Some mass spectrometry instruments has a very low activity. Then the acquired data contains a lot of zeros. To optimize the data flow to the PC, the firmware option ADQ14-FWPD can detect and analyze pulses directly in the FPGA. The zero data is suppressed and only requested information about a pulse is transmitted to the PC for further analysis.Extended dynamic range through dual channels
A traditional method for enhancing performance when digitizers were operating at 8 bits resolution was to use 2 channels and apply the same signal, but with different gain. In this way, the ratio between the largest and the smallest signal was increased. The same method can be applied on the 14 bits digitizer ADQ14DC-2X , which provide 2 synchronized channels at 2 GSPS each.Thomson Scattering
"The combination of 14 bits dynamic range and 1 GS/s sampling rate is taking the performance of digitizers for TS system to an unprecedented performance level compared to the normally used 10 or 12 bit ADC.[1]"Thomson scattering is one of the most important diagnostic at the moment to study plasma. It is used in, for example, stellarator and tokamak fusion experiments. The short description of the method is:
A laser beam is sent into the plasma. The laser beam is scattered on the electrons and the Doppler effect will result in a color shift. This indicates the temperature. The intensity of the scattering indicates the density of the plasma.
Recommended Products
The ADQ14DC-4C is perfect for the Thomson scattering measurement. The ADQ14 is a unique combination of high bandwidth and high resolution which is required by the Thomson scattering application.Benefits
- The dynamic range requirements are high, which is met by 14 bits resolution of ADQ14.
- The bandwidth requirements of the experiment is above 300MHz, which is met by the 700 MHz bandwidth of the ADQ14.
- The bandwidth imply that the sample rate has to at least 1 GSPS, and ADQ14 offer 1 GSPS or 2 GSPS.
- The channel count is often high, and ADQ14-4C provide 4 high speed channels per card which gives a dense system.
- The high channel count also implies rack assembly, and ADQ14 is available for both MTCA.4 and PXIe chassis.
- The timing synchronization capabilities is a chassis is making the ADQ14 solution unique.
Optical Coherence Tomography
The non-invasive SS-OCT uses light waves to obtain three-dimensional images on a micron scale. This technology provides cross-sectional images of tissue structures which provides a valuable instrument in research and diagnostic medicine.Recommended Product
The ADQ14OCT is configured to support variable clocking from the most advanced lasers and supports a laser trig rate of up to 1000 MHz to help produce the most detailed images in a very short time. ADQ14OCT is factory-programmed with signal processing typically used in SS-OCT applications, providing real-time FFTs up to 32768 bins, logarithm computations, and multiple configuration options to simplify integration into SS-OCT equipment. ADQ14OCT is available with USB3.0, PCIe, and PXIe interfaces.
Imaging is performed through OCT when the interference pattern signals are produced by different scans of wavelength when reflected at different depths using low coherence interferometry.
Fourier-Domain OCT calculates the depth dependent reflection profiles. Continuously performing this A-scan at different locations creates a two dimensional cross section.
LiDAR
LiDAR
When LiDAR (Light Detection And Ranging) is used for mapping the shore line it is necessary to measure above and below the water level. This technique is used for monitoring meandering rivers and studying flood risk and erosion of the coast line. These environments have different requirements on a LiDAR system. An infrared laser is used for land and a green laser to penetrate the water (topo-bathymetric LiDAR). In good conditions, a depth of up to 50 meters can be monitored. This LiDAR application puts several requirements on the digitizer including high resolution amplitude capability (a Time to Digital Converter (TDC) is not enough) and high channel count to accommodate certain laser requirements.Recommended Products
SP Devices’ offers several models suitable for LIDAR applications:- ADQ14DC-4C offers 4 channels at 1 GSPS with 14 bits resolution. The high vertical resolution allows for accurate images during underwater surveys. The four channels are available for multiple detectors connected to lasers with different wavelengths. The ADQ14 also allows for high throughput to the PC for fast scanning capabilities. Input impedance matching is also important, especially in an over voltage condition. The signals are strong and the over voltage protection circuitry often acts as a non-linear current sink. To avoid the non-linear condition and resulting large reflections during over voltage, the first stage of the ADQ14DC is linear and resistive. This means that there is an attenuation of reflections even in an over voltage scenario.
- ADQ412-4G also offers 4 channels, but at 2 GSPS per channel and with 12 bits vertical resolution.
Tech Corner
Time‑interleaving of analog‑to‑digital converters (ADCs) is a way to increase the overall system sample rate by using several ADCs in parallel. The challenge is to handle the mismatch between the individual ADCs, especially at higher frequencies.

Higher speed
The SP Devices interleaving technology provides our customers with a method of increasing the sampling rates of their A/D solutions. The interleaving process involves the signal being sampled at different times by one of a number of parallel ADCs. The overall sampling rate is in this way multiplied by the number of ADCs.
XXX . V0000000000 Clocking
Clocking
The ADQ series of digitizers has an advanced clock system for flexible synchronization to external
equipment. This document is a general description of the clock system. It also contains examples on
how to use the clock system.
1 Introduction
The ADQ series of digitizers has clock reference and internal clock source as well as a connector
for direct external clock. The intention with the clock design is to synchronize several
different hardware units. The clocking system has a lot of flexibility. It also has a lot of limitations.
The application note intend to give understanding on how the clocking works and why
there are limitations.
A typical situation where this application note is useful is when the signal source has a clock
reference and the digitizer should be synchronized to that source. Many instruments use
10 MHz. Then it is straight forward. However, for other reference frequencies, the clock network
has to be controlled in several nodes, which are described here.
XXX . V0000000000 The international monetary and financial system
The suitable design of international monetary and financial arrangements for the global economy is a long-standing issue. A key shortcoming of the existing system is that it tends to heighten the risk of financial imbalances, leading to booms and busts in credit and asset prices with serious macroeconomic consequences. These imbalances often occur simultaneously across countries, deriving strength from international spillovers of various types. The global use of the dollar and the euro allows monetary conditions to affect borrowers well beyond the respective issuing economies. Many countries also import monetary conditions when setting policy rates to limit interest rate differentials and exchange rate movements against the major currencies. The global integration of financial markets tends to reinforce these dynamics, by allowing common factors to drive capital flows and a common price of risk to move bond and equity prices. Policies to keep one's own house in order by managing financial cycles would help to reduce such spillovers. In addition, central banks need to better internalise spillovers, not least to avoid the effects of their actions spilling back into their own economies. Moving beyond enlightened self-interest would require international cooperation on rules constraining domestic policies.
Just as in the past, however, there is little agreement on what the key shortcomings of the current international monetary and financial system (IMFS) are, let alone on what to do about them. A common diagnosis has been that the system is unable to prevent the build-up of unsustainable current account imbalances and that this, in turn, has induced a contractionary bias: surplus countries have no incentive to adjust, while deficit countries are forced to do so. Indeed, current account imbalances have been a focus of G20 cooperative efforts.
This chapter provides a different perspective, by arguing that the main shortcoming of existing arrangements is that they tend to compound the weaknesses of domestic monetary and financial frameworks ("regimes"). In particular, the IMFS tends to heighten the risk of financial imbalances - that is, unsustainable credit and asset price booms that overstretch balance sheets and can lead to financial crises and serious macroeconomic damage. These imbalances occur simultaneously across countries, deriving strength from global monetary ease and cross-border financing. Put differently, the system exhibits "excess financial elasticity": think of an elastic band that can be stretched out further but that, as a result, eventually snaps back all the more violently.1
The chapter is structured as follows. After outlining the key features of the IMFS, the first section explains and documents how the interaction of domestic monetary and financial regimes increases financial imbalances. It highlights several factors: (i) the role of monetary areas that for the key international currencies (notably the US dollar) extend well beyond national borders; (ii) the limited insulation properties of exchange rates, which induce policy responses designed to avoid large interest rate differentials vis-à-vis the main international currencies; and (iii) the powerful waves generated by freely mobile financial capital and global liquidity, which wash across currencies and borders, carrying financial conditions across the globe. The second section considers possible solutions. It highlights the need to adjust domestic policy frameworks and to strengthen international cooperation, going beyond the own-house-in-order doctrine.
The IMFS: main elements and weaknesses
Main elements
The IMFS comprises the arrangements governing transactions in goods, services and financial instruments among countries. Today, it consists of a set of domestically oriented policies in a world of largely free capital flows. Domestic monetary regimes focus mainly on price stability, while currencies are allowed to float to varying degrees: free floating among the principal international currencies coexists with greater or lesser management of other currencies. Financial regimes generally allow funds to move freely across currencies and borders, although some countries still impose restrictions. The main restraint on financial transactions takes the form of prudential regulation and supervision, in part based on internationally agreed standards.Current arrangements differ markedly from the previous system, Bretton Woods (1946-73). At the time, the US dollar's convertibility into gold served as an external monetary anchor, and currencies were tied together through fixed but adjustable exchange rates (Table V.1). Domestic monetary regimes in general gave less priority to price stability and more to external balance and demand growth. While the anchor ultimately did not prove that strong, the arrangements contrast with present ones, in which the aggregation of monetary policies pursued under domestic mandates acts as the only overall constraint. During the Bretton Woods era, the leading international currency was the dollar, which now shares this role to some extent with others, mainly the euro. And international capital mobility was quite limited, reflecting a myriad of restrictions on "repressed" domestic financial systems.
The performance of the two systems has differed markedly as well. Bretton Woods did not see major episodes of financial instability, but eventually proved unable to ensure lasting global monetary stability. It broke down once the United States formally abandoned gold convertibility and exchange rates were allowed to float. Current arrangements have succeeded in promoting price stability more than financial stability.
Arguably, this is no coincidence. The 84th Annual Report, as further elaborated in other chapters of this Annual Report, explored why domestic monetary and financial regimes have so far been unable to ensure lasting financial stability. But their interaction through the IMFS has also played a role, by compounding rather than limiting the weaknesses of domestic regimes. Consider, in turn, the interaction of monetary and financial arrangements.
Interaction of domestic monetary regimes
The interaction of monetary regimes spreads easy monetary conditions from core economies to the rest of the world. The international use of reserve currencies does so directly, and the strategic conduct of monetary policy does so indirectly. Take each in turn.The reliance on a single global currency has diminished slowly since Bretton Woods, but the US dollar continues to play a dominant role in international trade and finance, alongside the euro. As a means of exchange, the dollar is on one side of no less than 87% of foreign exchange market transactions (Table V.2), with an even higher share of forward and swap transactions. Its dominance in foreign exchange markets makes the dollar the sole intervention currency outside Europe and Japan, which supports its high share in foreign exchange reserves. More than half of world trade is invoiced and settled in dollars, pointing to the greenback's pre-eminent role as a unit of account.
Remarkably, the advent of the euro and the dollar's trend depreciation since the 1970s have not materially challenged the dollar's role as a store of value (Graph V.1, left-hand panel). At 63%, it maintains almost three times the share of the euro in foreign exchange reserves. Its share in both official reserves and private portfolios is sustained by the scale of what can be termed the "dollar zone" of economies whose currencies move more closely with the dollar than with the euro (Box V.A). At half or more of world GDP, the dollar zone is far larger than the US economy, which is less than a quarter.
Monetary policy settings for key international currencies influence financial conditions outside these currencies' home jurisdictions directly through their impact on interest rates and the valuation of assets or liabilities denominated in these currencies but held or owed by non-residents. In particular, dollar and euro credit to non-bank borrowers outside the United States and euro area stood at $9.5 trillion and €2.3 trillion ($2.7 trillion), respectively, at end-2014. The dollar debt represents a seventh of global GDP outside the United States (Box V.B).
The large stocks of dollar- and euro-denominated credit extended to borrowers outside the United States and the euro area, respectively, mean that Federal Reserve and ECB policies are transmitted directly to other economies. The impact depends on the characteristics of the instrument in question, notably its maturity and the flexibility of the corresponding interest rate. For instance, in the case of bank loans priced off of dollar Libor or Euribor, changes in short-term policy rates pass through within weeks. Over half of dollar and euro credit to borrowers outside the United States and euro area remains in the form of bank loans.
The pass-through is slower for bonds, given their generally fixed rates and longer maturity, but then quantities can respond too. In particular, some stocks of dollar bonds have changed quite markedly in response to unconventional monetary policy (Chapter IV). Low yields reflecting the Federal Reserve's large-scale purchases of Treasury and agency bonds, among other factors, led US and global investors to seek yield in lower-quality bonds. The impact was especially pronounced for non-US borrowers, who between 2009 and 2014 ramped up their dollar bond issuance by $1.8 trillion (Graph V.2, left-hand panel). Investor demand for such bonds proved highly responsive to the compression of the term premium, as measured by the spread between Treasury bond yields and expected bill yields: the lower the premium, the faster the growth of dollar bonds issued by non-US borrowers (hence the negative relationship after the first quarter of 2009 seen in the right-hand panel of Graph V.2).
By the same token, the recent ECB large-scale bond purchases and compression of term premia on euro-denominated bonds raise the question of whether borrowers outside the euro area will take advantage of the funding opportunity. In fact, by the end of 2014 the stock of euro bonds issued by such borrowers was already growing as fast as its dollar counterpart.
Post-crisis, offshore dollar credit has grown fastest in those jurisdictions where it has been cheapest relative to local funding, especially emerging market economies (EMEs).2 Authorities around the world use capital controls or macroprudential policy to raise the cost of dollar borrowing at home, but their policy reach does not extend to activities of multinational firms, which can borrow dollars (or euros) offshore to sidestep tight domestic funding conditions. This is one reason for the rapid growth in various quantitative measures of "global liquidity", which denotes the ease of financing in global financial markets (Box V.B).
Box V.A
Mapping the dollar and euro zones
This box uses simple regression methods to place currencies in three zones of influence corresponding to the main international currencies based on the currencies' degree of co-movement. The three reference currencies are the dollar, the euro (before 1999, the Deutsche mark) and the yen, consistent with their status as the three most transacted currencies in the world in the BIS Triennial Central Bank Survey. Thus defined, the dollar zone accounts for nearly 60% of world GDP, far more than the US share in world GDP, which is between 20 and 25%.
The dollar share is calculated in two steps. First, each currency is placed in or between zones. Each currency's weekly percentage change against the dollar is regressed on the weekly percentage change of the euro/dollar and yen/dollar rates. The dollar zone weight is calculated as 1 minus the corresponding regression coefficients. For example, the Hong Kong dollar is pegged to the US dollar, so the coefficients are zero and the dollar zone weight is 1. For the intermediate case of sterling, in 2013 the pound's estimated coefficient is 0.60 on the euro/dollar rate and 0.09 on the yen/dollar, making the currency's dollar weight 1 - 0.60 - 0.09, or 0.31. The results in Graph V.A show the dollar to be more global, the euro to be more regional and the yen to lack much external influence. The dollar weights can thus be read in reverse as euro weights, eg with the dark blue area representing over 95% euro weight.
Second, the dollar share is calculated across currencies using (PPP) GDP weights. The dollar zone weight for each of the 40 economies (50 before the euro) is multiplied by the respective GDP, and the product is added to the US GDP. This sum is then expressed as a share of the total GDP of the 43 major economies analysed, including those of the United States, the euro area and Japan. Graph V.1 plots these aggregate zone shares of global GDP.
There is strong cross-sectional evidence that a currency's co-movement with the dollar shapes the currency composition of its external portfolio, both official and private. For the two dozen economies that disclose the currency composition of official reserves, the dollar zone weight accounts for about two thirds of the variation in the dollar share across countries. And in larger samples, the dollar zone weight is also strongly linked with the dollar share of cross-border bank deposits or loans and international bonds. The underlying motivation is the same for the official and private sectors: matching the portfolio weights to the co-movements of the domestic currency with major currencies serves to minimise the volatility of portfolio returns when measured in domestic currency.
And in larger samples, the dollar zone weight is also strongly linked with the dollar share of cross-border bank deposits or loans and international bonds. The underlying motivation is the same for the official and private sectors: matching the portfolio weights to the co-movements of the domestic currency with major currencies serves to minimise the volatility of portfolio returns when measured in domestic currency.
 And in larger samples, the dollar zone weight is also strongly linked with the dollar share of cross-border bank deposits or loans and international bonds. The underlying motivation is the same for the official and private sectors: matching the portfolio weights to the co-movements of the domestic currency with major currencies serves to minimise the volatility of portfolio returns when measured in domestic currency.
And in larger samples, the dollar zone weight is also strongly linked with the dollar share of cross-border bank deposits or loans and international bonds. The underlying motivation is the same for the official and private sectors: matching the portfolio weights to the co-movements of the domestic currency with major currencies serves to minimise the volatility of portfolio returns when measured in domestic currency. See R McCauley and T Chan, "Currency movements drive reserve composition", BIS Quarterly Review, December 2014, pp 23-36.
See R McCauley and T Chan, "Currency movements drive reserve composition", BIS Quarterly Review, December 2014, pp 23-36.One reason is to limit exchange rate movements. Exchange rate flexibility has often been described as insulating the domestic economy from external developments, but this insulation is often overstated. In particular, appreciation can lead lenders to consider firms with debts denominated in foreign currency as better capitalised and therefore more creditworthy, reducing perceived risks associated with lending and increasing the availability of credit.3 Through this and other mechanisms, such as carry trades and momentum trading, currencies can overshoot, shrinking the traded goods sector and leaving the economy vulnerable to a turn in the ease of global financing. Then, depreciation can lead to financial distress among firms with foreign currency debt. During the dollar's downswing from 2002 to 2011 (with an interruption in late 2008), many central banks resisted unwelcome appreciation against the dollar, in setting their own policy rates and by intervening in the currency market.
Indeed, many countries - not only EMEs but also advanced economies - appear to have kept interest rates below those that traditional domestic benchmarks would indicate, partly in response to low rates in core currencies. In the 1990s, policy rates were broadly in line with the Taylor rule, a simple interest rate rule prescribing a mechanical reaction to the output gap and the deviation of inflation from target. In the early 2000s, however, actual policy rates drifted persistently below the levels implied by the Taylor rule, suggesting that monetary policy became systematically accommodative (Graph V.3). Many advanced economies apparently hesitated to raise interest rates during the boom, and have maintained them near zero since the crisis. For their part, EME authorities appear to have set policy rates low out of concern over capital flows and appreciation (Graph V.3, right-hand panel). The empirical significance of US interest rates in influencing policy rates elsewhere provides additional evidence for follow-the-leader behaviour (Box V.C). While this simple exercise has important limitations, it points to competitive easing as a way of sustaining external demand. More than 20 central banks have eased monetary policy since December 2014, some explicitly responding to external conditions (Chapter IV).
Box V.B
Global liquidity as global credit aggregates
Over the past several years, the BIS has developed indicators to track global liquidity conditions. The term global liquidity is used to mean the ease of financing in global financial markets. Total credit outstanding is one of its main footprints, as it shows the extent to which bond markets and banks have led to the build-up of exposures. In covering US dollar and euro credit, this box focuses on the two largest components of global credit through which the monetary policies of the respective currency areas directly influence financial conditions in the rest of the world.
In covering US dollar and euro credit, this box focuses on the two largest components of global credit through which the monetary policies of the respective currency areas directly influence financial conditions in the rest of the world.
 In covering US dollar and euro credit, this box focuses on the two largest components of global credit through which the monetary policies of the respective currency areas directly influence financial conditions in the rest of the world.
In covering US dollar and euro credit, this box focuses on the two largest components of global credit through which the monetary policies of the respective currency areas directly influence financial conditions in the rest of the world.
Global credit can be extended through bank loans or bonds, and each has a domestic and an international component. Graph V.B shows dollar- and euro-denominated debt, broken down by the location of the borrower. Some 80% of global non-financial dollar debt at end-2014 was incurred by US residents (top left-hand panel). Their liabilities include US public debt, US household debt and US corporate debt. But $9.5 trillion (19%) of dollar credit was extended to non-bank borrowers located outside the United States, and these entities are as exposed to the US monetary policy stance as US residents are. At 13% of non-US GDP, the stock of offshore dollar credit exceeds its euro counterpart worth $2.7 trillion (bottom left-hand panel). Compared with borrowing in US dollars, a larger share of overall borrowing in euros takes place from inside the same currency area (92%).
The international credit component tends to be more procyclical and volatile. International bank lending in both dollars and euros outpaced domestic credit in the boom that preceded the Great Financial Crisis, and contracted once the crisis broke out (Graph V.B, right-hand panels). Bond markets partly substituted for impaired bank lending in the immediate aftermath of the crisis, and increased demand for funding went hand in hand with higher yield spreads. Since 2010, the search for yield has enabled a surge in issuance at compressed spreads that has helped to push the share of bonds in international credit to 46%. In this second phase of global liquidity, bond markets and the asset management industry have taken centre stage in shaping global liquidity conditions.
 See BIS, "Highlights of global financing flows", BIS Quarterly Review, March 2015, pp 13-29; and www.bis.org/statistics/gli.htm.
See BIS, "Highlights of global financing flows", BIS Quarterly Review, March 2015, pp 13-29; and www.bis.org/statistics/gli.htm.As a result, monetary policies of advanced and emerging market economies have reinforced each other. Easy monetary conditions at the centre have led to easy monetary and financial conditions in the rest of the world: there, firms and governments have boosted dollar and euro borrowing and authorities have resisted unwelcome currency appreciation. In turn, their foreign exchange intervention has raised official investment in major bond markets, further compressing bond yields there. With central banks and reserve managers bidding for duration shoulder to shoulder with pension funds and life insurers, bond yields have declined to record lows and the term premium has turned negative (Chapter II).
Interaction of financial regimes
Financial market integration has allowed common global factors to drive capital flows and asset prices. The common factors have partly shifted between the two phases of global liquidity, pre- and post-crisis.
Box V.C
International monetary spillovers
Over recent years, interest rates in EMEs and advanced economies moved closely together with interest rates in large advanced economies, particularly the United States. This close correlation could reflect the response to common macroeconomic developments affecting all countries. But it could also reflect global interest rate spillovers from large advanced economies. Interest rate spillovers can result from explicit exchange rate policies or attempts to contain exchange rate and capital flow pressures resulting from yield differentials vis-à-vis key currencies, and from global investor arbitrage tying capital market rates together.
To shed light on this question, a panel of 30 emerging market and advanced economies over the period 2000-14 is investigated in a regression analysis. The analysis shows a strong relationship between changes in interest rates prevailing in these economies and changes in US interest rates, even after controlling for domestic macroeconomic conditions and the global business and financial cycle. For short-term interest rates, a 100 basis point change in US rates is associated with an average 34 basis point change in emerging market and small advanced economies (Table V.C, first column). For long-term interest rates, the effect is stronger: a 100 basis point change in the US bond yield is associated with an average 59 basis point change in the yields of these economies (second column). Besides US interest rates, the degree of global investor risk aversion, as measured by the VIX, also consistently emerges as an important driver of these interest rates.
The analysis shows a strong relationship between changes in interest rates prevailing in these economies and changes in US interest rates, even after controlling for domestic macroeconomic conditions and the global business and financial cycle. For short-term interest rates, a 100 basis point change in US rates is associated with an average 34 basis point change in emerging market and small advanced economies (Table V.C, first column). For long-term interest rates, the effect is stronger: a 100 basis point change in the US bond yield is associated with an average 59 basis point change in the yields of these economies (second column). Besides US interest rates, the degree of global investor risk aversion, as measured by the VIX, also consistently emerges as an important driver of these interest rates.
 The analysis shows a strong relationship between changes in interest rates prevailing in these economies and changes in US interest rates, even after controlling for domestic macroeconomic conditions and the global business and financial cycle. For short-term interest rates, a 100 basis point change in US rates is associated with an average 34 basis point change in emerging market and small advanced economies (Table V.C, first column). For long-term interest rates, the effect is stronger: a 100 basis point change in the US bond yield is associated with an average 59 basis point change in the yields of these economies (second column). Besides US interest rates, the degree of global investor risk aversion, as measured by the VIX, also consistently emerges as an important driver of these interest rates.
The analysis shows a strong relationship between changes in interest rates prevailing in these economies and changes in US interest rates, even after controlling for domestic macroeconomic conditions and the global business and financial cycle. For short-term interest rates, a 100 basis point change in US rates is associated with an average 34 basis point change in emerging market and small advanced economies (Table V.C, first column). For long-term interest rates, the effect is stronger: a 100 basis point change in the US bond yield is associated with an average 59 basis point change in the yields of these economies (second column). Besides US interest rates, the degree of global investor risk aversion, as measured by the VIX, also consistently emerges as an important driver of these interest rates.
Furthermore, the persistently low global policy rates relative to Taylor rule-implied levels since the early 2000s (Graph V.3) reflect, at least in part, the effect of low policy rates prevailing in the United States over this period. Specifically, a 100 basis point cut in the US federal funds rate is found to lower EME and other advanced economy policy rates by 43 basis points relative to the levels implied by a standard normative Taylor rule (Table V.C, third column). When estimating a descriptive Taylor rule, the estimated impact of the US policy rate is even higher: some 70 basis points (fourth column). In sum, the results suggest an economically significant causal relationship from US interest rates to interest rates in emerging market and other advanced economies.
Analysis of a broader sample of 62 countries and a more inclusive measure of international capital flows points to a similar dynamic. Here, the larger the net debt inflows, including both portfolio and bank flows, the larger the increase in an economy's ratio of bank credit to GDP (Graph V.4, right-hand panel). The inclusion of Ireland, Spain and the United Kingdom shows that a domestic credit boom's reliance on external financing is not a symptom of financial underdevelopment. In fact, in the subsample of 23 advanced economies the reliance on capital inflows is greater than among EMEs, as the steeper fitted line suggests.
In the second, post-crisis, phase of global liquidity, the term premium on sovereign bonds has become a more important driver of funding conditions. Although cross-border bank credit has continued to expand strongly in EMEs, it has contracted sharply among advanced economies, while bond financing has surged across the board. Even as bond flows have gained prominence, the term premium has emerged as the salient global price of risk in integrated financial markets.
Studies of the spillovers across global bond markets around official large-scale bond purchase announcements have highlighted the strong co-movement of bond yields. If investors treat bonds denominated in different currencies as close substitutes, purchases in one market also depress yields elsewhere. Table V.3 illustrates this point, summarising several studies that estimate the basis point moves in various advanced bond markets that correspond to a 100 basis point move in the US Treasury market. In addition, local currency EME bonds have also co-moved much more closely with Treasuries than a decade ago.6
Heretofore, the relationship across even major bond markets appeared asymmetric, with US bond yields driving those elsewhere, but in the past year this seems to have changed. In particular, there are signs that the euro area bond market has been moving its US counterpart. Anticipation of ECB large-scale bond purchases put downward pressure on French and German bond yields and, through co-movement of term premia, on US bond yields as well, despite the expected divergence in policy rates (Graph V.5, right-hand panel). This contrasts with the experience in early 1994, which epitomises previous patterns. At the time, the Federal Reserve was raising the policy rate while the Bank of France and the Deutsche Bundesbank were reducing theirs, but the backup in US bond yields was transmitted to Europe (Graph V.5, left-hand panel).7
Current concerns
To summarise, the workings of the IMFS post-crisis have spread easy monetary and financial conditions from the reserve currency areas to the rest of the world, just as they did pre-crisis. Global financial conditions have consequently loosened to an extent that may not prove consistent with lasting financial and macroeconomic stability. Credit booms in EMEs and some advanced economies less affected by the crisis have built up tell-tale financial imbalances. In the short run, the IMFS has tilted conditions towards expansion. But in the longer run, financial busts, were they to materialise, would tilt them towards contraction.Monetary policy divergence across key currencies and renewed dollar appreciation pose risks. Ease in the euro area might prolong global ease, if firms and governments around the world can substitute euro funding for dollar funding. However, the large stock of dollar debt outstanding means that a tightening of dollar credit is likely to prove consequential. Thus, renewed dollar strength could expose vulnerabilities (Chapter III), especially in those firms that have collectively borrowed trillions of dollars. Admittedly, it is well known that the US economy has a short position in the dollar that funds a long position in other currencies. And by the same token, the rest of the world must hold more dollar assets than dollar liabilities and thus enjoy valuation gains in aggregate when the dollar appreciates. But even in a country with a long dollar position, the distribution of currency positions across sectors matters greatly for the outcome. For example, in many EMEs the official sector has a long dollar position whereas the corporate sector carries a short one (Box V.D). Absent transfers from the (gaining) official sector to the (losing) corporate sector, the economy may well be hurt by dollar strength.
Dollar strength, monetary policy divergence and heavy official holdings in the global bond market could lead to volatility. Were EMEs to draw down reserves substantially, their selling bonds in the key currencies could create unprecedented cross-currents in global bond markets. ECB and Bank of Japan bond purchases, EME selling and, eventually, the Federal Reserve's not rolling over maturing bonds could confront the remaining private investors with a difficult and shifting problem of bond pricing.
Limits and prospects in international policy coordination
Policies to address the issues raised in this chapter require more than each country managing its inflation and business cycle. A broader notion of keeping one's house in order suggests policymakers deploy monetary, prudential and fiscal policies to manage financial cycles to ensure lasting monetary, financial and macroeconomic stability (Chapters I and IV). The resulting reduction in the frequency and depth of credit booms and busts would greatly reduce negative cross-country spillovers.
Box V.D
Valuation effects of dollar appreciation
This box uses the example of Korea to illustrate that dollar appreciation can deliver wealth gains to non-US residents as a whole, while still representing a tightening of financial conditions for non-US firms that have funded themselves in the dollar. The Korean official sector can gain from dollar appreciation but need not adjust its spending, while the Korean corporate sector can lose net worth and face tighter credit.
It is by now well known that dollar appreciation boosts US net international liabilities. This is because US residents have dollar-denominated liabilities to the rest of the world that exceed their corresponding assets to the tune of 39% of GDP. With the appreciation of the dollar in 2014, the US net international investment position declined from -$5.4 trillion to -$6.9 trillion, as US assets stopped growing in dollar terms despite rising local currency valuations. This $1.5 trillion difference was more than three times the current account of $410 billion. Accordingly, the rest of the world's wealth increased.
This is because US residents have dollar-denominated liabilities to the rest of the world that exceed their corresponding assets to the tune of 39% of GDP. With the appreciation of the dollar in 2014, the US net international investment position declined from -$5.4 trillion to -$6.9 trillion, as US assets stopped growing in dollar terms despite rising local currency valuations. This $1.5 trillion difference was more than three times the current account of $410 billion. Accordingly, the rest of the world's wealth increased.
 This is because US residents have dollar-denominated liabilities to the rest of the world that exceed their corresponding assets to the tune of 39% of GDP. With the appreciation of the dollar in 2014, the US net international investment position declined from -$5.4 trillion to -$6.9 trillion, as US assets stopped growing in dollar terms despite rising local currency valuations. This $1.5 trillion difference was more than three times the current account of $410 billion. Accordingly, the rest of the world's wealth increased.
This is because US residents have dollar-denominated liabilities to the rest of the world that exceed their corresponding assets to the tune of 39% of GDP. With the appreciation of the dollar in 2014, the US net international investment position declined from -$5.4 trillion to -$6.9 trillion, as US assets stopped growing in dollar terms despite rising local currency valuations. This $1.5 trillion difference was more than three times the current account of $410 billion. Accordingly, the rest of the world's wealth increased.
Typical of the rest of the world, Korea's net international investment position as a whole gained from dollar appreciation. Still, Korean firms that have borrowed dollars can still see their net worth fall. Overall, the country's modestly positive ($82 billion in Table V.D) external position shows net foreign currency assets of $719 billion, with over half held by the official sector (official reserve assets of $364 billion) and substantial holdings by institutional investors (portfolio assets of $204 billion). A substantial fraction of portfolio and other foreign currency liabilities ($348 billion), and $65 billion of foreign currency loans booked by banks in Korea, are owed by the corporate sector. Moreover, BIS data show an additional $7 billion of mostly dollar bonds issued by offshore affiliates of Korean non-financial firms, and there is also offshore bank credit. Dollar appreciation leads to official gains that are not conveyed to firms that lose net worth.
Much analysis of international balance sheets, in general, and the insurance afforded by foreign exchange reserve holdings, in particular, implicitly suffers from a fallacy of division, according to which what is true of the whole is true of the parts. In the absence of transfers made when the domestic currency depreciates - which would themselves be fraught with moral hazard - the gains in the public sector do not offset corporate losses. Firms need to adjust their spending and hiring. And if the authorities eventually deploy international reserves to provide dollar liquidity to banks and firms, the intervention may follow disruptions that have already exacted a price.
International policy coordination can occur at various depths. Enlightened self-interest takes international spillovers into account to the extent that they spill back on one's own economy. However, even if countries did their best individually, this would still fall short of the mark if there were significant international spillovers, as in today's era of global liquidity. Moving towards a more efficient outcome would require greater cooperation, including ad hoc joint action, and possibly even agreement on rules of the game that constrain domestic policies.
Obstacles present themselves in terms of both analysis and cooperation. There is the difficulty of agreeing on a diagnosis of what ails the IMFS. And even if a common understanding of international spillovers and their causes emerged, it would remain challenging to forge and to maintain a common approach among multiple actors of varying sizes subject to differing domestic constraints.
Such possibilities and obstacles are evident in the discussion concerning crisis management. During the Great Financial Crisis, central banks proved able to make swift joint adjustments to their policy stances and to coordinate closely in extending foreign exchange swaps to each other. Funding extended under dollar swaps reached almost $600 billion (and, under euro swaps, €6 billion). The dollar swap lines supported financial stability by allowing the funding of foreign banks with limited access to Federal Reserve facilities. In turn, they also restored the monetary transmission mechanism after banks had been bidding up dollar Libor relative to the federal funds rate.
Today, proposals to modify and extend safety nets face obstacles. One reason is deep analytical disagreement. Is reserve accumulation a by-product of exchange rate management, or a form of self-insurance against domestic and external crises? Should international liquidity facilities, including currency swap lines between central banks, be broadened, and what is their best design? Would enhanced safety nets lead to smaller foreign exchange reserves? And, even if agreement were reached, many aspects of international risk-sharing would remain problematic. Despite the room for improvement, the status quo may well persist.
All this reinforces the case for crisis prevention. Here, central banks could seek to internalise the effects of their own policies. An improved exchange of information would help authorities to reach a better understanding of international spillovers and spillbacks. For instance, if the major central banks' monetary policies have indeed induced competitive easing among EMEs, the resulting financial imbalances may ultimately hurt the advanced economies. What is more, such spillbacks may be stronger than in the past, in line with EMEs' growing weight in the world economy (Chapter III). Similarly, the outsize official role in major bond markets points to the need for policymakers to pay attention to global effects. However, while global reserve managers might collectively benefit from taking into account the effect of their investment behaviour on global bond yields, their individual incentive is to ignore international spillovers.
Box V.E
Consolidating the US external balance sheet
Much of international macroeconomics assumes that national borders delimit currency zones and decision-making units. Just as the national accounts do, it assumes that those borders define the relevant economic territory: different currencies do not compete within a given country and firms operate exclusively within national borders. In reality, neither is the case. Not only does the domain of major currencies extend outside their country of issue (Boxes V.A and V.B), but multinational firms, be they financial or non-financial, operate across borders. Management focuses on group-wide profits and risks, and balance sheets span national boundaries. A consolidated perspective better reflects the reach of multinational firms and the extent of global integration.
This box uses the US example to illustrate how such a consolidated view of foreign assets and liabilities differs from the official international investment position (IIP) recorded on a residence basis - the defining criterion of the national accounts and balance of payment statistics. These are denoted "locational" in the first two columns of Table V.E. The process of consolidation aligns balance sheets with the nationality of ownership rather than with the location where the assets and liabilities are booked. This amounts to redrawing the US border to include the foreign balance sheets of US-owned firms, and to exclude the US balance sheets of foreign firms. This consolidation is performed here for the banking sector and the non-bank business sector (multinational companies).
The first step replaces the banks' external positions with consolidated BIS data (three rows under "bank-reported" in Table V.E). This removes all cross-border claims of, say, BNP Paribas New York on the rest of the world (these being French assets), and adds JPMorgan's consolidated foreign claims, yielding a total of $3.330 trillion for reporting US banks combined. Similarly, on the liabilities side, out goes any cross-border liability of BNP Paribas New York, and in comes JPMorgan's global foreign liabilities, to give an estimated $2.958 trillion for US banks. Moreover, foreign banks' local operations in the United States, which are not part of the US external position, further add to US consolidated assets and liabilities, respectively, to the extent that US residents provide funding ($2.465 trillion) to, or receive credit ($3.150 trillion) from, the US offices of foreign banks. Consolidating banks raises the sum of US foreign assets and liabilities from $40 trillion (IIP) to $45 trillion.
The second step consolidates foreign-owned multinational companies (excluding banks) in an analogous, though coarser, way (owing to data limitations). The cross-border direct investment positions of non-banks, assets and liabilities, are replaced by the (larger) total assets of US multinationals outside the United States and by those of foreign multinationals in the United States, respectively (rows under "direct investment" in Table V.E). Out goes General Electric's equity position in its French subsidiary, and in comes that subsidiary's total assets, resulting in $20,250 billion for all US-owned multinationals combined. These assets exceed the corresponding ownership claims (consisting of $5,078 billion worth of equity and equity-like inter-affiliate debt in the IIP) because US multinationals also borrow abroad; these liabilities (an estimated $15,173 billion) in turn add to US foreign liabilities. As for foreign multinationals, French firm Total's stake in its US subsidiary is removed, and its US assets are added - yielding $9,920 billion for foreign multinationals. Foreign multinationals' liabilities ($6,863 billion) count as a US foreign asset. This step sextuples directly held corporate assets and liabilities, but leaves US net assets unchanged.
Together, consolidating banks and multinational companies more than doubles the gross foreign position of the United States. US external assets and liabilities combined jump from $40 trillion on a residence basis (IIP) to an estimated $89 trillion when measured on a consolidated basis. The example reveals that the US economy is more open, and its foreign balance sheet larger, than is apparent from the external position derived from the balance of payments. The calculation of the US current account, on the other hand, should not be affected by consolidation, since foreign earnings are included in net investment income whether they are repatriated or not.
This interpretation of domestic mandates contrasts sharply with successful international cooperation in the realm of financial regulation and supervision. There, national mandates have not precluded extensive international cooperation and the development of global rules.
A better understanding of the shortcomings of the current IMFS would already be a big step forward. A widely held view is that the main problem is the IMFS's apparent inability to prevent large current account imbalances. This view of imbalances is the prevailing one in international forums and implies specific adjustment policies, such as those associated with the G20 Mutual Assessment Process.9
The focus on current accounts and the corresponding net resource flows, however, arguably glosses over the IMFS's fundamental weakness. The aim of rebalancing global demand reduces the notion of imbalances to net flows in goods and services between countries, and neglects the greater risk of financial imbalances building up within and across countries. To be sure, large current account deficits often point to underlying problems, but financial booms and busts can and do develop in surplus countries as well. An aggregate surplus position may well conceal such vulnerabilities. Financial imbalances are more closely linked to domestic and international gross positions, and need not leave a mark on cross-border net flows - what current accounts represent.10 Indeed, financial imbalances may not show up in a country's balance of payments at all if multinationals issue debt offshore for their use abroad, for instance. This, in turn, raises the question of the appropriate unit of analysis in international finance, with consequences for how one should measure the risks (Box V.E). Making progress on the design of the IMFS thus calls for a new diagnosis that accounts for financial imbalances as a basis for broad adjustments to domestic policy regimes and their international interaction.
About international banking statistics
The BIS compiles and publishes two sets of statistics on international banking activity - locational and consolidated banking statistics. Both sets are collected under the auspices of the Committee on the Global Financial System and reported to the BIS at a country, rather than individual bank, level.
View our release calendar for advance notice of publication dates.
Our data
- Locational banking statisticsThese statistics provide information about the currency composition of banks' balance sheets and the geographical breakdown of their counterparties. They capture outstanding claims and liabilities of banks located in BIS reporting countries, including intragroup positions between offices of the same banking group. The locational statistics are compiled following principles that are consistent with balance of payments. Adjusted changes in amounts outstanding are calculated, as an approximation for flows.
- Consolidated banking statistics
These statistics measure banks' country risk exposures. They capture the worldwide consolidated claims of internationally active banks headquartered in BIS reporting countries. The consolidated statistics include the claims of banks' foreign affiliates but exclude intragroup positions, similarly to the consolidation approach followed by banking supervisors. They detail the transfer of credit risk from the immediate counterparty to the country of ultimate risk (where the guarantor of a claim resides).
Research and analysis
Developments in the latest international banking statistics, including breaks in series, are summarised in a quarterly statistical commentary. The statistics are also analysed in the Highlights section of the BIS Quarterly Review and in research papers.Publication dates
The international banking statistics are published quarterly in January, April, July and October, with a lag of about 16 weeks. Revised data are published in March, June, September and December, concurrently with the BIS Quarterly Review.View our release calendar for advance notice of publication dates.
Reporting guidelines
The Guidelines for reporting the BIS international banking statistics provide definitions and requirements for reporting locational and consolidated banking statistics. The consistency of reporting practices with the Guidelines varies across reporting countries, and key discrepancies are highlighted in countries' summaries of their banks' reporting practices.
Monetary and financial stability: Here to stay?
We argue that changes in the monetary and financial regimes over the last twenty years or so have been subtly altering the dynamics of the economy and hence the challenges that monetary and prudential authorities face. In particular, the current environment may be more vulnerable to the occasional build up of financial imbalances, i.e. over-extensions in (private sector) balance sheets, which herald economic weakness and unwelcome disinflation down the road, as they unwind. As a result, achieving simultaneous monetary and financial stability in a lasting way may call for refinements to current monetary and prudential policy frameworks. These refinements would entail a firmer long-term focus, greater symmetry in policy responses between upswings and downswings, with greater attention to actions during upswings, and closer coordination between monetary and prudential authorities
XXX . V000000000000 Shaping the Future of Financial and Monetary Systems
How can the global financial system reinforce its contribution to sustained economic growth and social development?
The global financial system is the cornerstone of economic activity, which is critical for long-term economic growth and development. However, the global financial crisis demonstrated the downside of interconnectedness and revealed a range of systemic vulnerabilities.
As the global financial system recovers, major collaborative efforts are required to rebuild public trust, respond to regulatory and technological change and overcome barriers to financial inclusion. The World Economic Forum’s System Initiative on Shaping the Future of Financial and Monetary Systems aims to build a more efficient, resilient and equitable international system by: enhancing financial stability, innovation and economic growth by analysing the implications of industry transformation in an effort to better understand the competitive, human capital, and regulatory dynamics that will exist in the financial sector of the future; promoting global financial inclusion through a portfolio of in-country impact projects, identifying the highest potential opportunities to increase access to quality, affordable financial services for the unserved and underserved; and better understanding disruptive innovation in financial services by exploring how innovations are changing business models and restructuring ecosystems in specific areas of financial services.
The Future of AI & Automation in the Financial and Monetary System
Across the financial and monetary system organizations find themselves in the challenging position of being asked to do more with less. Financial intuitions face an imperative to cut costs in the face of a challenging macroeconomic environment and new regulations while simultaneously attempting to expanded services to compete with “fintech” new entrants. Many of their regulators and supervisors are little better off – having had their mandates but not their budgets expanded in the years following the global financial crisis they face a serious set of operational challenges.
Automation enabled by advanced technologies like machine learning and AI present an enticing solution to these challenges. However, understanding the opportunities for and potential implications of increased automation in the financial and monetary system remain heavily siloed. Absent an initiative that convenes the necessary experts and strategists to comprehensively map this transformation we risk encountering unintended consequences for systemic stability and broader economic growth. This project will seek to identify high potential opportunities for automation across the system, understand their implications, and having identified potential governance gaps, catalyse joint public/private implementation of automation best practices.
= MA THEO RULER ACQUISITION FINTECH ELECTRONIC TRANSACTION IC MATIC =




























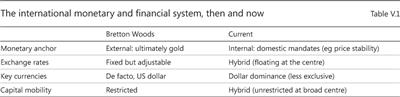
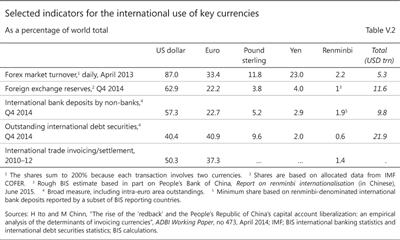
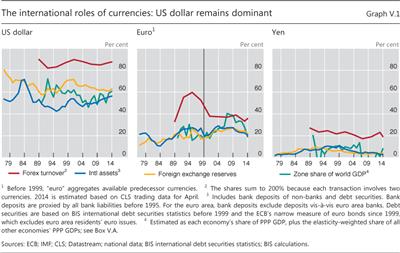
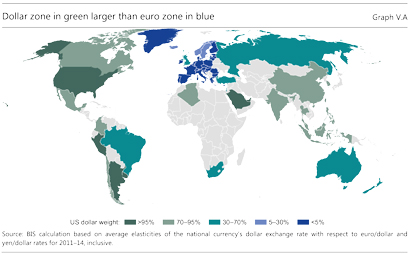
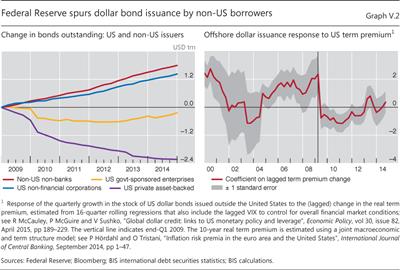
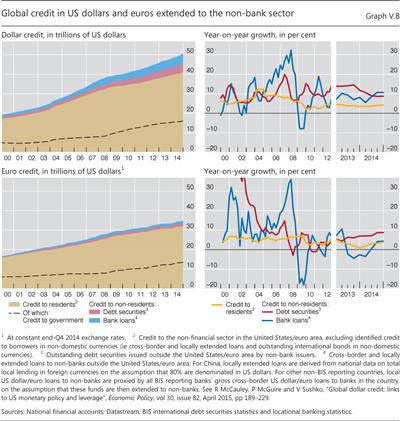
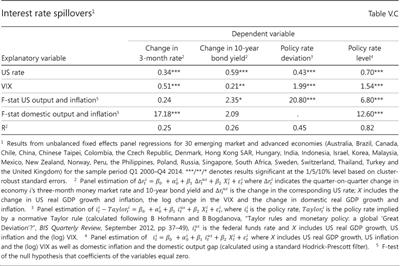
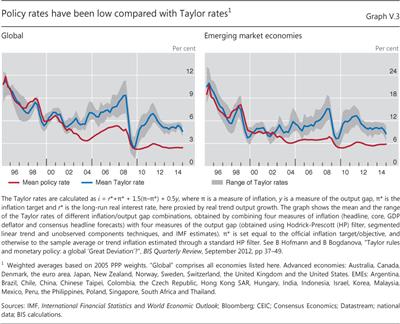
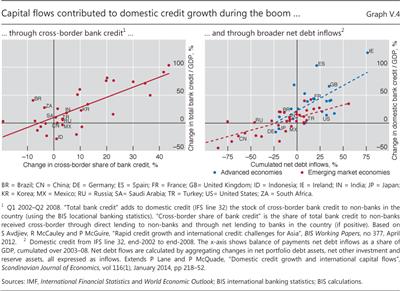
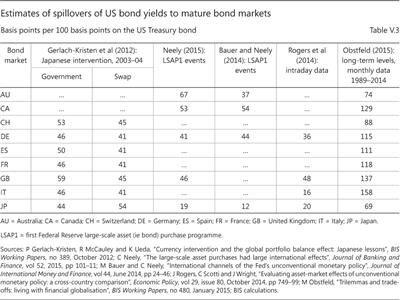
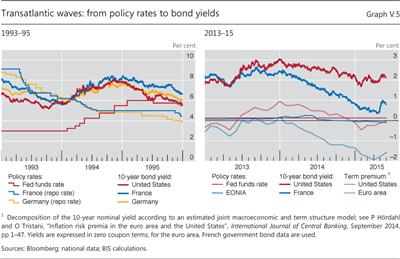
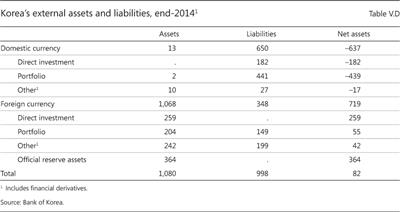
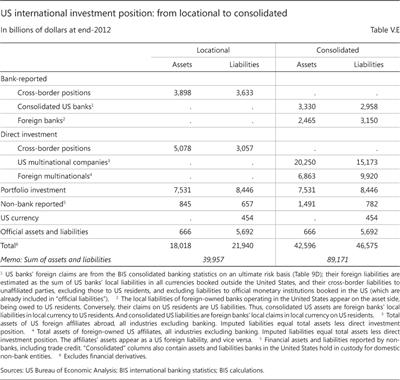
Tidak ada komentar:
Posting Komentar