Minggu, 26 September 2021
Amnimarjeslow Governor track record 91220017 Algoritme on Power Secure Think to be Monitoring and Controlling time to set up ; Thankyume with lock book for keeping human electronic machine interface by spirit
Problem solving in monitoring and controlling especially electronic machine access control and communication ROBOT IC Hertz is much influenced by time adjustments in the real dimensions of space and time as well as passing through many dimensional through hole points, at least we will involve the following stages:
1. Analysis of dimensional and time problems, 2. designing algorithms,
3. Making Baby IOXT program ,
4. coding , debugging , documentation ,
5. SMART = Specific → clear financial goals
Measurable → can be measured nominally
Achievable → possible to achieve
Realistic → according to financial ability
Timely → there is a time period
6. definite
7. The Produce output
8. sistematic and structure to do Power life
9. The algoritme can be stop processing
10.eficiency and accurate algoritme methode .
let's review the tools needed for the process
let's review the tools needed for the process
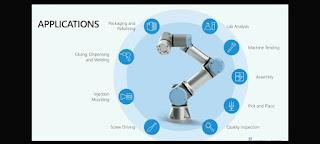
Algorithm, examples of some software methods in a block chain: 1. operating system software, 2. programming language software, 3. application software. Operating system software is developed with the main objective of controlling electronic computer interface devices when the system process is running, programming language software is developed as a tool for developing application programs that suit user needs, while application software is application software intended for specific purposes. development application.
The 21'st Century of baby IOXT Gate
+++++++++++++++++++++++++++++++++++++++
The key building blocks of any IoT structure are always the same, namely:
smart things;networks and gateways enabling low-power devices (which is often the case in IoT) to enter the big Internet;the middleware or IoT platforms providing data storage spaces and advanced computing engines along with analytical capabilities; andapplications, allowing end users to benefit from IoT and manipulate the physical world.
These elements make up the backbone of any IoT system upon which effective, multi-layered architecture can be developed. Most commonly, these layers are:
1. the perception layer hosting smart things
2. the connectivity or transport layer transferring data from the physical layer to the cloud and vice versa via networks and gateways;
3. the processing layer employing IoT platforms to accumulate and manage all data streams;
4. the application layer delivering solutions like analytics, reporting, and device control to end users.
Besides the most essential components, the we also describes three additional layers:
the edge or fog computing layer performing data preprocessing close to the edge, where IoT things collect new information.
1. Typically, edgy computing occurs on gateways;
2. the business layer where businesses make decisions based on the data;
3. the security layer .encompassing all other layers.
Often viewed as optional, these extra components none the less make an IoT project neatly fit modern business needs for startup algoritme . we describes and explain for informix mwthode .
The problem solving process consists of ten main steps, namely: 1. the start of a process, 2. reading the input data of the process, 3. The problem solving process, 4. Printing the results of processing / information, 5. the end of the problem process, 6. feedback, 7 continual improvement, 8. standard setting, 9. development of appropriate standards in time, 10. safety and good application
$$$$$
There are 4 analyzes that I will apply in the application of algorithm problems or it can be said AMNIMARJESLOW AL do Four do AL one:
1. Analysis of algorithms in situations,
2. Analysis of algorithms in a problem,
3. Analysis of decision-making algorithms
4. Analysis of algorithms for potential problems and reaction action.
The problem in the Algorithm is an action that is stimulated by a causal diagram of standard deviations, deviations from normality, deviations from what should be, the existence of deviations encouraging algorithm actions to draw causes in the link and match process, by looking for causes that make deviations that are specific and real , historical and real .
A time setup algorithm must be right on target and the target is absolute, that is, it leads to a decision goal with measurable conditions and is Go To , IF .. Then , Until .. Do . the target is also USER 's desire , namely by weighing by considering what are the adverse consequences or deviations from the standard , where every job is in the form of IPOT ( Input _ Processing _ Output _ Time Setup ) . Algorithm problems should not be drawn conclusions or opinions but by looking at the deviations that occur, seeing changes that are relevant to the consequences, differences that arise, stating in facts or not facts.
we need appreciation of simplicity algorhitme process of Baby IOXT in the electronic machine learning as like as instrument time setup for need processing export and import in goods and service using Baby IOTX .
Detection of system Problems :
all information systems will have problems , regardless of how well the system is designed . several things that cause the information system to have problems , among others as follows ;
1. Over time,
2. Changed system environment,
3. Changes in standard operating procedures, 4. The development of the Internet of things and secure things.
repair of information system problems is called maintenance programming , which includes responding to system problems and adding new tasks , subjects and functions to modern electronic machine systems . Information system problems are always related to the characteristics of information, namely as follows:
a. relevance,
b. Completeness,
c. Correctness,
d. password access and security ,
e. Timeliness,
f. technical economics,
g. Efficiency,
i. Reliability,
j. Usability.
an analysis model based on electronic machines must be based on user needs including:
1. establishing a basis for making software design,
2. limiting the set of requirements that can be validated once the software is built.
3. hardware production using electronic machines integrated with Baby IOXT. Previously I will describe how the development of types of machines from human civilization: 1. the era of machines with animal power or ancient industry,
2. the era of mechanical machines, where using mechanical machine tools such as catapults, pulleys, saws, axes and others, industrial ladders 2 ,
3. the era of electric machines , namely using electric machines such as generators and dynamos as well as AC and DC motors commonly called the third ladder industry ,
4 . the industrial era of electronic machines, namely modern civilization today such as television, cell phone, fax, satellite, satellite dish, computers, printers, sophisticated aircraft with electronic warfare control, radar, internet, artificial intelligence and others, is currently called the 4th ladder industry.
Expected improvements in system development on electronic machines:
1. Performance (performance),
2. Information,
3. Economy technic
4. Instrumentation and Control power system management,
5. Efficiency and effectiveness and quality, 6. Good Services and High fidelity performance
7. feedback fast response , accurate , and smart .
Communication between modules or block diagrams follows several stages:
1. Modular electronics machine Programming Concepts
2. Communication between modules
3. Cohesion
4. Clutch,
Modularization or block diagrams or process diagrams are used when there is a
complex problems, so the first step is to identify the main task, after that it will be divided into more detailed tasks.
This process is also known as Top Down design.
MODULAR PROGRAMMING
Breaking algorithms into more algorithms
small/module.
The formed module has a unified task/function
as well as the unity of the process/procedure.
Each module must have a single entry and a single
exit consecutively from top to bottom or from the beginning
to the end of the module block diagram settings
Have main program and sub program or module.
Six steps in the modular process:
1. Problem definition: classify in input, process
and output
2. Group activities into modules. Define
activities of the existing compiled electronic block diagram modules
3. Create a stacking chart to explain the hierarchy and
connection between electronic machine modules
4. Create logic from the main program with pseudocode and electronic machine interface instructions.
First take an inventory of what is done
in play program
5. Create logic for each module with pseudocode and matching software and hardware instructions.
6. Desk checking algorithm: checking the correctness of the algorithm with IPOT data [Input, Process, Output and Time Setup]
For example, the communication system between the electronic engine engine modules is the communication of several electronic engine devices via satellite. channel access system , namely the ability to transmit information multi - destination , to a large number of geographically dispersed electronic machine information users . the method of transmitting information together , through the same resource in a network , is called the multiple access technique . if a resource is a transponder from a satellite, the full or partial use of that transponder, by geographically dispersed earth stations. even the current developments for transmitting information in terrestrial transmission systems. In the satellite communication system, one must look at how to accommodate information, namely frequency or bandwidth, time and space, and energy.
Satellite communications (SATCOM) are already today an important component of aeronautical communications, in particular for the oceanic airspace. In the future, SATCOM is expected to be equally important also for the continental airspace and become an integral part at instrument and controlling of electronic machines module in the Future Communications Infrastructure (FCI). In addition, evolving satellite constellations provide new SATCOM systems offering new capabilities to meet the current and future aviation communication needs.
Data communication between electronic machine modules
**----------------------------------------**
when electronic machine modules communicate with each other both hardware and software and infoware such as computers communicate with smart phones and then communicate with robotics, satellites, program control, satellite dishes, printers, indicators, drones and others. data and information communication between these modules will cause a number of problems to be resolved . There are several different forms of data in electronic machine modules such as computers such as simple text, formatted text, graphics, sound, files created by data collection techniques, certain application programs, and the programs themselves. electronic machine module module equipment varies greatly, if these modules must and will communicate with each other, it is very important to use common security and convenience standards such as file or data transfer protocols, protocols are agreed ways to do things properly . So if the electronic engine modules have to communicate with each other they have to follow many protocols. let's take a look at some of the protocols that have ever existed in the world of electronic machines module equipment :
1. XModem / CRC protocol,
2. YModem protocol,
3. ZModem protocol,
4. Sentinel protocol,
5. Kermit protocol,
6. Internet protocol,
7. SLIP protocol.
The ON-LINE Algorithm process on electronic machines uses the Baby IOXT network:
___________________________________________
Uniting Hardware and Software is only the first stage in setting up the terminal , then the selection of communication software and connection with an internet provider that will connect electronic machines to each other with Baby IOXT. communication software is one of the most important for electronic engine module module communication so that the Baby IOXT ON-LINE process can provide access to all facilities. communication software is software to carry out tasks and functions of electronic machine hardware functions that interact with each other in the Baby IOXT line. some good and true in the ON-Line Baby IOXT process; 1. Communication Software, 2. Protocol, 3. Interface, 4. Terminal, 5. Transfer Settings, 6. Memory hardware, 7. Hyper Terminal, 8. Electronic data buffer, 9. Communication network: edge, 2G, 3G, 4G , 5G and the latest 6G where the GPS Locater process is precise, fast, efficient and SMART.
10. Packet Driver and Drift .
Baby IoT Information Communication Technology (ICT) is a breakthrough in human to human, human to things and things to things transmission of information. Smart devices are now able to connect, move, and make decisions on behalf of individuals, this technology is also termed as “connectivity for anything”. IoT ecosystem consists of many smart devices that can be connected amongst each other anywhere and anytime. However, constraints such as storage volume, radio range, and power are hindering the IoT growth and need the communication protocol to manage these constraints.
Top IoT Communication Protocol
Many wireless technologies are available today that are being used to interconnect IoT devices and the internet, consisting of various ranges WPAN and WLAN such as Wi-Fi, Infrared, Bluetooth, Bee, M-bus, etc. The communication protocols can be broadly classified into Wi-Fi, Bluetooth, Satellite, NFC, and RFID standards.
Here we discuss the top 4 IoT communication protocols:
1. WiFi
For many developers, Wi-Fi connectivity is often an obvious choice, particularly given the pervasiveness of Wi-Fi within the LAN home environment. It’s a local area network that makes use of IEE 802.11 standards in a range of 5Ghz ISM frequency wavelength. Wi-Fi is short-range technology and provides a range of about 60 feet from an access point.
Wi-Fi is a wireless protocol designed to replace Ethernet with wireless means. Its goal was to provide cross-seller interoperability with off-the-shelf, easy-to-implement, easy to use short-range wireless connectivity.
Standard Wi-Fi is often not the best IoT technology, but some IoT applications can leverage standard Wi-Fi-enabled, particularly for in-build or campus environments. Obvious cases include building and home automation as well as in-house energy management, where Wi-Fi can be used as the communication channel and the devices can be connected to electrical outlets.
On the other hand, Wi-Fi 802.11ah also called “HaLow” is specially designed for IoT and requires unique clients and infrastructure. Vendors of Wi-Fi technologies continue to improve and are trying to provide better technology every day.
2. Satellite Communications
Satellite communications allow mobile phones to communicate with the nearest antenna of about 10-15-mile. These are referred to as GSM, GPRS / GSM, 3G, 4G / LTE, 5G, and others depending on the speed of communication. Satellite communication is also referred to as Machine to Machine communication in IoT as it allows communication between mobile devices.
Custom-designed satellite communication appears to be the only feasible solution to the communication limitation that is the wide-scale interconnection of IoT devices. Satellite technology could help the IoT sector grow and handle this wide-ranging connectivity challenge easily.
The speed of data transfer could prove to be a concern for such high loads. Nevertheless, it is only a matter of time before the advent of innovative solutions.
Satellite providers are already partnering together to deliver services and equipment capable of unleashing IoT’s full potential. A solution is being already worked upon to integrate fiber, satellite, and wireless networks. The global nature of satellite systems and the ability to simultaneously broadcast to multiple points make it the most effective signal delivery on Earth. In order to achieve global coverage, satellite transmission tag along with terrestrial networks.
3. Bluetooth
Bluetooth technology has come a long way since its invention in the year 1994 by Ericsson. Bluetooth was developed as an alternative for standard RS cables which were then being used for connecting external devices to PC. Bluetooth is used in IoT for keeping track of equipment in commercial, educational, or health care sectors. Bluetooth applications are very effective for indoor tracking scenarios which have lower power requirements. Bluetooth connectivity, however, falls under short-range connectivity and doesn’t support transmission or track underwater. Moreover, Bluetooth connectivity is further not advised for security solutions that require visual or audio information to be transmitted over the network
Launched in 2009, Low-Energy Bluetooth created the opportunity for IoT to utilize Bluetooth as a medium of communication. BLE is a standard that specifically addresses small-scale IoT implementations such as wearables and beacons which allow devices to send small amounts of data using minimal power. The roles and uses of Bluetooth in cars and homes are going to continue to grow and expand. Imagine receiving automatic traffic updates or weather reports on your dashboard during your daily commute or home automation scripting using Bluetooth to set up lighting, thermostat, and home theater systems for the perfect mood or occasion is not farfetched.
4. NFC and RFID
NFC technology was initially originated from Radio Frequency technology (RFID) which encodes and reads the information using electromagnetic fields. Every NFC-enabled device is equipped with a small chip that is activated when it comes close to another NFC chip (10 cm range). Consequently, NFC allows for simple and safe interactions between electronic devices. NFC devices can be further classified into active and passive devices. Active devices include mobile devices that are capable enough to send and receive information. On the contrary, passive devices can transmit information and are not equipped to read information themselves. NFC technology can be embedded for multiple benefits like performing contactless transactions, connecting devices with a tap, downloading digital content with high speed, and providing security system credentials. With a single tap, two different IoT devices can be simply connected with NFC. NFC technology has built-in security features such as encryption to prevent any potential hack. Further, the short-range NFC acts as a shield and protects against hackers.
Radio-frequency identification (RFID) is a method of communication used for wireless tracking and identification of objects. It is one of the simplest methods of communication and is being used in the majority of IoT ecosystems. It is not only used to track consumer products around the world, but also to track toll collection vehicles. It is used by hospitals to track their patients and by farmers to track their animals. RFID tags are the advancement of traditional bar codes and have the capability to read and write the data.
______________________________________________
module machine electronic joint to joint
*******************************************
*AMNIMARJESLOW 2002*
Networking , Flow Chart , Algorithm
Function pair to Pair at Mathematic
Program Design
++++++++++++++++++++++++++++++++++++++++
requirements for the purity of a network, flow chart, pair of algorithm functions that can be applied to the design of IPOT mathematics electronics programs and technical economics: 1. IPOT network must be stable; 2. the stability of the appropriate IPOT network relativity; 3. IPOT network attenuation and response are feasible and quite accurate; 4. IPOT network system must be able to reduce errors to zero or to a value that can be tolerated; 5. there is a match in the IPOT network at a reasonable relative stability with a fast response condition accuracy that can be met at the same time; 6. IPOT networks must be able to detect places and positions using Baby IOXT such as 5G and 6G, 7G networks in GPS which use vector matrix analysis that is directly proportional to the time domain; 7. IPOT network can control multiple inputs and multiple outputs; 8. IPOT network can be made with the mathematical electronics model and the technical economic model; 10 . IPOT network should and may be simulated in network engineering using both hardware, software and infoware based on the electronic human interface brainware.
IPOT meaning : ( Input_Proces_Output_Time SetUP )
☆☆☆
I call the EINSTEIN protocol (EINSTEIN meaning Energy _Intern_Saucer Tech_Energy Input) protocol during the operational time of the electronic machines joint to joint networking network. EINSTEIN protocol is optimum Network Protocol with maximum integrated network engineering. the EINSTEIN protocol system applied to the IPOT network is used using the Baby IOXT on line network. Direct inspection of the spacecraft's network system must have the performance possible at the minimum time using the minimum fuel at the time most appropriate for the circumstances under the circumstances, conditions, tolerances, visibility and range of space and time in which the spacecraft is located.
Network electronic Machines Joint to Joint
by managimg a network by using
techniques the perfect time to synchronize
Hardware , Software , Infoware and Brainware
(Brainware as like as Baby IOXT,AI , ML , DL )
$$$$$$$$************************$$$$$$$$
network electronic machines joint to joint design and implementation , we need to know !! and we must to know how to troubleshoot problem when network arise . we must also to know how to maintain the network and keep it functioning at an acceptable level . in addition , we must to know when it is necessary to expand or change the network's configuration in order to meet the changing demands placed on it . managing network electronics machine joint to joint , it mus be and should be .
let,s go to come on elctronic instrument
joint to joint
========================================
Vlad_i_vo_stock in electronic joint module
₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩₩
Situation analysis in the mathematical electronics program is algorithmic: Happy is the person who solves the problem gently, which means to solve the problem specifically, because by solving the problem of specific algorithmic electronics the problem becomes clearer which means that it has been partially solved. then what if the control problem of the algorithm is complex and not ready to be solved at this time, we don't need to be confused with so many electronic algorithms that we make, we have to solve complex problems with ;; 1. Separating electronic algorithms into joint electronics modules connected to a single algorithm is useful for viewing systematic deviations, formulating formulas, and sometimes algorithms can be framed with each other. 2. do the priority scale of the connected electronics module algorithm, some consideration of the order of priority problems seen from the urgency, urgency in the program, the trend of program development. 3. locating a position so that we can determine a suitable process to complete it by reviewing the best alternative programming languages, namely hardware, software, brainware, and infoware languages.
Analysis of differences and changes in an electronic module that is connected to each other either by close control or remote control using the EINSTEIN protocol programming language: 1. Control is a standard or normalization of a system while the problem is a deviation from the standard or in other words an EINSTEIN protocol is problem + deviation + deviation = standard - reality .
Among the information available in the joint to joint electronic module programming algorithm we look for or detect various changes or deltas or differentiations or derivatives or timers that occur in the difference area. Changes can occur from influences within the electronic module or external influences from the electronic module system that we joint to joint, both in Artificial intelligence and Smart devices. let 's examine what is change , change is an event that arises or appears more or less at the time the deviation begins . change is dynamic , it happens !! , change is an event and occurs more or less at the same time as the start of the deviation . while the difference is a condition that existed before the deviation began. difference is static , difference is state , difference is exists , and existed before the deviation started . on the time dimension , the difference coincides with the change , in other words the difference between the two periods is nothing but change as well . The tendency of the integrated electronics module algorithm is for a moment, that is, don't look and look for changes in the time dimension or signal frequency, but just look for differences. Basically it can be said that the dimensions of time and frequency are neutral in a main task and function so they are colorless, things that exist or happen are always dilated to the dimensions of What, Where, and area and position are never interconnected dimensions but to make it easier for us. say as " time " only , so that we can get the real result of the algorithm program the most possible . On a network basis, we can explain that fact and time are power and control that explains the problem with the most likely problem limits on the timer and actuator and indicators.
technical specifications on an electronic network algorithm problem: 1. Eternal Problem, this problem is a long-standing or "eternal" problem that has existed since its inception (start up problems), or can we say when it started?? I don't know, what we might do is reduce the eternal peculiarities so that we can make standards, deviations and realities. 2. Problems Humans as technical users, humans see algorithmic language programs are often colored with prejudice, sentiment, so that often only symptoms or consequences are visible, while the real causes are hidden in the hearts of the people concerned. so from that symptom alone we have to guess the cause !! . considering the difficulties mentioned above , it is clear that in the " human problem " as a technical user more assumptions are needed than the technical and physical problems themselves . So in the case of humans, the adjustment is to adaptation actions, namely accepting deviations or reducing the consequences of deviations even though the causes are still affected.
so in the case of humans we must be good at predicting the possible causes, especially the very high probability causes. there are several actions that can be taken for problems that can be created by human problems: 1. preventive measures aimed at reducing the possibility of causing causes; 2. precautionary measures aimed at reducing and eliminating deviations if this occurs, usually in the electronic module module algorithm using SMART electronic controls such as AI, ML, DL, CV. finally we control the precautions provided such as the use of standard Baby IOXT.
$$$$$$Vlad$$$$$i$$$$vo$$$$stock$$$$$$$
Entertainment_Professional_Start Up
__________________________________
Sun_showing to sand_strategic_look that
BALI DANCE to be Call :: Marga_pati dance
_________________________________________
28 November 2021 ubud _ gianyar
Melas_Ati Beach ( 29 November 2021 )
Rai_ning ... so far so good
___________***____________
Off_Ice to be Rain $$$ life is mining
========== $$ ==========
Langganan:
Postingan (Atom)